A recently discovered vulnerability in the AWS Systems Manager (SSM) Agent, a cornerstone of Amazon Web Services (AWS) used for managing EC2 instances and on-premises servers, has raised critical security concerns.
This security flaw, identified as a Path Traversal vulnerability, allows attackers to execute malicious code with root privileges, potentially leading to privilege escalation and unauthorized access to sensitive systems.
Understanding the Vulnerability
According to the Cymulate report, the issue originates from insufficient input validation in the ValidatePluginId function located in the pluginutil.go file of the SSM Agent.
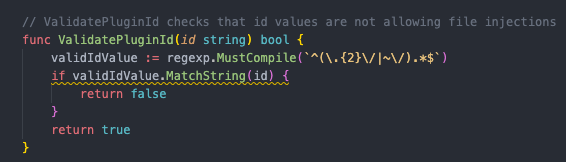
This function is responsible for checking and validating plugin IDs specified in SSM Documents—JSON or YAML-based templates that define tasks to configure or manage systems.
Improper sanitization of the plugin IDs enables attackers to include malicious path traversal sequences (such as ../) to manipulate the file system.
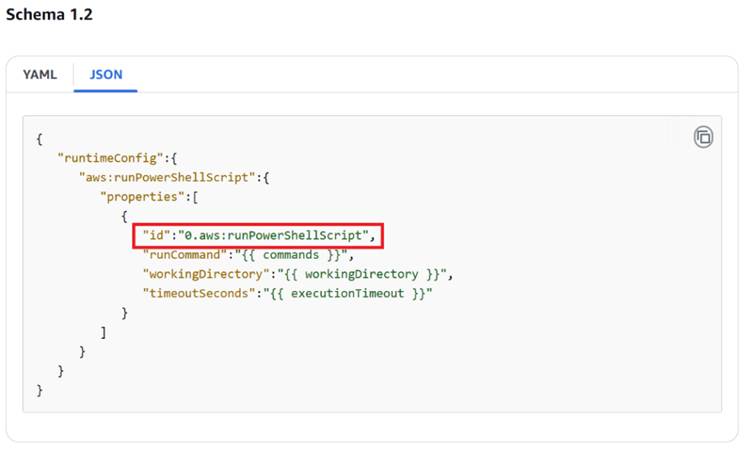
When an SSM Document is executed, the SSM Agent dynamically creates directories named after the plugin ID and executes scripts within them using root privileges.
Due to flawed validation, attackers can craft a malicious plugin ID that directs the agent to create unintended directories and execute commands outside the expected secure locations.
For instance, this could result in scripts being executed in sensitive areas such as /tmp/.
Technical Breakdown
- Key Component: The flaw exists in the AWS SSM Agent, specifically in the ValidatePluginId function.
- Repository: AWS SSM Agent GitHub Repository (source).
- Vulnerable Versions: All currently released versions of the SSM Agent.
The vulnerability permits attackers to utilize a crafted plugin ID when creating an SSM Document. This input is processed by the SSM Agent to create directories and files in unintended locations.

For example, if the plugin ID contains ../../../../../malicious_directory, the agent interprets this input as a directive to create directories outside its intended scope.
As a result, files such as _script.sh can be executed in arbitrary locations with elevated privileges.
Successful exploitation could enable attackers to:
- Create directories in restricted or sensitive locations.
- Execute arbitrary commands or scripts with root-level access.
- Potentially escalate privileges to gain full control over the compromised instance.
Steps to Reproduce the Exploit
- Create a Malicious SSM Document: Use a plugin ID containing path traversal sequences (e.g., ../../tmp/malicious_directory).
- Upload the Document: Submit it to AWS using the Management Console, CLI, or SDK.
- Execute the Document: Trigger execution via the SSM Agent.
- Verify Results: Check the filesystem for unintended directory creation and note the execution of _script.sh in these locations.
Mitigation and Recommendations
AWS should take immediate action to address this vulnerability by:
- Enhancing Input Validation: Update the ValidatePluginId function to rigorously sanitize inputs, rejecting special characters such as ../ to eliminate path traversal risks.
- Security Patching: Release an updated version of the SSM Agent with these fixes.
- User Awareness: Notify AWS customers to update their SSM Agents and audit their systems for signs of exploitation.
This vulnerability underscores the importance of input validation in preventing exploitation.
Organizations using AWS Systems Manager should remain vigilant, apply security updates promptly, and monitor their systems closely to mitigate potential risks.
At the time of writing, AWS has yet to release a patch, but swift action is anticipated to safeguard its users and infrastructure.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
