Largest underground store “BriansClub,” for buying stolen credit cards got hacked, over 26 million credit and debit card data extracted from the underground store.
BriansClub found to be sold more than 9.1 million stolen credit cards and the store earned more $126 million according to the KrebsOnSecurity report. Brian Kerbs also complains that the website is using his popularity and even his image on their ads to carry out their activities.
The plain text data that contains payment card data shared to KrebsOnSecurity, the data includes the one available for sale at BriansClub[.]at and the historical data.
Multiple analysis of the payment card data reveals that the same card data has been shared with multiple sources and anyone can BriansClub Web site account can retrieve the data.
The exposed data contains credit card data starting from 2015 to 2019.
- 2015 BriansClub added 1.7 million cards
- 2016 BrainsClud added 2.89 million cards
- 2017 Around 4.9 million cards
- 2018 holds 9.2 million cards
- Between January and August 2019 7.6 million cards
The data offered by the BriansClub are mostly dumps, which contains ones and zeros when these data are written in the magnetic stripe, they are used by criminals for making payments.
The below table shows the market value of the cards in dark markets.
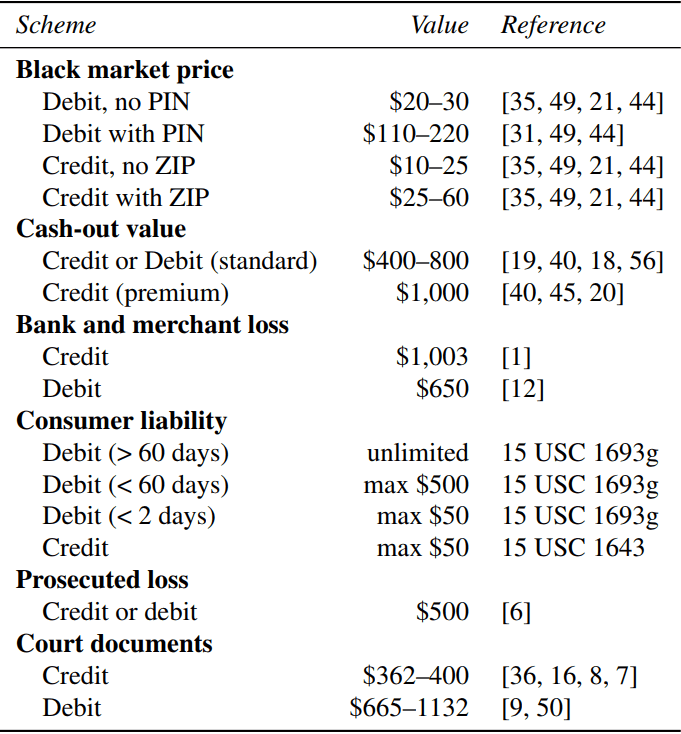
According to Flashpoint analysis, the BriansClub holds more than $414 worth of stolen credit card details. Out of 26M stolen cards, around 14M cards found valid and not expired.
Cyber-security journalist Brian Kerbs has contacted the BriansClub through a support ticket and they acknowledged that “the data center was hacked and the data affected by the data-center breach has been since taken off sales, so no worries about the issuing banks.”
The stolen credit card data form BriansClub is shared with financial institutions to identify and monitor or reissue cards listed on the black market website.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates



.png
)
