Sign1 Malware Hijacked 39,000 WordPress Websites
A client's website was experiencing random pop-ups as server side scanner logs revealed a JavaScript injection related to Sign1, which is a malware campaign...
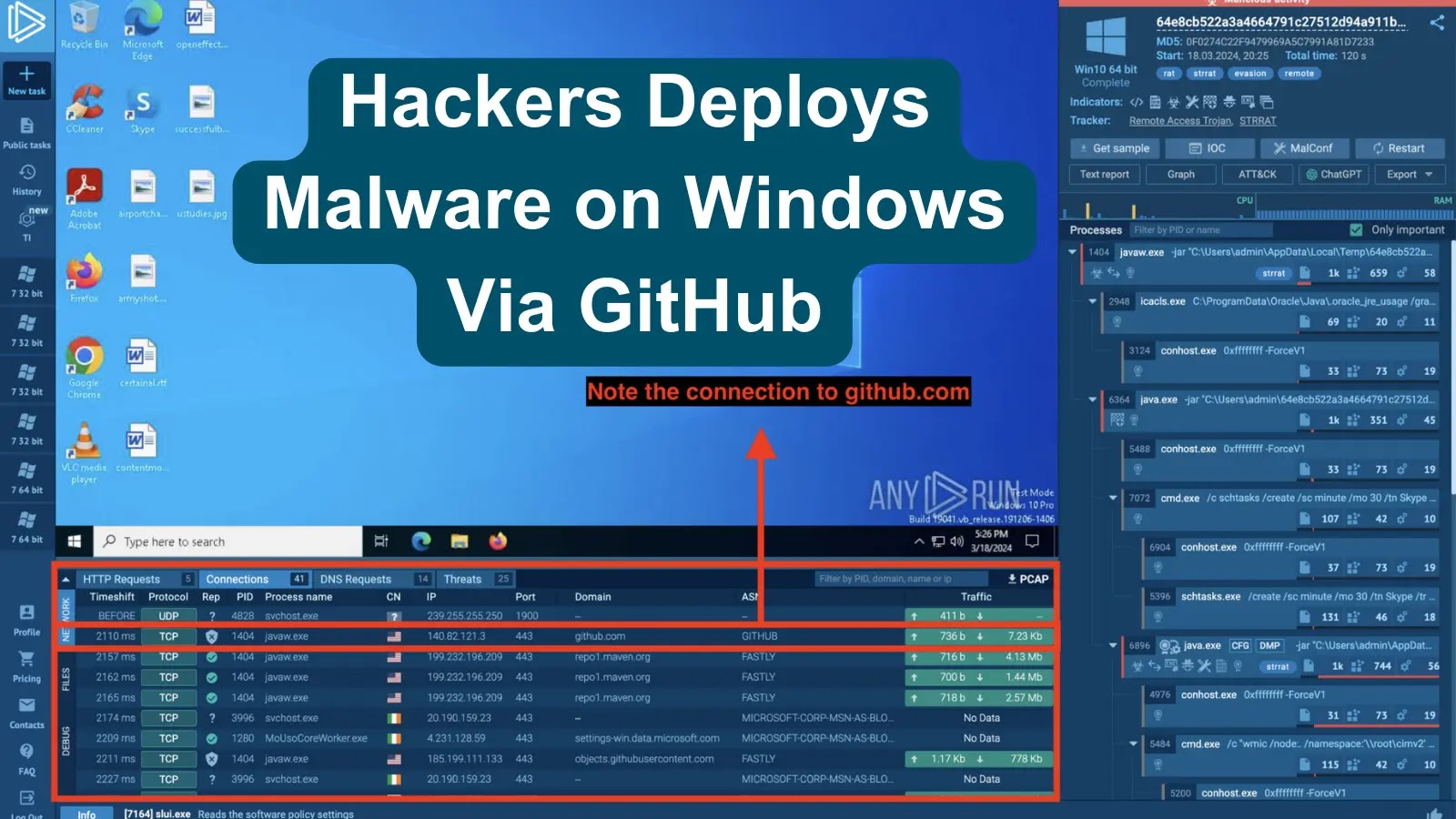
Hackers Deploy STRRAT & VCURMS Malware on Windows Via GitHub
A new phishing campaign targets users with emails containing a button to "verify payment information." Clicking the button triggers the download of a malicious...
TinyTurla Evolved TTPs To Stealthly Attack Enterprise Organizations
Staying ahead of security measures and exploiting new vulnerabilities requires hackers to change their tactics.By doing so, they manage to bypass better defenses,...
Authorities Dismantle Grandoreiro Banking Malware Operation
Group-IB, a cybersecurity firm, helped INTERPOL and Brazil dismantle the Grandoreiro banking trojan operation, as their expertise in threat intelligence and investigation was key. Malware...
Androxgh0st Exploits SMTP Services To Extract Critical Data
AndroxGh0st is a malware that specifically targets Laravel applications. The malware scans and extracts login credentials linked to AWS and Twilio from .env files....
Workings of MalSync Malware Unveiled: DLL Hijacking & PHP Malware
Researchers have discovered the workings of the MalSync malware known as the "DuckTail" or "SYS01".The analysis of the malware revealed the infection vectors,...
Andariel Hackers Leveraging Remote Tools To Exploit Organizations
The Andariel threat group has been discovered to be using MeshAgent when attacking Korean companies.The group has previously attacked Korean Asset management solutions...
Azorult Malware Abuses Google Sites To Steal Login Credentials
A new evasive Azorult campaign that uses HTML smuggling to deliver a malicious JSON payload from an external website. The JSON file is then loaded...
Novel Script-Based Attack That Leverages PowerShell And VBScript
A new campaign has been identified as DEEP#GOSU is likely linked to the Kimsuky group, and it employs a new script-based attack chain that uses numerous PowerShell...
BunnyLoader 3.0 Detected With Advanced Keylogging Capabilities
BunnyLoader is a rapidly developing malware that can steal information, credentials, and cryptocurrencies while also delivering new malware to its victims.Since its first detection in...



.webp)


%20(1).webp)
.webp)

.webp)


.webp)



.webp)
%20(1)%20(1).webp)