A major cybersecurity vulnerability in Cisco Webex Chat (previously known as IMI Chat) has raised alarming concerns after it was revealed that unauthenticated attackers could access the chat histories of organizations using the platform.
First identified in July 2024, the flaw exposed sensitive communications from hundreds, potentially thousands, of organizations spanning internal IT help desks to customer-facing operations.
Critical Exposure of Sensitive Data
Cisco Webex Chat, acquired in 2021 following the purchase of IMI Engage by IMImobile PLC, is widely used for live chat support.
The tool enables organizations to integrate a chat widget into web applications for customers or internal staff.
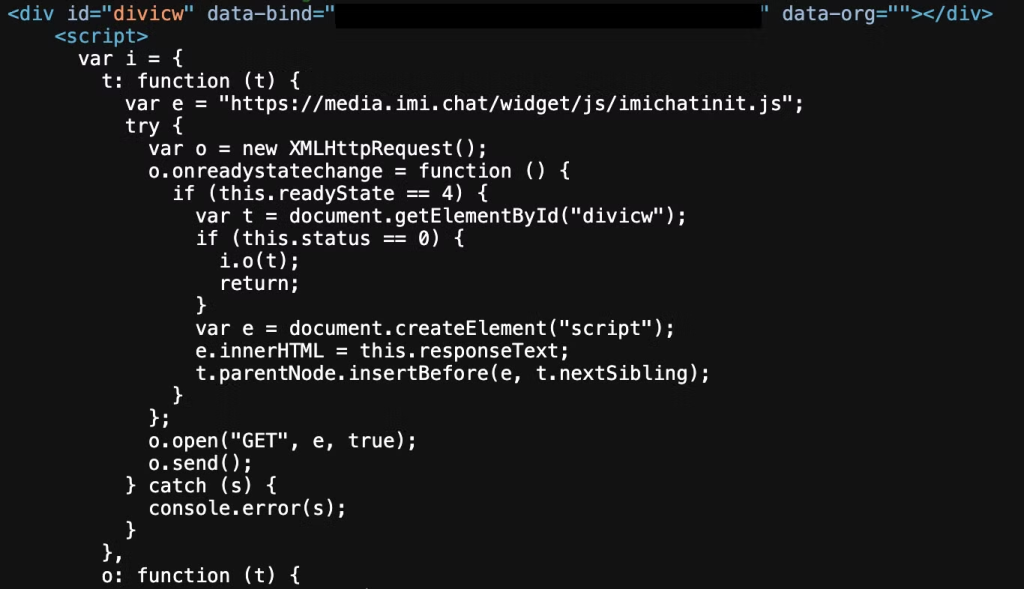
However, this functionality became an attack vector due to the insecure use of a “clientKey” — originally intended as a public identifier — which was also employed as a secretKey for sensitive API calls.
The issue allowed threat actors to list and retrieve chat thread metadata and even access the full historical conversation logs.
These logs could potentially contain sensitive customer information, personally identifiable information (PII), internal credentials, and responses to security queries.
How the Exploit Works
The flaw was rooted in the way chat threads were initialized and managed via backend API calls. Researchers discovered the following:
- Thread Initialization: The /threads API endpoint used the clientKey to create new chat sessions but also inadvertently allowed the listing of existing threads.
- Unauthorized Thread Access: By sending a GET request with the clientKey, attackers could retrieve metadata for ongoing and past chat threads, including thread identifiers (UUIDs).
- Chat History Retrieval: Attackers could exploit another API call, GetPreviousChatHistory, to access the complete text content of chat threads. Parameters like the app UUID, client ID, and thread ID — which could be harvested via earlier steps — were enough to retrieve sensitive conversation logs.
Proof-of-Concept and Real-World Impact
According to the Ophion Security blog, Researchers created a proof-of-concept (PoC) script that demonstrated how attackers could exploit this vulnerability with only minimal information, such as the app UUID embedded in the widget’s JavaScript or the domain origin hosting the chat.
POST /rtmsAPI/api/v3/apps/CLIENT_ID/threads HTTP/2
Host: CUSTOMERNAME-usor.apps-imiconnect.io
Content-Length: 165
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.6613.120 Safari/537.36
Content-Type: application/json
Accept: */*
Secretkey: CLIENT_KEY
Priority: u=1, i
{"title":"da0f3fca-5f21-4b8b-b76d-1bf5baf5813c_APP_ID_ALLOWED_ORIGIN_1727372312156","type":"Conversation","status":"Active"}Tested against a real organization, the script successfully accessed all historical chat logs, revealing sensitive discussions between employees and IT teams.
This significant oversight by Cisco underscores the risks of inadequate security in SaaS products. Chat systems, widely assumed to be secure environments, can hold critical information that attackers can leverage for further exploits.
Organizations using Cisco Webex Chat are strongly advised to immediately audit their environments and ensure they are using a patched or updated version of the software.
Cisco must also prioritize revisions to its authentication and API handling mechanisms to safeguard sensitive customer and organizational data from future attacks.
As cybersecurity concerns continue to escalate, this incident serves as a stark reminder of the critical need for rigorous security testing and monitoring in enterprise SaaS tools.
Collect Threat Intelligence with TI Lookup to improve your company’s security - Get 50 Free Request



.png
)
