As the world moves increasingly into a digital realm, the security of data stored in the cloud is an ever-growing concern for businesses and individuals alike.
Cloud computing enables access to our most sensitive and critical information from any device with an internet capability, making it extremely attractive to those looking for easy and efficient storage capabilities.
But this convenience also comes with risks – our data isn’t as secure as we might like or assume unless appropriately managed.
That’s why it’s essential to understand what measures can be taken to ensure that your data remains private, protected, and available only to authorized users on approved networks and systems.
In this blog post, we’ll explore the various ways you can securely use cloud services while maintaining total control over who has access to your business’s information – from encryption strategies to identity management solutions – so that you have peace of mind knowing that your company’s confidential electronic files remain secure in today’s uncertain online landscape.
What is Cloud Security and Data Privacy
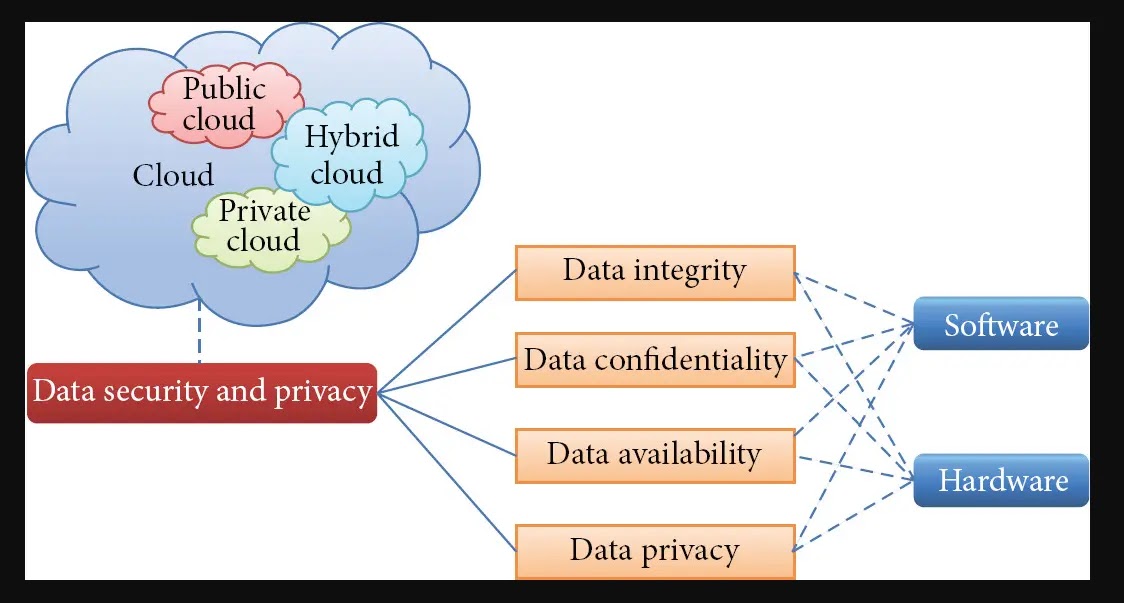
The importance of cloud security best practices and data privacy continues to grow as cloud technology use surges upwards.
Cloud penetration testing checklist encompasses maintaining the confidentiality, integrity, and availability of personal and sensitive information stored or processed in the cloud environment.
It is the measures they employ to defend against cyber intrusion and malicious attacks. Data privacy, on the other hand, pertains to maintaining the confidentiality of, if applicable, personal and sensitive information before, during, and after storage or processing distributes the same in a cloud environment.
This teaches proper consent for data collection and processing, ensuring proper disaster preparedness, and implementing secure data handling practices. Data encryption can also be used as a means to protect stored and transmitted data from unauthorized access, manipulation, or theft.
Benefits of using Cloud Security and Data Privacy

Data security and privacy are key concerns in today’s digital world, including the workings of businesses and even the everyday lives of individuals.
Cloud security best practices is taking root due to its advantages over traditional firewall measures for business entities.
Firstly, cloud security allows flexibility and scalability, enabling a business entity to alter its security needs based on evolving dynamics quickly.
Additionally, higher levels of automation provided by cloud security solutions mean less manual job costs and effort.
Identity and Access Management (IAM) solutions allow for comprehensive control over who can access sensitive data and applications while ensuring that these users remain compliant with policies.
Businesses can finally be confident that their sensitive information is protected since cloud security is reliable and cost-efficient. Moreover, data privacy is vital for any business or individual to retain trust and build a customer reputation.
By opting for the use of cloud security best practices, a business entity can be assured that its consumers’ sensitive information is stored and managed securely.
Challenges of using Cloud Security and Data Privacy
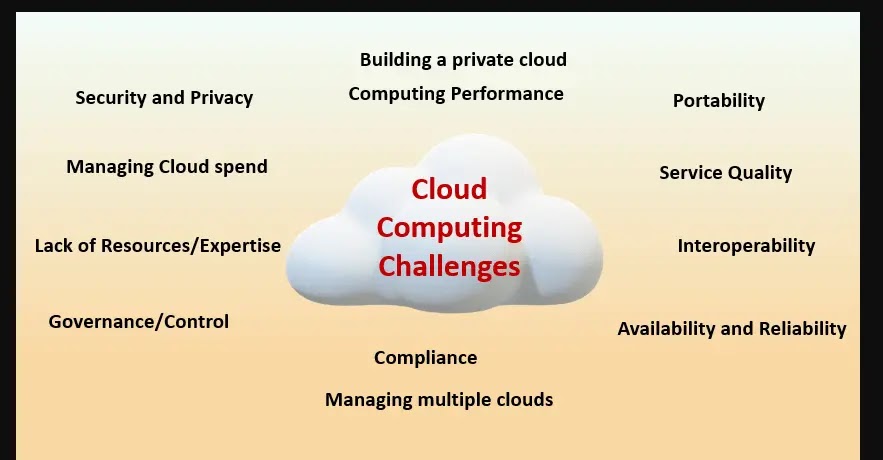
Business operators are moving their data and operations to the cloud with the continuous shift towards cloud computing. This move comes with its own challenges, especially in the guarantees for preserving privacy and safeguarding cloud security.
Today’s prime challenge businesses struggle with is securing important data in public clouds.
IAM solutions can assist in providing solutions to that dilemma and are primarily used as cybersecurity measures for regulating access to data in the cloud.
Security Compliance is another common challenge, as large companies have to meet specific regulations and industry standards. With the increased complexity of today’s cloud computing environment, business entities must ensure that all security measures are always up to date.
Also, businesses must adhere to several regulations and standards, such as GDPR or HIPAA, if they hoard sensitive data in the cloud. Non-compliance with these rules typically means skyrocketing costs, heavy fines, and legal problems.
How to ensure your data privacy with Cloud Security best practices

In recent years, more and more people are trusting cloud solutions for their businesses and personal uses. Although the convenience of the cloud is fantastic, the globe is concerned about dealing with data privacy issues.
Fortunately, there exist cloud security solutions that will help you ensure no one can easily access your data.
It should contain encryption functions, controls over who may access it, and monitoring mechanisms to detect irregular usage activity.
Besides that, choose a good provider that understands its clients’ privacy stance and has good experience in its lines.
Some factors to consider include choosing reliability and ensuring whatever solution you pick meets industry regulations and fields like GDPR or HIPAA standards. To learn more about cloud security best practices and find a reliable provider, you can explore N-ix for valuable insights and resources.
Best practices for maintaining data privacy in the cloud
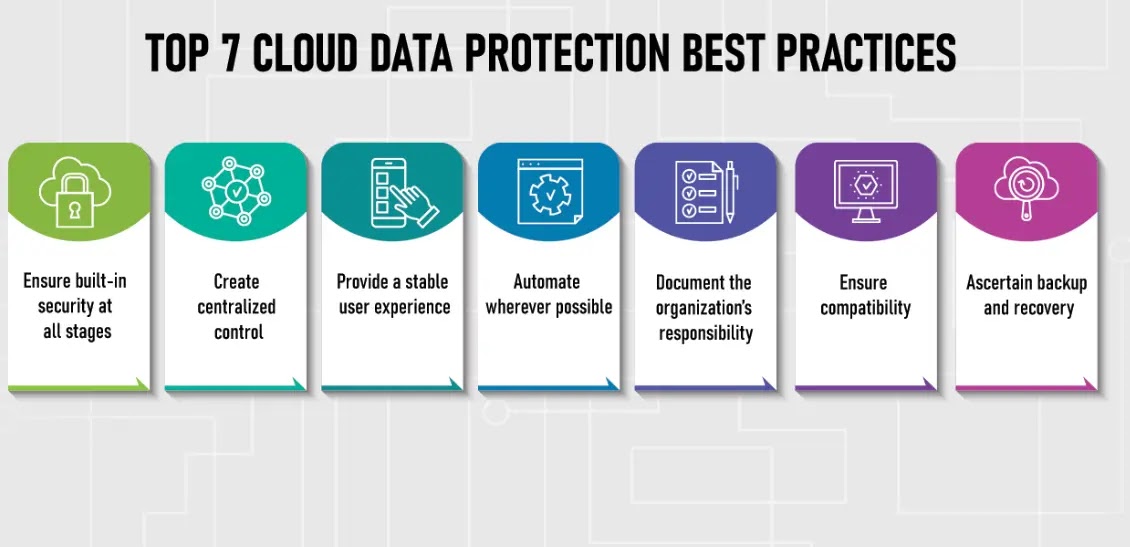
Data privacy in the cloud is a serious concern as more and more companies rely on cloud-based services. However, businesses should follow several best practices to ensure their data’s privacy in the cloud.
One of the most important practices is choosing a cloud provider with strong security measures and a known entity that protects their customers’ data well.
Other good practices would include using robust authentication protocols, regularly monitoring activity logs, thoroughly checking up on software and security protocol updates until they cascade across all of the organization’s systems, and periodically refreshing knowledge bases on old threats, new attacks, and emerging trends/technologies so that organizations can stay one step ahead of potential threats.
Final Thoughts
Ultimately, it’s essential to maintain data privacy in the cloud for security and composure.
The solutions for securing the cloud and maintaining data privacy have many advantages: improved system reliability, protection from stolen services, secure communication services, and automated backup procedures, among others.
However, since reliance on the cloud entails a degree of uncertainty regarding storage or some service functions, ensuring sufficient data privacy has proved difficult.
Considering this aspect is vital as you evaluate various cloud security best practices before committing; that way, you can maximize their advantage while minimizing their disadvantage.



.png
)
