Hackers have exploited a vulnerability in a 14-year-old Content Management System (CMS) editor, FCKeditor, to launch SEO poisoning attacks against government and educational websites worldwide.
This campaign has compromised numerous sites, redirecting unsuspecting users to malicious or scam websites through open redirects and poisoned search results.
Open redirects are a critical flaw where websites redirect users to external URLs without proper validation, making them a prime target for cybercriminals.
These redirects are particularly dangerous because they originate from legitimate domains, allowing attackers to bypass security filters and trick users into visiting malicious sites.
This technique has been effectively used to perform phishing attacks, distribute malware, and scam users while maintaining the appearance of legitimacy.
You can analyze a malware file, network, module, and registry activity with the ANY.RUN malware sandbox, and the Threat Intelligence Lookup that will let you interact with the OS directly from the browser.
FCKeditor: The Target of Choice
The focal point of this campaign is the outdated FCKeditor plugin, a web text editor popular for editing HTML content directly within web pages.
Despite being rebranded as CKEditor in 2009 with significant improvements, many sites continue to use the deprecated version, especially in the education and government sectors.
Cybersecurity researcher @g0njxa uncovered the campaign after noticing Google Search results for ‘Free V Bucks’ generators hosted on university sites, revealing the extent of the exploitation.

Educational and Government Sites Compromised
The campaign has not spared prestigious institutions and government entities. Among the affected are MIT, Columbia University, Universitat de Barcelona, Auburn University, University of Washington, Purdue, Tulane, Universidad Central del Ecuador, and the University of Hawaiʻi.
Government and corporate sites, including those belonging to Virginia, Austin, Texas, Spain, and Yellow Pages Canada, have also been targeted, utilizing a combination of static HTML pages and redirects to malicious sites.
In SEO poisoning, attackers manipulate search engine results to promote malicious websites.
By leveraging the trust and authority of compromised domains, these actors can poison search engine results, leading unsuspecting users to scam sites, fake news articles, phishing pages, and malicious browser extensions.
This not only endangers users but also tarnishes the reputation of the compromised sites.
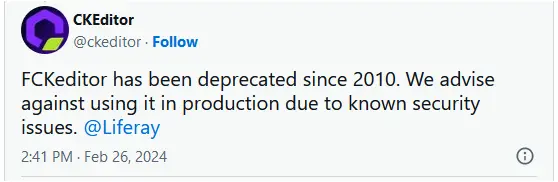
FCKeditor Deprecated
The software maker has responded to the open redirects campaign, emphasizing that FCKeditor has been deprecated since 2010 and should no longer be in use.
However, the persistence of this outdated software on critical sites highlights the broader issue of legacy systems and their vulnerabilities.
It’s a stark reminder for organizations to update and patch their systems to protect against such exploits.
This campaign underscores the importance of maintaining up-to-date software and the need for vigilance against sophisticated cyber threats.
As attackers continue to exploit vulnerabilities in outdated systems, website administrators and users are responsible for ensuring the security of their digital environments.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are extremely harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.



.png
)

