CrushFTP is a file transfer server that supports secure protocols, offers easier configuration, and offers powerful monitoring tools.
It also provides a web interface that allows users to transfer files using a web browser.
A critical vulnerability associated with FileSystem escape has been discovered and addressed in the latest version.
This particular vulnerability allows any user to download system files escaping from the virtual file system present in the CrushFTP application.
Moreover, there have also been reports indicating the exploitation of this vulnerability in the wild by threat actors.
Free Webinar | Mastering WAAP/WAF ROI Analysis | Book Your Spot
No CVE was assigned to this vulnerability at the time of reporting.
Additionally, customers who use Demilitarized Zones (DMZ) in with their CrushFTP instance are not affected by this vulnerability due to the protocol translation system.
CrushFTP Servers Zero-day
According to the reports shared with Cyber Security News, there have been several exploitation attempts over CrushFTP instances owned by multiple U.S. Entities, which are speculated to be an activity of Politically Motivated Intelligence Gathering.

To provide a brief insight, the CrushFTP application is a bundled stand-alone portal executable (PE) that probably doesn’t have a standard installation location.
The application can run on Windows, macOS and Linux and depend on Java.
To prevent the exploitation of this vulnerability, users of CrushFTP are recommended to upgrade to the latest version, v11.1.0, which has a patch for it.
All versions before CrushFTP v9 are affected.
For more information about the changelogs and other information, the CrushFTP wiki page can be viewed.
How To Update?
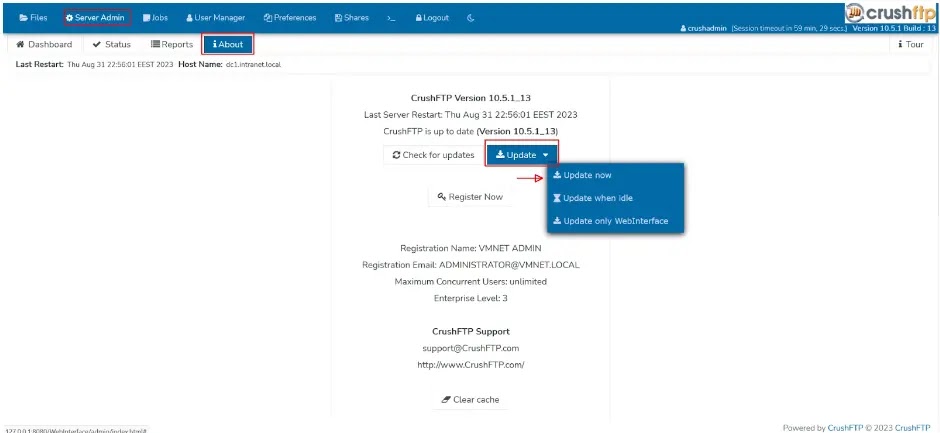
To update CrushFTP to the latest version v11.1.0 (for Online users), the following steps can be followed:
- Login to the dashboard using your “crushadmin” equivalent user in the WebInterface.
- Click on the About tab.
- Click Update, Update Now.
- Wait roughly 5 minutes for the files to download, unzip, and be copied in place. CrushFTP will auto-restart once done.
- Finished.
.webp)
For Offline users, the below steps can be followed
- Download CrushFTP11.zip from our download page. (https://www.crushftp.com/early11/CrushFTP11.zip)
- Give it the name `CrushFTP10_new.zip` and place it in the CrushFTP main folder. (Same location where you have your prefs.XML file)
- See the above normal instructions, as Crush will use your local offline zip file.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.



.png
)
