New malspam email campaign discovered with fake windows updater and its Builder, through which hackers launching Cyborg Ransomware to encrypt the compromised systems files.
A spam email claims to be from Microsoft and email body urges the victims to Install the Latest “Microsoft Windows Update” by opening the attached file.
Fake update attachment appears with a random name although having a “.jpg” file extension, but is actually an executable file with the file size of 28KB.
Once the victims execute the file, a .NET downloader that will drop another malware on compromised victims’ computers.
Researchers found #Strings section that gives major clues to the executable’s behaviors. One of the notable things is that the hoax Microsoft update will download another executable file from GitHub.
Cyborg Ransomware Behaviour
The main ransomware file bitcoingenerator.exe downloaded from the Github account named misterbtc2020 and the file is .NET compiled malware, the Cyborg ransomware.
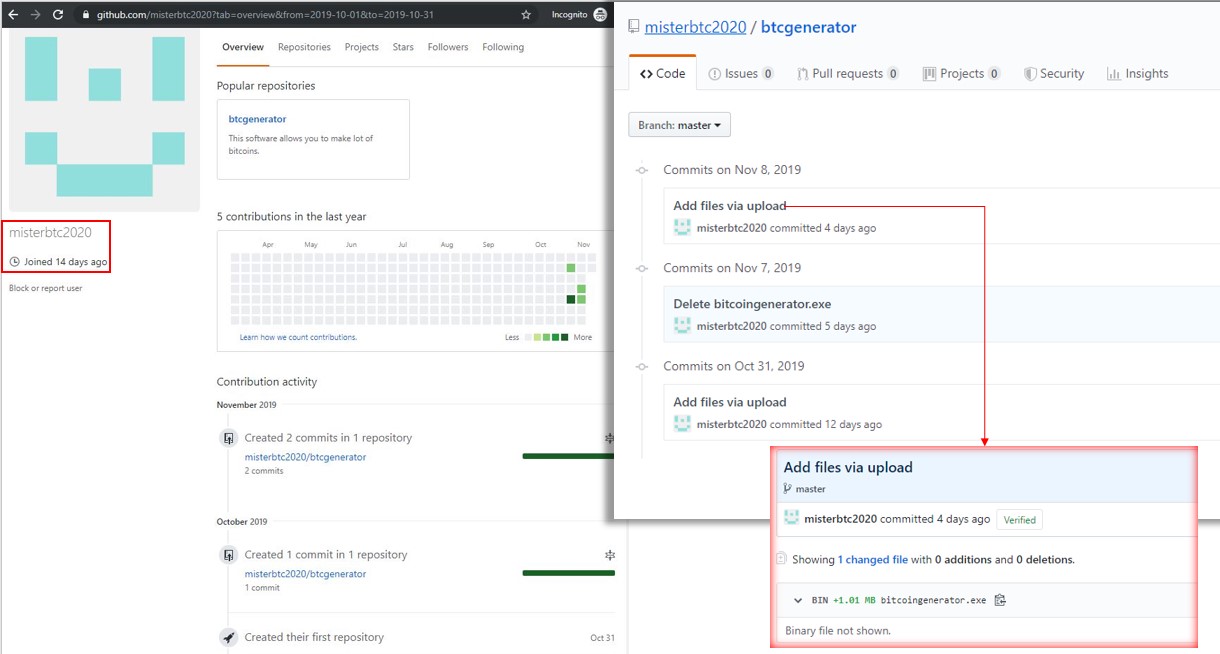
Successful execution will encrypt the infected user’s system and “.777” has been appended to the encrypted files’ filenames.

Once the ransomware completes the encryption process, the ransomware notes will be dropped into the Desktop.
Ransom note demands victims to send $500 to their bitcoin wallet and also request victims to reach the attack via email.
Trustwave researchers also found 3 more samples, “The file extension these Cyborg ransomware samples will append to the encrypted files varies as observed from the samples found on VT. This is an indication that a builder for this ransomware exists. “
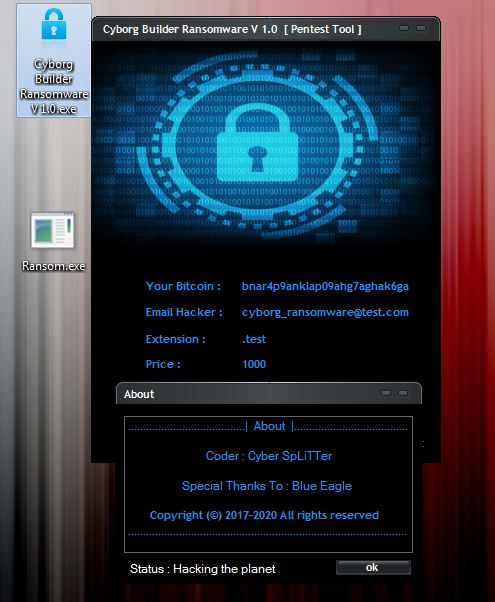
Attackers using newly created GitHub account which contains 2 repo’s Cyborg-Builder-Ransomware, and Cyborg-russian-version.
“The Ransomware can be created and spread by anyone who gets hold of the builder. It can be spammed using other themes and be attached in different forms to evade email gateways.” Trustwave said.
You can also read the complete Ransomware Attack Response and Mitigation Checklist.
Indicator of Compromise
SHA1: 34BAC75C515CAC706ED0D9EF5BA8B76E60FF78F7
SHA1: 8E830F5C5D144CBE7554C91A846A20ACA6322C60
SHA1: 496063408CD61466614CC8370A6687D6F8D45663
SHA1: 50E15A5AAE1C45BE13B4F9B23A6596A822B378A2
SHA1: DF4A3733D76D96BF1A646AD4F807AB668A88A3DC
Cyborg Builder Ransomware V 1.0.7z (2522495 bytes)
SHA1: 7E251FA01E11A7240856C4934714B40B9EF519EF
Cyborg Builder Ransomware V 1.0.exe (2630144 bytes)
SHA1: 8599C32E71D39BBD89B7FCAE419FDF4619A6D2F3



.png
)
