Cybersecurity researchers have identified a renewed wave of attacks involving the Dark Crystal RAT (DCRat), a dangerous remote access Trojan that has resurfaced through a Malware-as-a-Service (MaaS) model.
Attackers are actively targeting gamers by distributing malicious software disguised as gaming cheats and cracks, primarily through YouTube.
Malware Distribution Exploits YouTube Platform
The attackers behind DCRat have turned to YouTube as their primary distribution channel. They create fake or hijacked accounts to upload videos promoting supposed gaming cheats, cracks, bots, and similar software.
Each video description contains a download link pointing users to legitimate file-sharing services hosting password-protected archives.
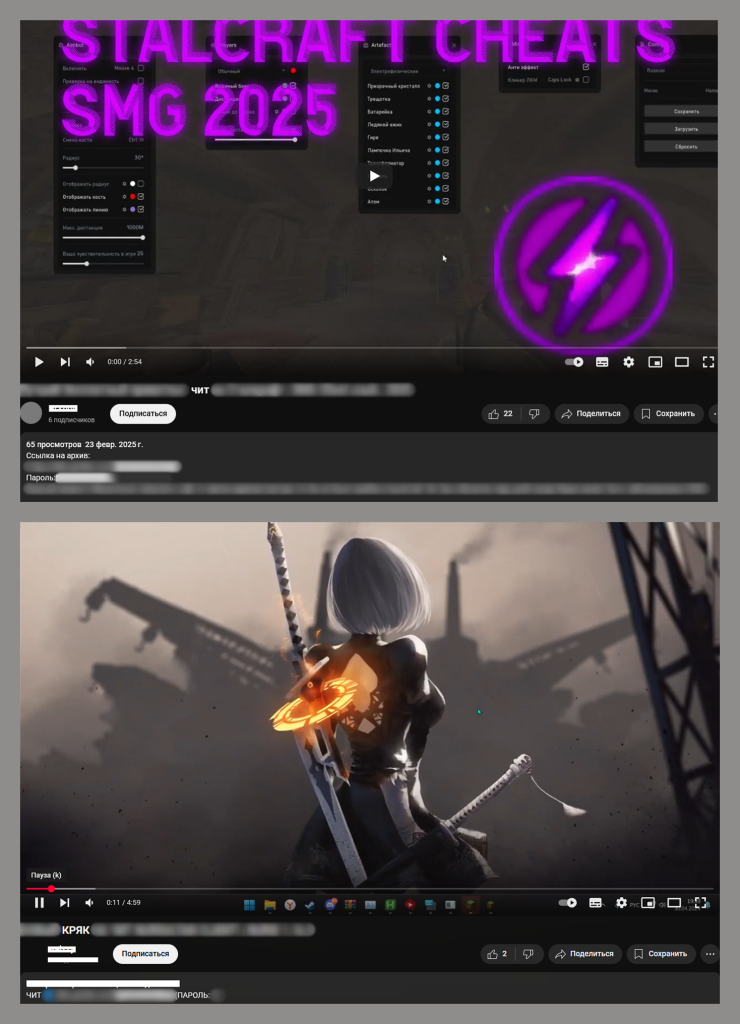
The password itself is conveniently provided in the same description, making the process appear trustworthy.
However, instead of providing the promised gaming tools, these archives contain the DCRat malware hidden among various junk files and folders designed to distract victims.
DCRat, also known as Dark Crystal RAT, first emerged in 2018 and has since evolved into a sophisticated threat.
The malware operates as a backdoor, allowing attackers remote access to infected devices.
Additionally, DCRat supports modular plugins that significantly enhance its capabilities.
Researchers have identified 34 distinct plugins associated with this malware family, including dangerous functionalities like keystroke logging, webcam spying, file theft, and password exfiltration.
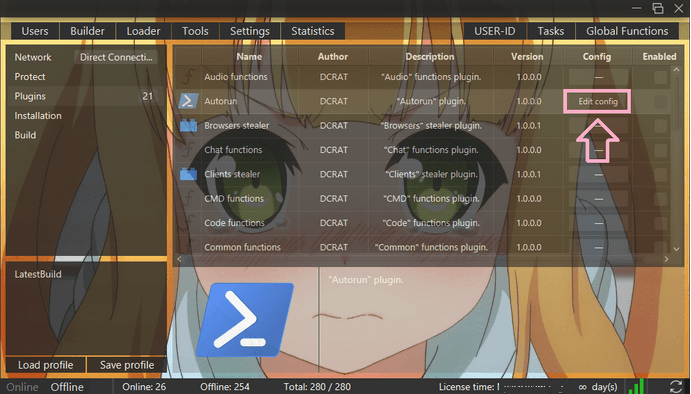
Infrastructure Leveraging Anime-Themed Domains
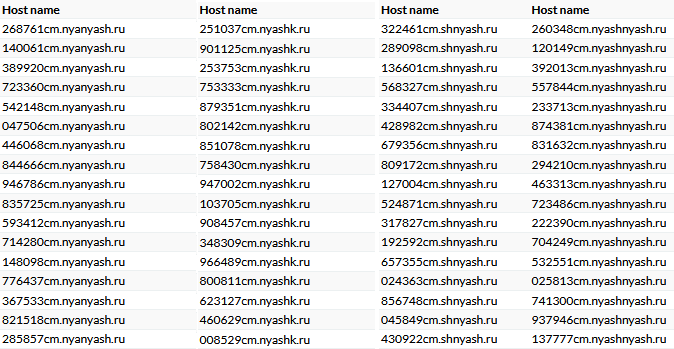
To host command-and-control (C2) servers, cybercriminals have registered numerous second-level domains—primarily within Russia’s “.ru” domain zone—and created multiple third-level domains for operational use.
Since early 2025 alone, at least 57 new second-level domains have been registered by the attackers.
Interestingly, these domains frequently contain anime-inspired slang terms such as “nyashka,” “nyashkoon,” and “nyashtyan,” which resonate with fans of Japanese pop culture.
Telemetry data indicates that Russia is the primary target of this campaign, with approximately 80% of detected infections occurring there.
Additional affected regions include Belarus, Kazakhstan, and China.
Kaspersky security solutions detect this malware as “Backdoor.MSIL.DCRat.”
Experts strongly advise users to download game-related software exclusively from trusted sources to avoid infection risks associated with password-protected archives distributed via unofficial channels.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
