A zero-day vulnerability in Dropbox for Windows allows attackers to escalate privileges from simple windows users privilege to the reserved SYSTEM privilege.
The vulnerability resides in the DropBoxUpdater service, which is responsible for keeping the client application up to date.
Dropbox Updater Vulnerability
The vulnerability was discovered by security researcher Decoder and Chris Danieli and they have created a PoC to test the vulnerability.
The DropBoxUpdater is the component of the Dropbox Client Software suite, the updater installed as a service and keeps 2 scheduled tasks running with SYSTEM permissions.
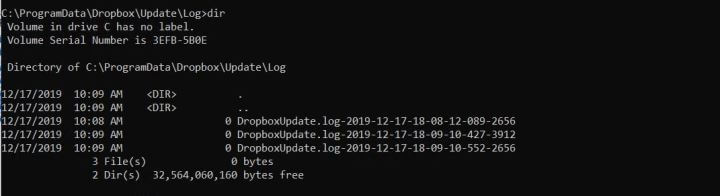
Dropboxupdate writes the log files in the directory “c:\ProgramData\Dropbox\Update\Log”, any users can access the directories or to add, delete the files.
Another notable thing is that SetSecurity call made through SYSTEM privileges on the files, this allows an attacker to exploit via hardlink.
“But we have a problem here, we have to “guess” the logfile name, that is the exact time (including milliseconds) and the PID of the updater process,” researchers said.
Researchers provided details of the vulnerability on September, 18th and Dropbox said the vulnerability will be fixed before the end of October. Since 90 days passed researchers published a post with the details.
MicroPath
0Patch published a micropatch to fix the vulnerability, “we decided that the most reliable fix would be to simply cut off the log-writing code from DropBox Updater.”
The micropatch is provided for free, so anyone installing and registering 0patch Agent will immediately get it and have it applied to DropBox app.
Dropbox is a file hosting service that offers cloud storage, file synchronization, personal cloud, and client software. It was founded in June 2007 and has more than 500 million users.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates



.png
)
