A peculiar malicious Python script has surfaced, employing an unusual and amusing anti-analysis trick to mimic a fake Blue Screen of Death (BSOD).
The script, which has a low detection rate of 4/59 on VirusTotal (SHA256: d716c2edbcdb76c6a6d31b21f154fee7e0f8613617078b69da69c8f4867c9534), drew the attention of security researchers for its creative use of Python’s Tkinter library.
The Execution and Impact
The Tkinter library, commonly used for creating graphical user interfaces (GUIs), is not typically associated with malicious scripts.
While most Python malware operates through command-line execution, the use of Tkinter here makes the script stand out.
It uses the library to generate and display a full-screen window that imitates the infamous BSOD, often associated with a critical Windows error.
This window, which lacks controls for closing or resizing, is created with the following key snippet:
root = tk.Tk()
root.configure(background="dark blue")
root.overrideredirect(1)
root.geometry("%dx%d+0+0" % (w, h))
root.wm_attributes("-topmost", 1)
root.mainloop()The -topmost attribute ensures the fake BSOD remains visible over all other active windows, creating an illusion that the system has crashed. The crafted message within the script reads:
“A problem has been detected and Windows has been shut down to prevent damage to your computer…”
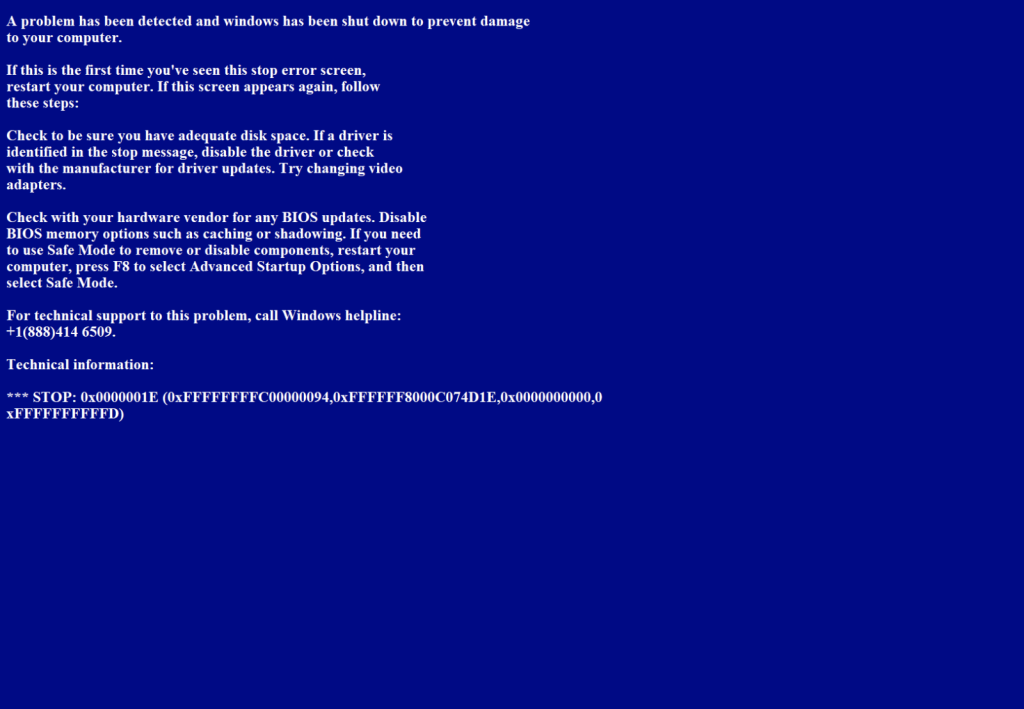
While the BSOD message itself is not particularly sophisticated, it effectively frustrates users and could divert attention during manual malware analysis.
Although not highly destructive, this fake BSOD trick demonstrates the persistent creativity of malware developers.
By leveraging seemingly benign libraries like Tkinter, attackers can assemble highly convincing, disruptive scripts to target unsuspecting users.
A senior cyber security consultant from SANS Institute examined the functionality of this script and noted that while such techniques are not groundbreaking, they can still complicate forensic or reverse-engineering efforts.
The low detection rate on VirusTotal raises additional concerns about how such scripts can evade traditional defenses.
This highlights the need for behavioral analysis and monitoring rather than relying solely on signature-based detection.
This incident serves as a reminder that even simple pranks, such as a fake BSOD, can have broader implications in the context of cybersecurity.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
