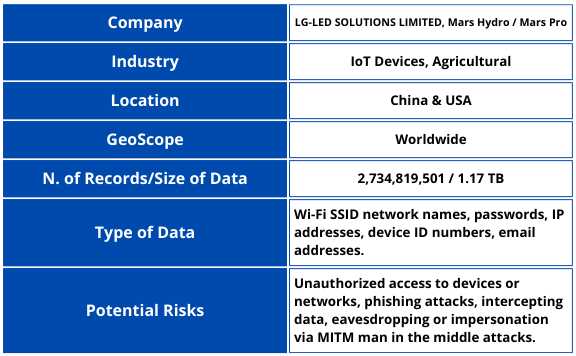
A massive security lapse has exposed over 2.7 billion records, including sensitive Wi-Fi credentials, device information, and user details, raising global concerns over IoT (Internet of Things) security.
Cybersecurity researcher Jeremiah Fowler uncovered this unprotected database, linked to Mars Hydro, a China-based manufacturer of IoT-enabled grow lights and agricultural devices, and disclosed the findings to vpnMentor.
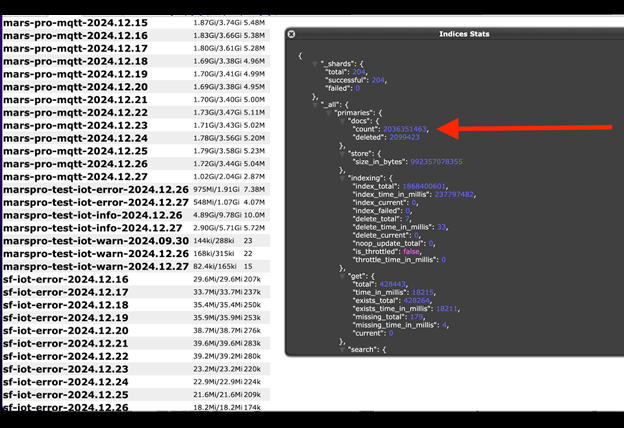
The exposed database, totaling 1.17 TB in size, contained 2,734,819,501 records, including sensitive information such as Wi-Fi network names (SSID), passwords, IP addresses, device IDs, and logs related to connected IoT devices.
Alarmingly, this data was stored in plain text with no encryption, making it vulnerable to unauthorized access and potential exploitation.
Details of the Breach
The leaked data was traced to Mars Hydro and its affiliated company, LG-LED SOLUTIONS LIMITED, registered in California.
The database also included API details, device operating system information (e.g., iOS, Android), and error logs referencing Mars Hydro’s products and its related control application, Mars Pro.
Despite Mars Hydro’s claim that its official app collects no user data, the logs revealed connectivity details and user credentials, likely captured by the IoT devices themselves.
Fowler noted that the breach extended risks such as unauthorized network access and the potential for advanced cyberattacks.
For instance, exposed SSID credentials could allow attackers to access private Wi-Fi networks, intercept data, or even exploit connected devices for malicious purposes.
Mars Hydro restricted public access to the database shortly after Fowler reported the issue.
However, key questions remain unanswered, such as how long the database was exposed and whether other parties accessed the data before the breach was secured.
This incident highlights the growing vulnerabilities in IoT ecosystems. According to a Palo Alto Networks report, 57% of IoT devices are highly vulnerable, with 98% transmitting unencrypted data.
Many IoT devices also rely on outdated software, default passwords, or lack authentication entirely, exacerbating security threats.
Fowler emphasized the risk of data breaches like this being exploited for “nearest neighbor attacks,” where hackers infiltrate nearby networks via exposed Wi-Fi credentials.
Such vulnerabilities could facilitate surveillance, man-in-the-middle (MITM) attacks, or manipulation of IoT devices to disrupt operations.
Experts urge IoT manufacturers to prioritize security by encrypting sensitive data, conducting regular security audits, and implementing robust authentication mechanisms.
Developers should also avoid logging sensitive user information in plain text and restrict access to cloud storage repositories.
While Mars Hydro and its affiliates have not faced misconduct allegations, this breach underscores the critical need for heightened data protection standards in the rapidly expanding IoT landscape.
For users, adopting strong passwords and securing IoT devices remains paramount to safeguarding privacy and preventing cyberattacks.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
