Google has announced the launch of OSV-Scanner V2, an open-source tool designed to enhance vulnerability scanning and remediation across various software ecosystems.
This update follows the recent release of OSV-SCALIBR, another powerful tool in the OSV suite, which together form a comprehensive platform for managing vulnerability metadata and streamlining vulnerability detection and management.
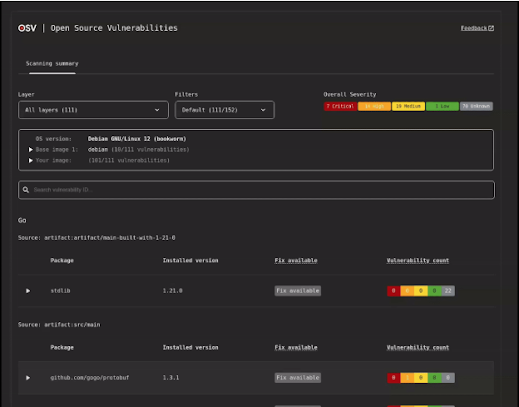
Key Features of OSV-Scanner V2
- Enhanced Dependency Extraction with OSV-SCALIBR:
- Expanded Formats: Supports source manifests and lockfiles such as .NET (deps.json), Python (poetry.lock, not uv.lock), JavaScript (bun.lock), and Haskell (cabal.project.freeze, stack.yaml.lock).
- Artifact Support: Includes analysis of Node modules, Python wheels, Java uber jars, and Go binaries.
- Layer and Base Image-Aware Container Scanning:
- Support for Container Images: Now capable of scanning Debian, Ubuntu, and Alpine container images to provide layer history, base image identification, and filtering of unlikely vulnerabilities.
- Language Support: Currently supports artifacts from Go, Java, Node, and Python.
- Interactive HTML Output:
- Offers an interactive way to present vulnerability scans with features like severity breakdowns, filtering capabilities, and full vulnerability advisory entries.
- Enhances container scanning with layer information and base image identification.
- Guided Remediation for Maven pom.xml:
- Extends guided remediation to Java, allowing intelligent upgrades and strategies to minimize disruptions while maximizing security improvements.
- Supports reading and writing pom.xml files, including updates to local parent pom files and integrating with private Maven registries.
Future Developments and Collaborations
Google has outlined several plans for future developments:
- Continued OSV-SCALIBR Convergence: Integrating more of OSV-SCALIBR’s features into the OSV-Scanner interface.
- Expanded Ecosystem Support: Increasing support for languages, OS advisories, and more general lockfile formats.
- Full Filesystem Accountability for Containers: Enhancing tracking and managing all files within container images.
- Reachability Analysis: Introducing deeper vulnerability impact insights.
- VEX Support: Adding support for Vulnerability Exchange to facilitate vulnerability communication.
Users can engage with OSV-Scanner V2 by visiting the OSV-Scanner or OSV-SCALIBR repositories.
Google encourages contributions via these repositories and invites feedback through the OSV discussion list at osv-discuss@google.com.
This initiative marks a significant step towards open collaboration in cybersecurity, making it easier for developers and security teams to identify and manage vulnerabilities efficiently.
As the technology landscape continues to evolve, tools like OSV-Scanner V2 are crucial for maintaining the integrity of software systems and fostering a more secure digital environment.
With its robust features and collaborative development approach, OSV-Scanner is poised to become an essential tool in the fight against cyber threats.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
