Google has announced a groundbreaking update to its Chrome browser that addresses a vulnerability in the web browser’s code, which has been leaking users’ browsing history for over two decades.
This long-standing issue stems from the CSS :visited selector—a web design feature that allows websites to stylize previously visited links.
While originally designed to improve user experience, it has inadvertently exposed users to privacy risks. The patch, to be implemented in Chrome 136, makes Google the first major browser developer to resolve this problem comprehensively.
A 23-Year-Old Threat
Since the early days of the internet, the CSS :visited selector has been an essential tool for web developers, allowing users to distinguish visited links from unvisited ones.
However, over time, security researchers discovered that malicious actors could exploit this feature to deduce users’ browsing history.
By crafting specific attacks, bad actors could determine whether a user had visited particular sites by observing how links were styled as :visited.
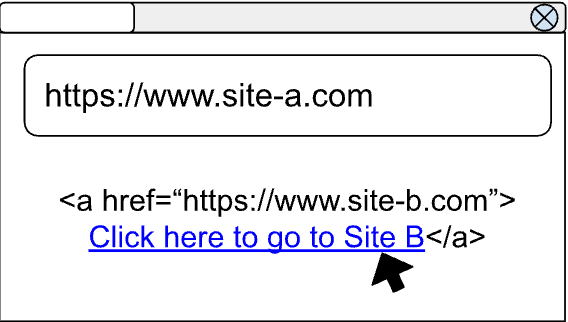
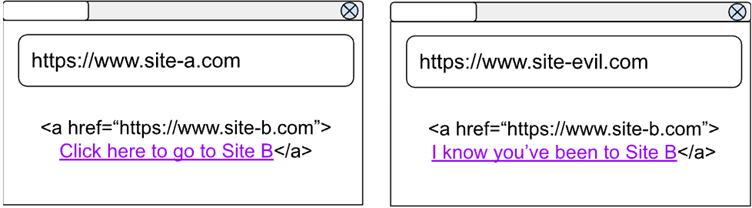
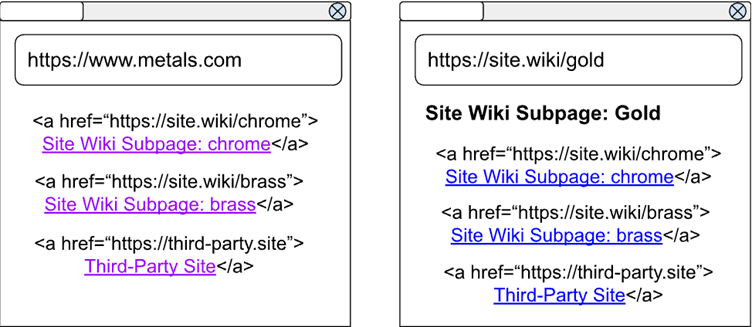
This problem was exacerbated by the fact that, historically, :visited history was unpartitioned.
This meant that if a user visited a website (let’s call it “Site A”) and clicked a link to “Site B,” any other website with the same link to “Site B” (e.g., “Site Evil”) could infer that the user had visited Site B.
This posed serious privacy concerns, as malicious sites could exploit this design flaw to harvest sensitive browsing activity.
Partitioning Visited Link History
With Chrome 136, Google is introducing a new approach called “visited link partitioning,” which renders these attacks obsolete.
Partitioning ensures that a user’s :visited history is no longer a global list accessible across websites. Instead, the visited history will be tied to the specific context in which a link was clicked—namely, the combination of the link’s URL, the top-level site, and the frame origin.
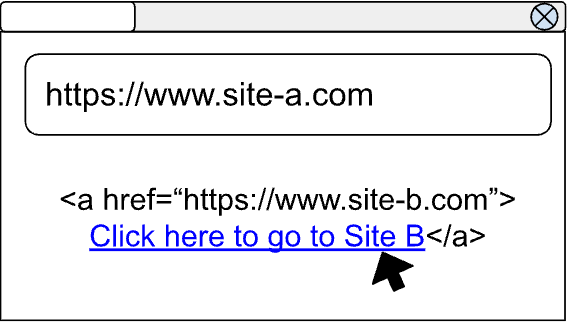
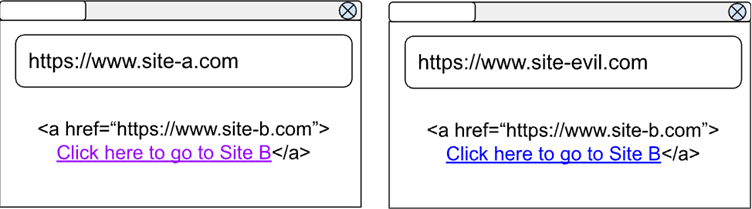
In practice, this means that a link styled as :visited on one site will no longer appear as visited on another site unless the two share a specific browsing context.
For example, if you click a link to Site B while on Site A, this action will only be recorded in the context of Site A.
Should a malicious website like Site Evil attempt to check your visited links, it will find no evidence of your prior browsing activity, thus safeguarding your privacy.
To preserve user experience, the update includes an exception for self-links. This means that subpages on the same site can still appear as :visited even if they were accessed through a different context.
For example, visiting multiple pages on a wiki site will still display those links as visited, enhancing usability while maintaining privacy protections for cross-site activity.
Google’s implementation of partitioned :visited history in Chrome 136 marks a major milestone in web security. By tackling a problem that has lingered for 23 years, Chrome is establishing itself as a leader in privacy innovation.
This update is expected to set a new standard for browser security across the industry and offers Chrome users peace of mind when navigating the web.
As privacy concerns grow in the digital age, this improvement reflects Google’s commitment to protecting its users while maintaining a seamless browsing experience. Chrome users can look forward to this essential update when Chrome 136 rolls out.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
