A newly discovered vulnerability in AnyDesk, the popular remote desktop software, has sparked serious cybersecurity concerns.
Identified as CVE-2024-12754 and tracked under ZDI-24-1711, this flaw allows local attackers to exploit a mechanism to handle Windows background images, potentially escalating their privileges to administrative levels.
Researchers warn that this vulnerability poses a significant risk to sensitive system files, with the Proof-of-Concept (PoC) exploit now publicly available.
Details of the Vulnerability
The vulnerability has been categorized under CWE-59 (Path Traversal) with a CVSS score of 5.5 (Medium), indicating its potential to compromise system confidentiality.
As per a report by Cyber Security News, Cybersecurity researcher Naor Hodorov discovered that the issue resides in AnyDesk’s process of copying desktop background images during session initiation.
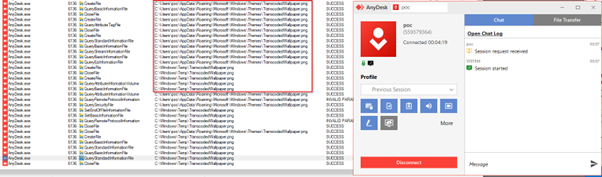
AnyDesk copies the current desktop background image to the C:\Windows\Temp\ directory when initiating a session.
This operation is executed by the AnyDesk service under the NT AUTHORITY\SYSTEM account, which holds high-level privileges.
How Attackers Exploit It
The flaw enables a low-privileged local user to manipulate this file-copying process to perform arbitrary file read or copy operations, as reported by Github. Here’s how the attack unfolds:
File Permissions and Ownership:
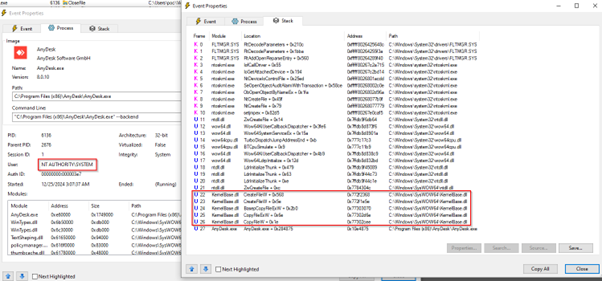
When AnyDesk copies the background image, the resulting file inherits ownership and permissions from the SYSTEM account.
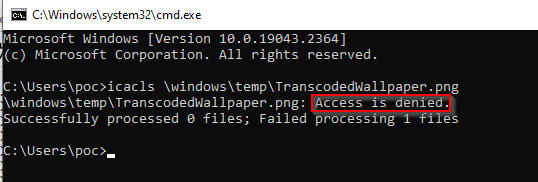
By default, low-privileged users do not have access to files created in C:\Windows\Temp\, as these files are protected by the SYSTEM account.
File Name Pre-Creation:
An attacker can pre-create a file in the C:\Windows\Temp\ directory with the same name as the background image file.
Once the vulnerability is triggered, AnyDesk overwrites this file with data from the source image, but the file retains its original ownership and permissions.
Directory Junction Attack:
By creating a symbolic link (junction) pointing to sensitive system directories, such as \Device\HarddiskVolumeShadowCopy1\Windows\System32\CONFIG, attackers can redirect AnyDesk’s file-copying operation to access protected files like the SAM (Security Account Manager), SYSTEM, and SECURITY files.
These files are critical for the Windows authentication system.
Privilege Escalation: With access to these files, attackers can extract hashed credentials and machine keys to obtain administrative privileges, enabling full system compromise.
While exploitation requires local access and low-level privileges, the vulnerability’s implications are severe.
Attackers can use the exploit to steal credentials, gain unauthorized access to sensitive data, and even take full control of the affected system.
To mitigate this threat, AnyDesk has released version 9.0.1, which includes patches to address the vulnerability. Users and organizations are strongly advised to update to this version immediately.
The discovery of CVE-2024-12754 underscores the growing sophistication of local privilege escalation techniques. What may seem like a benign feature, such as handling desktop background images, can be exploited in creative and high-impact ways.
This reminds organizations and developers to scrutinize even the most seemingly innocuous application processes for security flaws.
While AnyDesk’s patches effectively address this issue, users must remain proactive in applying updates and adopting robust security measures.
The release of the PoC highlights the urgency of taking immediate action to protect against potential exploitation. Cybersecurity vigilance remains a necessity in the face of evolving threats.
Are you from SOC/DFIR Team? - Join 500,000+ Researchers to Analyze Cyber Threats with ANY.RUN Sandbox - Try for Free



.png
)
