Cybersecurity service Have I Been Pwned (HIBP) has disclosed one of the largest data exposure events in its 11-year history, integrating 23 billion rows of stolen credentials from a malware operation dubbed “ALIEN TXTBASE.”
The breach corpus contains 493 million unique website-email pairs tied to 284 million unique email addresses, alongside 244 million new passwords added to HIBP’s Pwned Passwords database.
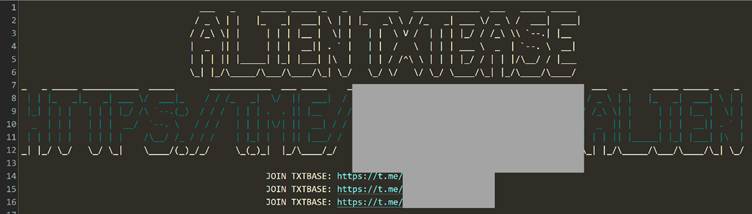
The disclosure follows a month-long effort to parse and validate stealer logs—records of credentials harvested by info-stealing malware—distributed through Telegram channels linked to cybercrime networks.
Scale and Source of the ALIEN TXTBASE Leak
The data originated from a Telegram channel offering “stealer logs”—credentials siphoned from malware-infected devices.
The channel initially shared two 5GB “teaser” files containing 36 million entries before requiring paid subscriptions for full access.
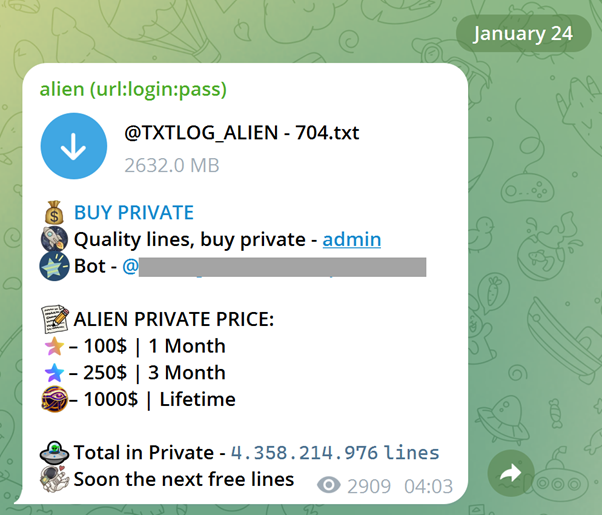
HIBP’s analysis traced these logs to victims globally, including a Filipino Netflix user, a German Mercedes owner, and individuals targeted via pirated software downloads.
For example, one victim unknowingly installed malware disguised as Notepad++ software, leading to the theft of corporate credentials saved in their browser.
Telegram’s role in facilitating cybercrime has drawn scrutiny, as its anonymity features enable widespread distribution of illicit data.
The ALIEN TXTBASE channel alone hosted 744 files, with attackers monetizing access to fresh logs for credential-stuffing attacks involving hackers reusing stolen credentials across multiple platforms.
Verification and Impact on Victims
HIBP founder Troy Hunt confirmed the legitimacy of the data through geofenced password-reset tests.
By simulating logins from victims’ regions—such as the Philippines, Mexico, and Venezuela—Hunt verified email addresses tied to services like Netflix.
A stark example involved a German user whose 1,100 exposed logins revealed hobbies (whisky collecting), tech preferences (Firefox usage), and professional interests (specialized electrical equipment).
Such detailed profiles underscore how stealer logs empower identity theft and targeted phishing campaigns.
New Tools for Organizations
HIBP introduced two APIs to help organizations mitigate risks:
- Domain Search: Allows domain owners (e.g., companies using “@example.com”) to retrieve all email aliases and associated websites from the breach1.
- Website Operator Search: Lets services like Netflix identify compromised customers by querying their domain.
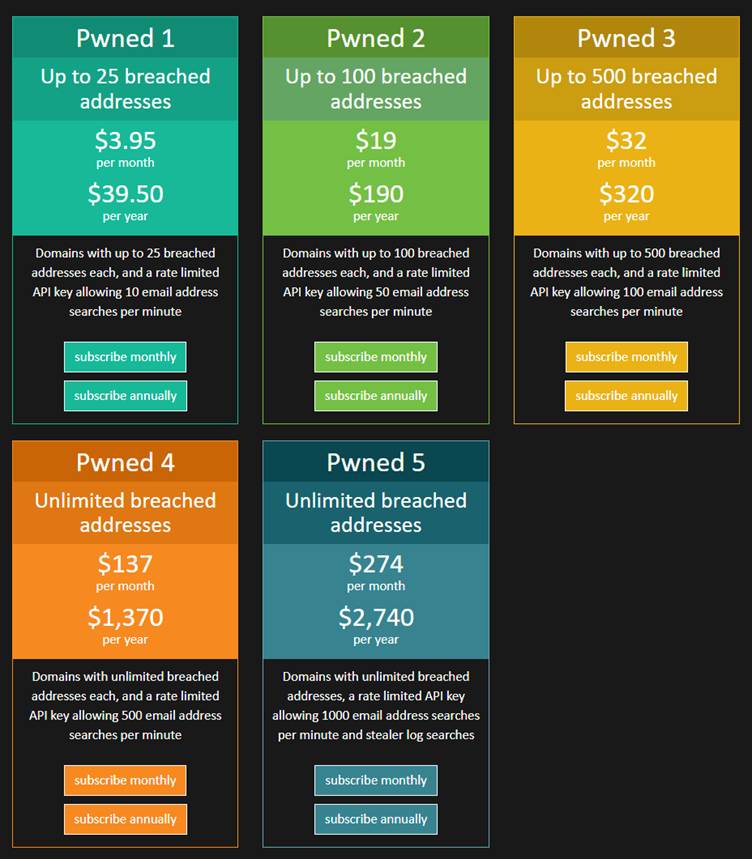
These tools, available under HIBP’s Pwned 5 subscription tier, aim to streamline incident response.
For instance, a corporation could scan its entire domain in one API call rather than thousands of individual email checks.
Password Database Expansion
The update adds 244 million previously unseen passwords and updates prevalence counts for 199 million existing entries in HIBP’s open-source Pwned Passwords database.
Queried 10 billion times monthly, this service helps platforms reject compromised passwords during sign-up flows.
Notably, patterns like “tender-kangaroo” and variants highlighted attackers’ use of memorable phrases—a trend password policies must address.
Technical and Operational Challenges
Processing 1.5TB of raw logs required custom .NET tools and SQL Azure, trimming 23 billion rows to 493 million unique pairs.
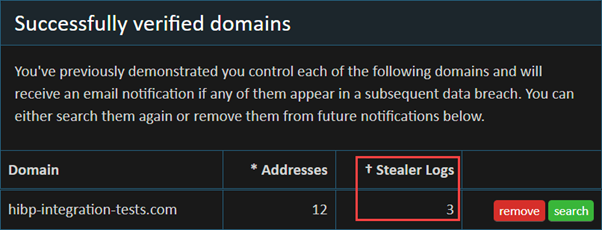
Hunt emphasized the inefficiency of cloud-based processing for such volumes, ultimately relying on local hardware to reduce costs. The effort reflects growing infrastructure demands as breach sizes escalate.
HIBP urges individuals to:
- Check email exposure via its free notification service.
- Use password managers and enable multi-factor authentication.
- Avoid pirated software, a common malware vector.
Organizations should adopt HIBP’s APIs to monitor domain exposures and audit compromised credentials.
With stealer logs becoming a primary breach vector, proactive defense is critical to disrupting attackers’ “second exploitation” phase.
Today’s update reinforces HIBP’s role in translating breach data into actionable intelligence—helping individuals and enterprises stay ahead of cybercriminals.
As Hunt noted, “The cloud isn’t always the answer,” underscoring the blend of ingenuity and pragmatism needed to secure the digital ecosystem.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



.png
)
