The HELLCAT ransomware group has claimed responsibility for a significant data breach at Jaguar Land Rover (JLR), exposing vast amounts of sensitive data including proprietary documents, source codes, employee information, and partner details.
This attack follows a pattern previously observed against prominent companies like Telefónica, Schneider Electric, and Orange, highlighting the group’s reliance on exploiting compromised employee credentials, specifically those harvested from Atlassian Jira instances.

The Breach
At the core of this breach is a technique that has become increasingly effective: using infostealer malware to steal credentials, which are then used to infiltrate critical corporate systems.
In this case, the compromised credentials belonged to an LG Electronics employee who was infected by an infostealer and had access to JLR’s Jira server.

The attack allowed the threat actor, known as “Rey,” to leak hundreds of internal files from JLR.
Hudson Rock, a cybersecurity firm tracking infostealer infections, noted that thousands of companies have Jira-related compromised credentials from such infections.
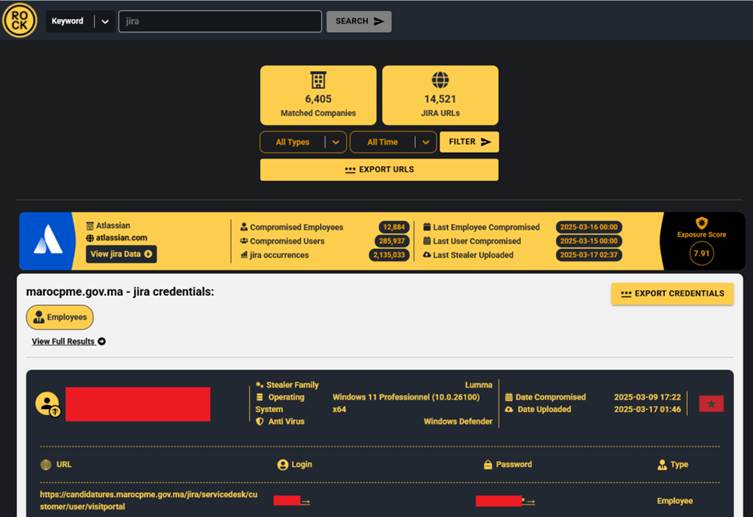
The firm’s database of over 30 million infected computers underscores the widespread nature of this threat.
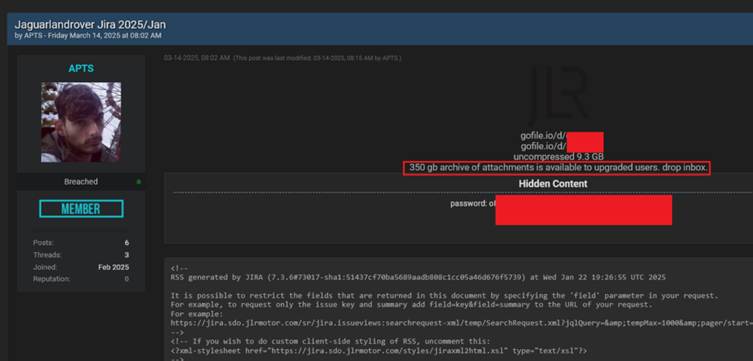
Days after Rey’s initial announcement, a second threat actor, operating under the alias “APTS,” emerged, claiming to have exploited similar credentials from 2021 to access JLR’s systems.
This led to an even larger data exfiltration, estimated at 350 gigabytes. APTS shared screenshots of a Jira dashboard, displaying additional sensitive data and confirming that the credentials used matched those in Hudson Rock’s database.
The Attack Method: Infostealers and Jira
HELLCAT’s modus operandi involves the silent infection of employee devices through phishing emails, malicious downloads, or compromised websites.
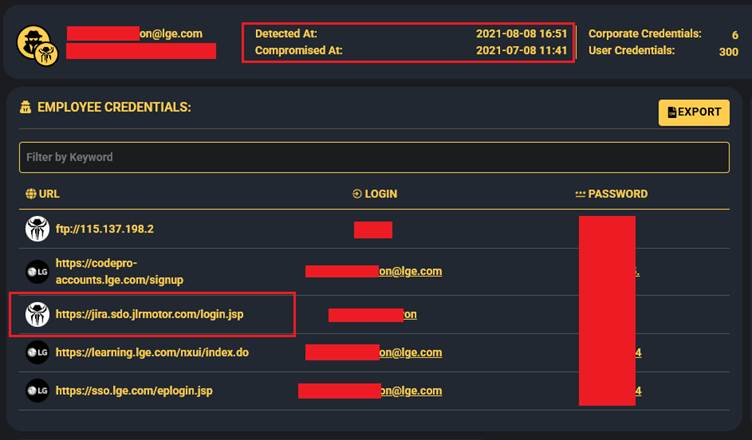
Once embedded, the infostealer malware like Lumma (implicated in the Schneider Electric breach) extracts sensitive login credentials for corporate systems, which are then sold or traded on the dark web.
In the JLR breach, following Rey’s confirmation of the Atlassian Jira instance as the entry point, it became clear how easily these stolen credentials can be used to escalate privileges and extract sensitive data.
A Credential Time Bomb
What makes the JLR breach particularly alarming is the age of the compromised credentials. Hudson Rock had previously identified these stolen login details as part of its vast database.
The fact that these credentials remained valid and unchanged within JLR’s systems highlights a critical oversight in managing and rotating corporate credentials.
The breach demonstrates the long-lasting threat posed by infostealer malware.
It joins a string of high-profile attacks (Telefónica, Schneider Electric, and Orange) that show how such infections can facilitate social engineering, blackmail, and AI-amplified leaks.
JLR’s case illustrates the enduring danger of unaddressed legacy credentials.
For organizations, the lesson is clear—infostealer infections are not isolated incidents but ongoing threats.
Credentials harvested can remain viable for years unless robust monitoring, multi-factor authentication (MFA), and timely credential rotation are implemented.
Atlassian Jira, critical in enterprise workflows, has become a prime target due to its centrality in data storage. Threat actors like HELLCAT can easily escalate privileges and extract data once inside.
As JLR assesses the damage and secures its systems, the cybersecurity community prepares for potential follow-up attacks. The leaked data could fuel targeted phishing campaigns or intellectual property theft, especially with AI tools capable of amplifying the impact of such breaches.
Given HELLCAT’s success, copycat operations are likely, with infostealer credentials remaining highly sought after on the dark web.
This incident serves as a stark reminder of the importance of proactive cybersecurity measures, including robust credential management and the integration of cybercrime intelligence APIs to enhance existing cybersecurity solutions.
For organizations seeking to protect against imminent intrusions due to info-stealer infections, Hudson Rock offers solutions to enrich cybersecurity solutions with its cybercrime intelligence API.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
