The revival of the LightSpy malware campaign has been observed, focusing on Indian Apple device users.
This sophisticated mobile spyware, suspected to have origins in China, is being used for espionage, targeting a select group of individuals, including journalists, activists, politicians, and diplomats across Southern Asia.
The implications of such targeted attacks are vast, raising alarms about potential geopolitical motives behind the campaign.
Technical Details of the Attack:
Infection Vector: The initial infection is believed to have occurred through compromised news websites featuring content related to Hong Kong.
Visitors to these sites unknowingly download the malware, initiating the infection process.
Weaponization: Upon infection, a first-stage implant gathers device information and facilitates the download of further stages, including the core LightSpy implant and various plugins.
AI-Powered Protection for Business Email Security
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by other email security solutions. .
These plugins are designed for specific spying functions, enhancing the malware’s ability to gather sensitive data from the infected device.
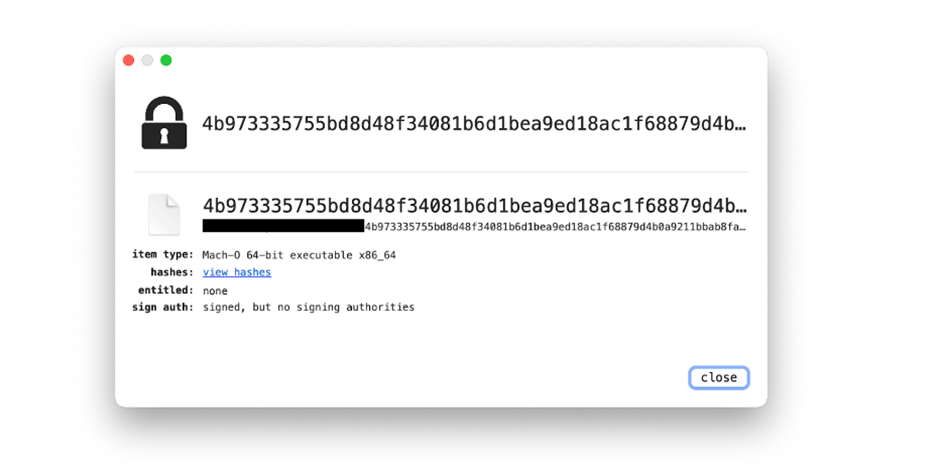
Hashes (md5, sha-256):
- 4b973335755bd8d48f34081b6d1bea9ed18ac1f68879d4b0a9211bbab8fa5ff4
- 2178d673779605ffb9cf7f2fa3ec8e97
File Information:
- File Name: None
- File Size: 430816 bytes
- File Type/Signature: Mach-O64
Blackberry’s recent blog post highlights the resurgence of the espionage campaign, LightSpy.
This campaign is targeting Southern Asia, with a possible focus on India.
Execution Chain
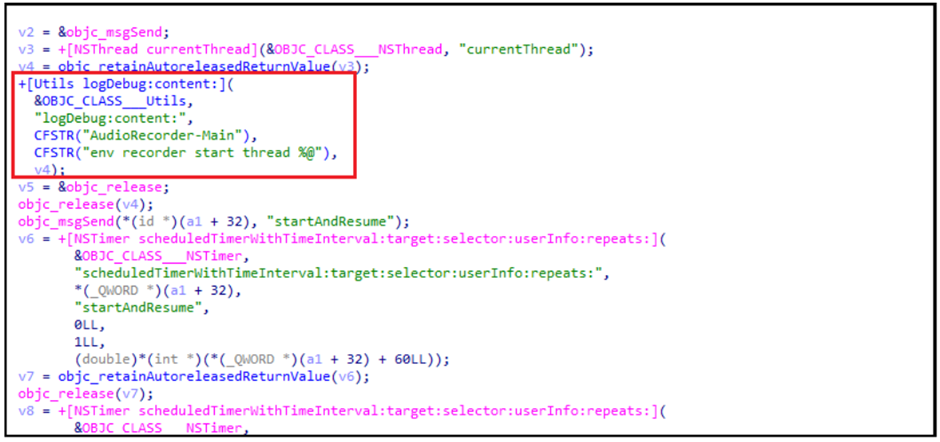
The execution begins with a Loader, which loads the encrypted and decrypted LightSpy kernel.
This kernel acts as a complex espionage framework, capable of supporting various plugins for extended functionality.
These plugins are securely retrieved from the attacker’s server, decrypted, and executed within the system.
Hashes (md5, sha-256):
- 0f66a4daba647486d2c9d838592cba298df2dbf38f2008b6571af8a562bc306c
- 59ac7dd41dca19a25a78a242e93a7ded
File Information:
- File Name: C40F0D27
- File Size: 1252656 bytes
- File Type/Signature: Mach-O64
The F_Warehouse framework underpins LightSpy and offers many capabilities, including file exfiltration, audio recording, network surveillance, user activity tracking, application inventory, image capture, access to credentials, and device enumeration.
LightSpy Capabilities
One of LightSpy’s more invasive features is its ability to covertly record audio through the device’s microphone, capturing private conversations and surrounding sounds.
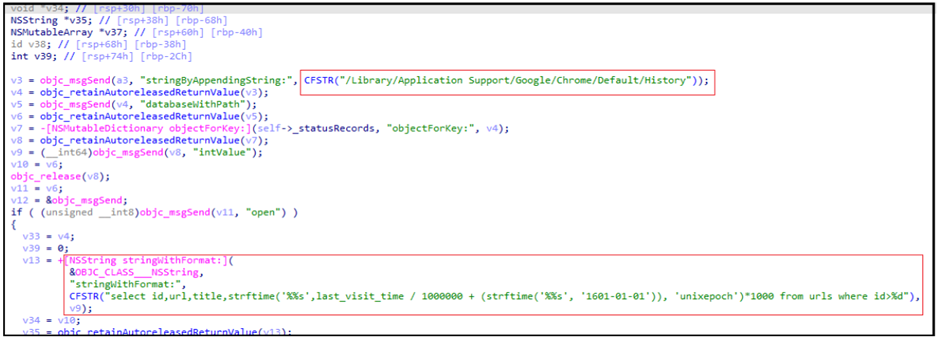
LightSpy meticulously tracks the browsing history of both Safari and Google Chrome, providing attackers with detailed insights into the victim’s online activities.
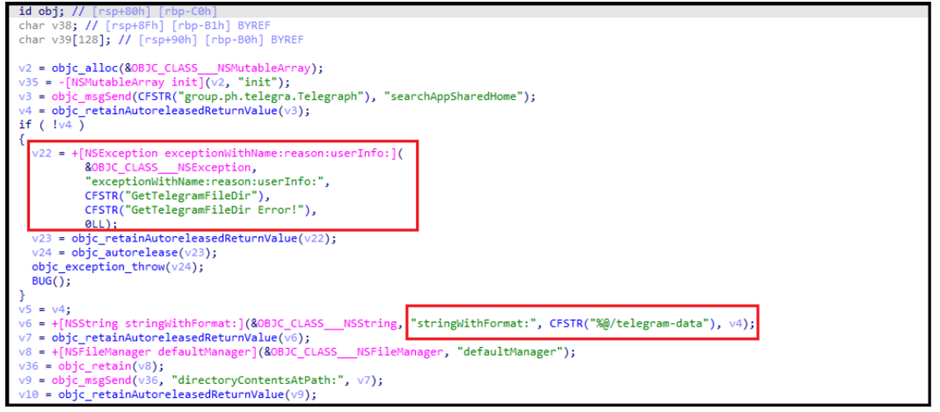
The malware explicitly targets data from popular messaging applications like Telegram, QQ, and WeChat, aiming to intercept private communications and gather sensitive information.
Shell Command Execution
Beyond data exfiltration, LightSpy can execute shell commands received from the attacker’s server, potentially allowing complete control over the compromised device.
The presence of comments in Chinese within the plugin code suggests that the developers behind LightSpy are native Chinese speakers, hinting at the involvement of state-sponsored actors.
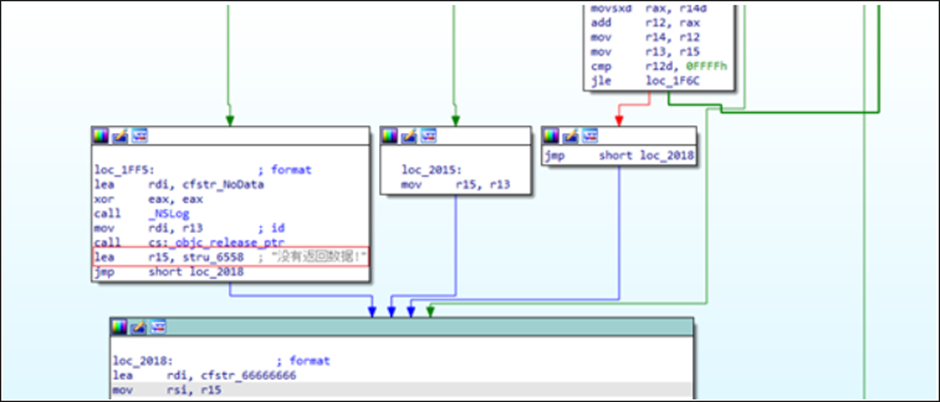
LightSpy communicates with a server at hxxps://103.27[.]109[.]217:52202, which hosts an administrator panel accessible on port 3458.
The return of LightSpy, maintained by the “F_Warehouse” framework, marks a significant escalation in mobile espionage threats.
The expanded capabilities of this malware pose a severe risk to individuals and organizations in Southern Asia.
The evidence pointing towards Chinese-speaking developers specifically targeting individuals potentially involved in sensitive activities underscores the need for increased vigilance and robust security measures.
Understanding the tactics and techniques employed by LightSpy is crucial in mitigating its impact and protecting sensitive information.
Looking to Safeguard Your Company from Advanced Cyber Threats? Deploy TrustNet to Your Radar ASAP.
.webp?w=696&resize=696,0&ssl=1)


.png
)
