Skidmap is a recent sample of the Linux malware that loads malicious kernel modules to hide it’s Cryptocurrency mining activities by faking network traffic and CPU usage.
The malware not only generates Cryptocurrency, but it also set’s up a secret master password on the infected system, which gives attackers complete system access.
Security researchers from Trend Micro observed the Linux Malware, Skidmap. According to their analysis of the malware, “it loads kernel-mode rootkits are not only more difficult to detect compared to its user-mode counterparts — but attackers can also use them to gain unfettered access to the affected system.”
Linux Malware Skidmap Infection Chain
The malware install’s through crontab, a utility used in Unix-like machines to schedule the job to run at regular time intervals. Upon installation, it downloads multiple binaries to the infected machine which affects the machine’s security settings.
Skidmap also set’s up backdoor access to the machine, besides backdoor, it creates another way also to gain unrestricted access to the system by setting a master password, which let attackers log in the system as any user.
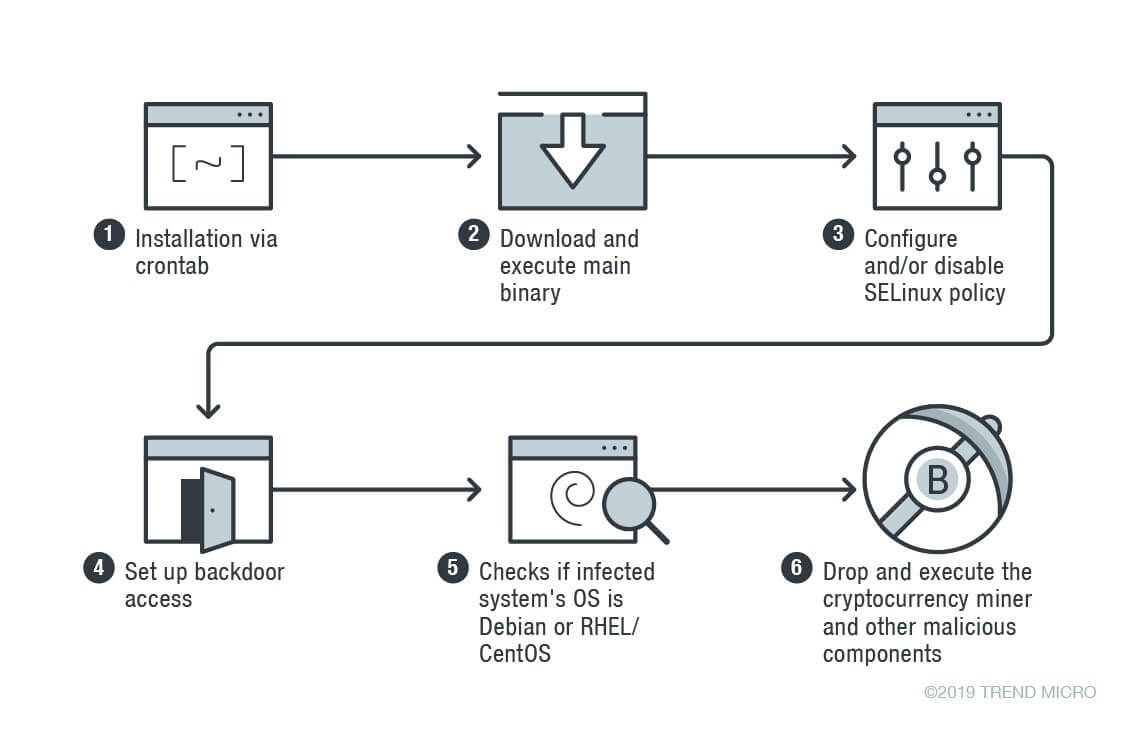
If the binary checks determine the infected system using Debian or RHEL/CentOS, then it drops cryptocurrency miner and additional components depend upon the operating system.
Notable Malicious Components
The Linux malware includes malicious components to evade its malicious activities and ensure they continue to run them in the infected machine.
A fake “rm” binary – Set’s malicious corn job task to download and execute a file.
kaudited – Drops Kernel modules and watchdog component to monitor the cryptocurrency miner file and process.
iproute – Used to hide files and fake network traffic.
netlink – Fakes network-related statistics and CPU-related statistics.
When compared with other malware, Skidmap employes advanced method to remain undetected and creates multiple ways for attacks to connect with the infected machine.
EvilGnome is yet another Linux malware observed recently with the capabilities of creating a backdoor and spying the Linux desktop users.
Indicators of Compromise
c07fe8abf4f8ba83fb95d44730efc601ba9a7fc340b3bb5b4b2b2741b5e31042
3ae9b7ca11f6292ef38bd0198d7e7d0bbb14edb509fdeee34167c5194fa63462
e6eb4093f7d958a56a5cd9252a4b529efba147c0e089567f95838067790789ee
240ad49b6fe4f47e7bbd54530772e5d26a695ebae154e1d8771983d9dce0e452
945d6bd233a4e5e9bfb2d17ddace46f2b223555f60f230be668ee8f20ba8c33c
913208a1a4843a5341231771b66bb400390bd7a96a5ce3af95ce0b80d4ed879e
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.



.png
)
