Security researchers discovered a new Mac malware Shlayer spreading through Google poisoned search results. The malware distributed masqueraded as a fake Adobe Flash Player installer (.DMG disk image).
The malware installer and its payload had a 0/60 detection rate among all antivirus engines on VirusTotal.
Mac Malware Shlayer
Intego researchers observed this newly updated Shlayer malware delivered as a Trojan horse file (.DMG disk image) masqueraded as an Adobe Flash Player.
Once the user installs the malicious Flash Player on Mac machine the image will get the mount and display instructions on how to install it.
“The instructions tell users to first “right-click” on the flash installer and select Open, and then to click Open in the resulting dialog box,” reads Intego blog post.
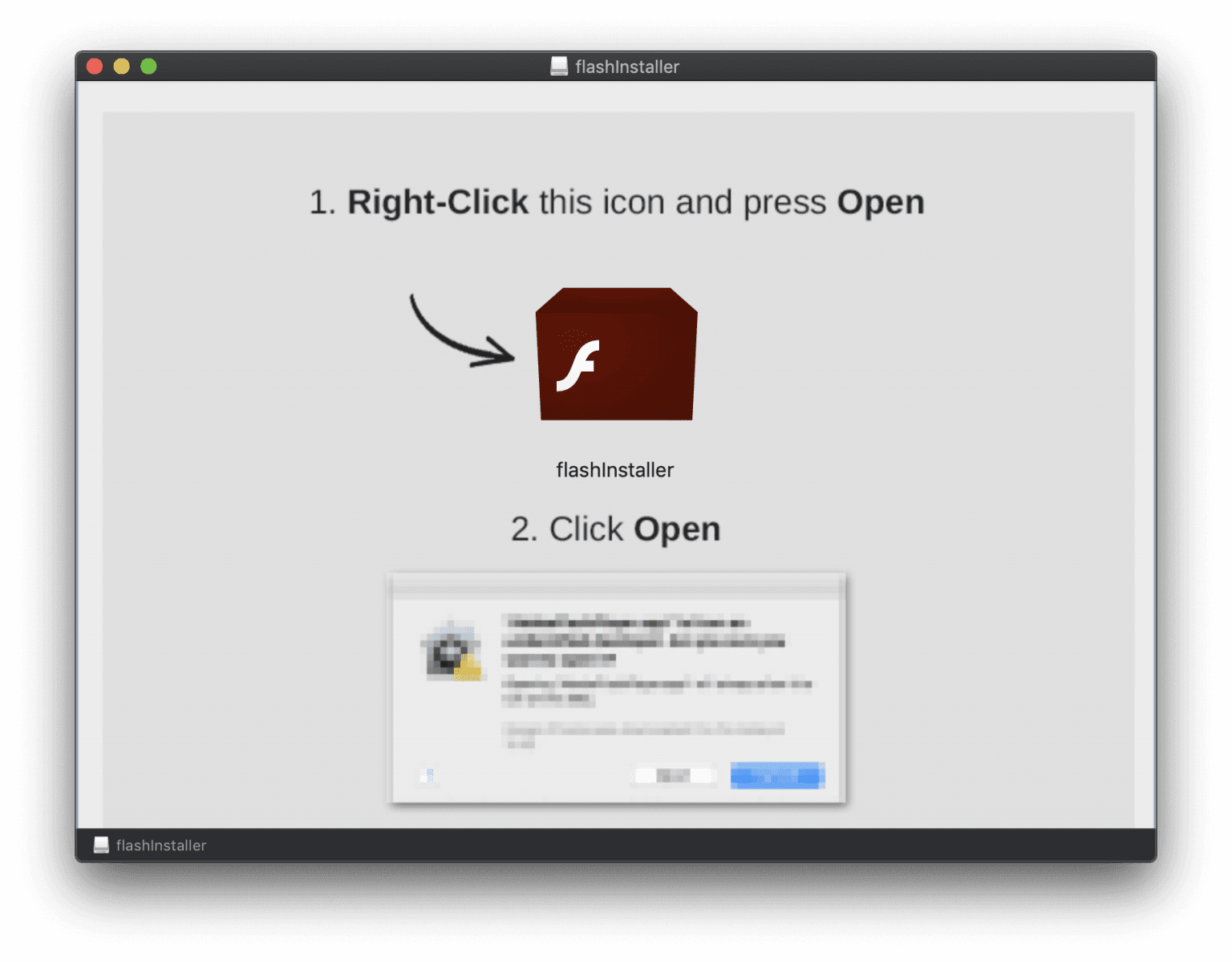
When the user starts following the instruction to installing the malicious application, the icon looks like a Flash player, but in the background, the bash shell script executed the opening terminal.
The bash script extracts password-protected .zip archive file which has a malicious app bundle, it stores the malicious app into a hidden temporary folder.
The malicious app also downloads the legitimate, Adobe-signed Flash Player installer to trick the user, but the hidden Mac app downloads malicious apps.
“The developers’ decision to hide the Mac .app within a password-protected .zip file, and to hide that within a bash shell script, is a novel idea—and it is also extremely clear evidence that the developers are trying to evade detection by antivirus software.”
“This newly re-engineered malware purports to be a legitimate Flash Player installer, but it can surreptitiously download and install additional unwanted packages containing adware or spyware.”
Shlayer malware believed to be the most widespread macOS threat, earlier this February Carbon Black researchers spotted new Shlayer malware targeting 10.10.5 up to 10.14.3.
Adobe already announced that they will stop distributing and updating Flash Player after 31 December 2020 (“EOL Date”).
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Also Read
Does Your Mac Need Antivirus Protection? Here’s What You Need to Know



.png
)
