More than 30 malicious fleeceware apps found in Apple’s official App Store. These apps are aimed to make financial frauds.
Apple allows apps to offer a trial period and these app developers taking it as an advantage.
If the users install the app and don’t cancel the subscription they use to charge an excessive amount.
Fleeceware Apps Apple’s App Store
Sophos observed 30 such apps present in Apple’s official App Store and these apps charge subscription between $30 per month or $9 per week after a 3- or 7-day trial period.

If the apps remain installed for more than a year they charge users $360 or $468, respectively. This apps doesn’t include any special features. It includes only the features that present in free apps or other normally paid apps.

The app types include image editors, horoscope/fortune-telling/palm readers, QR code/barcode scanners, and face filter apps,
Many of these apps are advertised as free in App Stores if the users installed it pop with a “free trial” notification.
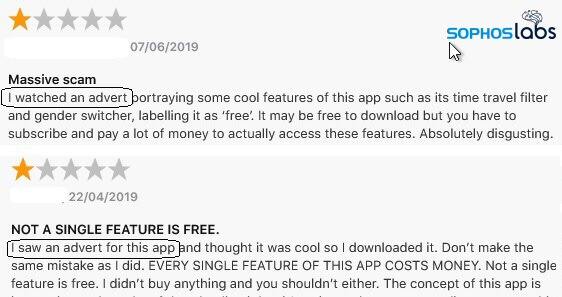
The notifications ask users to provide payment card details, in most cases, the apps are usable only after enrolling for a subscription.
“Some users may sign up to subscribe without reading the fine print, which includes the actual cost of the subscriptions,” reads Sophos blog post.
Apple store doesn’t keep count of how many users installed the app, many of these apps found to be in the list of the top popular apps list.
Earlier Sophos observed several Fleeceware apps on Google play store that cause monetary damage to users. these apps found to be installed more than 600 million times in total.
In those, some of the apps found transferring the text typed by the users to the servers located in China.
These malicious apps gaining popularity by advertising with various popular platforms like Facebook, Instagram, TikTok, and other sources.
Also, these apps have a high number of five-star reviews, in some way the app developers manipulated the reviews.
Here you can find the complete list of the Malicious Fleeceware Apps.



