A new endpoint detection and response (EDR) evasion technique has been identified that allows attackers with low-privilege access to bypass detection and operate under the radar.
Unlike traditional evasion methods that require high privileges, this method exploits masquerading to deceive event monitoring systems, such as Sysmon or Security Information and Event Management (SIEM) platforms, without raising alarms.
EDR solutions are designed to detect and respond to potential threats. These systems rely heavily on process creation events and the legitimacy of file paths to distinguish between routine and malicious activities.
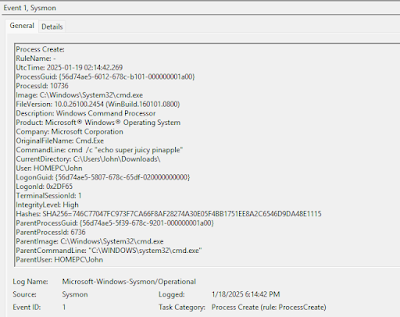
However, this novel approach demonstrates how attackers can bypass detection using only a standard user account, eliminating the need for elevated privileges.
By utilizing a technique known as Path Masquerading, attackers are able to disguise malicious payloads to mimic legitimate system processes, specifically targeting the Antimalware Service Executable (MsMpEng.exe) associated with Windows Defender.
Path Masquerading in Action
The method hinges on exploiting Unicode characters that resemble whitespace (e.g., En Quad, Em Quad, or Hair Space) to create deceptive file paths. Here’s how it works:
- Creating a Spoof Directory:
- With low privileges, attackers begin by creating directory structures such as “C:\Program Files 00” where they have fully read/write/execute permissions.
- They then rename the directory to resemble a legitimate system path using Unicode characters, e.g., “C:\Program[U+2000] Files.”
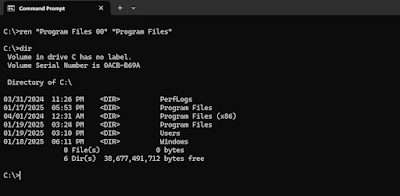
- Cloning Windows Defender Path:
- The legitimate folder structure of Windows Defender—C:\Program Files\Windows Defender—is mirrored into the newly created masqueraded path.
- A malicious executable, such as “SuperJuicy.exe,” is dropped into the cloned path.
- Execution and Deception:
- Once executed, tools like Sysmon log the event but only display the visual path “C:\Program Files\Windows Defender,” making it nearly indistinguishable from a legitimate execution path.
- This completely cloaks the attacker’s malicious payload under the guise of legitimate antivirus processes, throwing off investigators.
The potential impact of this attack method is significant. By disguising payloads as legitimate system processes, analysts may be misled to focus investigations on trusted system tools like Windows Defender, as per a report by Zero Salarium.
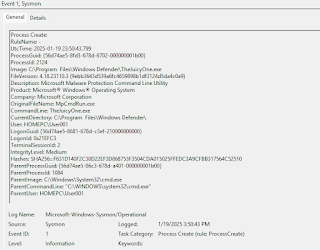
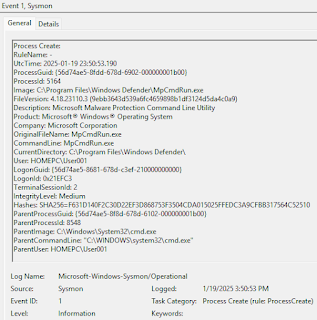
This not only delays detection and remediation but also provides attackers with more time to execute their objectives undetected.
To further escalate the attack’s effectiveness, the technique can be combined with DLL hijacking or side-loading, enhancing its ability to bypass defenses.
Defending Against Path Masquerading
Defending against this sophisticated evasion method requires proactive measures by administrators:
- Enhanced Logging Rules: Monitor paths containing Unicode whitespace characters.
- Modified Log Display: Adjust log-viewing tools to reveal hidden characters (e.g., “Program[En Quad]Files”).
- Access Restrictions: Limit folder creation permissions in critical directories such as “C:” to prevent unauthorized file paths.
The discovery of this new evasion technique highlights the evolving tactics used by attackers to bypass EDR solutions.
By leveraging low-privileged access and innovative path manipulation methods, this approach makes detection significantly more challenging.
Organizations must adapt by implementing more advanced monitoring and restricting permissions to critical system paths to protect against such stealthy attacks.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free



.png
)
