A recent snag in Google’s Chrome distribution process has left Windows users unable to install the browser on their Intel and AMD systems.
The issue, first reported by Windows Latest on March 25, arises when users attempt to run the ChromeSetup.exe file, only to be met with the error message: “This app can’t run on your PC: To find a version for your PC, check with the software publisher.”
This glitch is not attributed to any intentional block by Microsoft but rather an oversight on Google’s part.
It appears that Google inadvertently shipped an ARM version of the Chrome installer, which is incompatible with the majority of Windows systems that run on Intel and AMD processors.
Cause of the Error
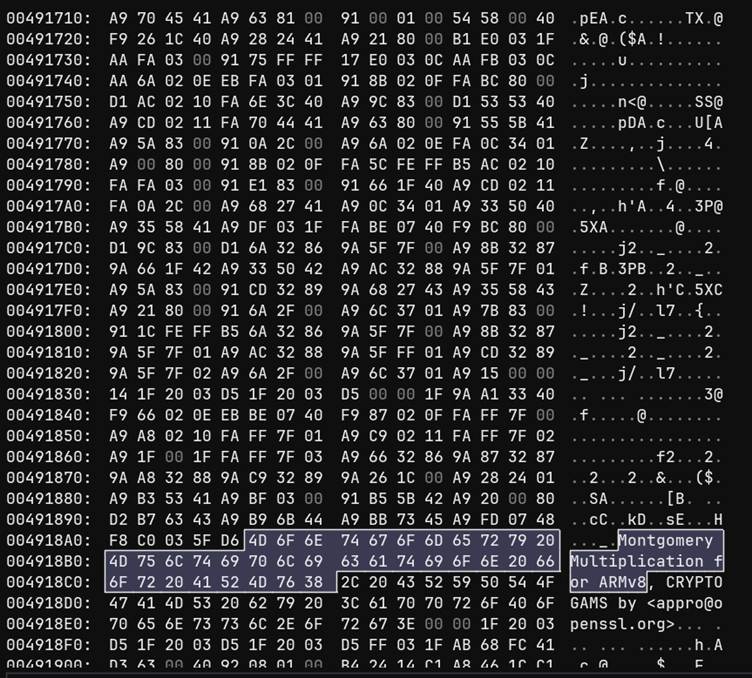
The problem became evident when the ChromeSetup.exe file was analyzed, revealing references to “Montgomery Multiplication for ARMv8,” a cryptographic routine often used in encryption protocols.
This code snippet confirms that the installer was built for ARM-based devices, such as those equipped with Snapdragon processors.
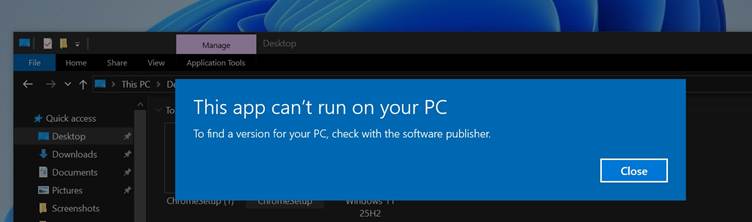
Consequently, when users try to install Chrome on their x64 systems, Windows detects a compatibility issue and prevents the app from running.
The error affects anyone attempting to install Chrome directly from Google’s official website via the downloadable ChromeSetup.exe file.
Users are then left with no option but to click “close” when encountering the compatibility error, as Windows offers no workaround for this issue.
Solution for Users
For individuals seeking to install Chrome immediately, Google offers an alternative solution through its offline installer.
These offline installers are unaffected by the glitch and can be downloaded from Google’s official website. By using these installers, users can circumvent the current issue and successfully set up Chrome on their Windows 10 and 11 systems.
In summary, the Chrome installation problem is an unintended consequence of Google’s distribution mishap rather than any sabotage by Microsoft.
Users can navigate this issue by utilizing the offline installers until Google rectifies the problem with the standard online installer.
Steps to Install Chrome Using Offline Installer
- Visit Google’s Download Page: Go to Google’s Chrome download page using a different browser like Microsoft Edge.
- Download Offline Installer: Look for the option to download the offline installer. This might involve clicking on more download options.
- Run Offline Installer: Once the offline installer is downloaded, run the file and follow the on-screen instructions to complete the installation.
By following these steps, users can bypass the current compatibility issue and ensure they have Chrome up and running on their Windows systems.
Are you from SOC/DFIR Teams? – Analyse Malware, Phishing Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
