Cybersecurity experts have uncovered a new exploit leveraging the widely used Remote Desktop Protocol (RDP).
This vulnerability enables attackers to gain unauthorized control over Windows systems and hijack browser activity, posing a significant threat to individual and enterprise data security.
Details of the Exploit
The exploit arises from the improper handling and storage of RDP bitmap cache files, which are designed to enhance performance during remote desktop sessions.
These files store fragments of on-screen activity, such as graphical elements and screen data, on the client’s local machine.
While intended for performance optimization, malicious actors have now weaponized this feature to gain unprecedented insights into active Windows sessions and web browsing activities
.By analyzing bitmap cache files stored on the initiating machine, attackers can reconstruct portions of the remote session’s screen.
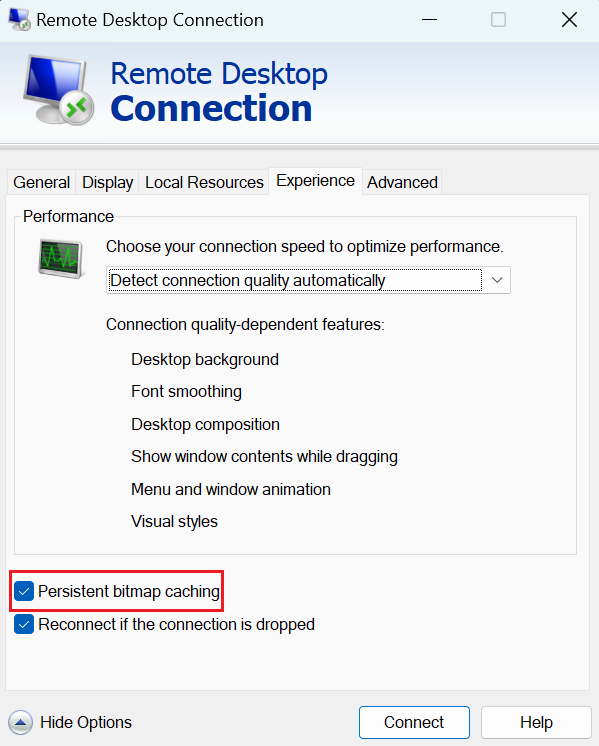
Persistent bitmap caching is enabled by default in mstsc.exe
This includes opened applications, executed commands, private browser sessions, and sensitive user activities like accessing login pages or downloading files.
With additional tools, such as BMC-Tools (developed by France’s cybersecurity agency ANSSI) and RdpCacheStitcher, attackers can piece together the graphical fragments into actionable intelligence.
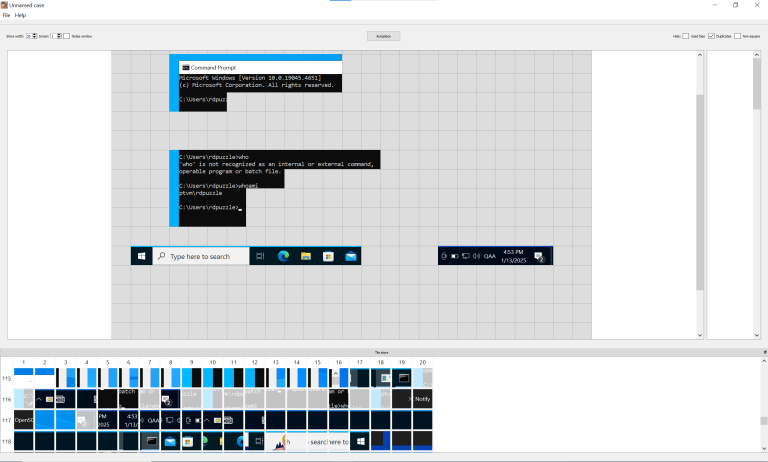
Researchers who explored this exploit compared it to virtually “looking over the shoulder” of the target user. In one real-world example, attackers successfully reconstructed RDP session frames to view:
- Terminal commands executed by the user, such as certutil.exe used to download malicious scripts.
- Private browser sessions, including login pages and sensitive credentials.
- File system activities, such as copying files like “svchost.exe” to local directories.
This level of insight not only compromises user privacy but also provides attackers with detailed information to escalate their privileges and deepen their foothold within compromised networks.
How the Exploit Works
The exploit hinges on the functionality of RDP bitmap cache files, which persist across multiple sessions.
These files are stored locally on the client machine and contain cached graphical elements transferred during screen rendering. For instance, cache files like Cache0000.bin on Windows systems store 64×64-pixel bitmap fragments in a fixed format.
By extracting and collating these fragments, attackers can infer user activities, such as opened applications, commands executed in terminal windows, and websites accessed via browsers. The exploitation tools work as follows:
- Bitmap Extraction: Tools like BMC-Tools extract persistent graphical fragments from cache files.
- Session Reconstruction: Software such as RdpCacheStitcher reassembles the fragments into partial or complete reconstructions of the user’s screen during the remote session.
Potential Targets and Impact
The exploit is particularly dangerous for organizations. Administrators using RDP to manage multiple machines create an extensive web of sensitive connections, all of which may be vulnerable if an attacker gains access to the initiating machine.
In one incident, attackers used this exploit to target service providers remotely managing client systems, spreading malware and exfiltrating sensitive credentials.
While ordinary users are also at risk, the highest impact is seen in enterprise environments where RDP is essential for IT operations.
Malicious actors can use the reconstructed data to conduct phishing attacks, spread ransomware, or simply monitor sensitive activities untraceable.
To mitigate the risks posed by this exploit, cybersecurity experts recommend the following measures:
- Disable Persistent Bitmap Caching: RDP clients (such as mstsc.exe) allow users to disable bitmap caching, minimizing the exposure of session data.
- Strengthen Network Security: Employ Virtual Private Networks (VPNs) and robust firewalls to secure RDP connections from external threats.
- Monitor RDP Sessions: Log and monitor RDP sessions for suspicious activity, including unexpected outgoing connections or file movements.
- Restrict Privileges: Implement the principle of least privilege to limit unnecessary RDP usage.
- Apply Updates: Regularly update Windows systems and security patches to prevent exploitation of known vulnerabilities.
According to the Insinuator blogs, the discovery of this exploit underscores the dual-edged nature of convenience-centric technologies like RDP.
While essential for remote access and network management, their misuse can create significant security vulnerabilities.
This incident also highlights the importance of forensic tools in identifying and mitigating emerging threats.
As organizations increasingly pivot towards remote and hybrid working models, securing RDP connections must remain a top priority. Experts warn that failure to address these vulnerabilities promptly could exacerbate the damage from future cyberattacks.
Collect Threat Intelligence with TI Lookup to improve your company’s security - Get 50 Free Request



.png
)
