Phishing attacks have surged nearly 40% in the year ending August 2024, with a significant portion of this increase linked to new generic top-level domains (gTLDs) like .shop, .top, and .xyz.
These domains, known for their minimal registration requirements and low costs, have become attractive to cybercriminals, according to new research by Interisle Consulting.
This trend raises concerns as the Internet Corporation for Assigned Names and Numbers (ICANN) continues to push forward with introducing even more gTLDs.
New gTLDs and Cybercrime
Interisle’s study highlights that while new gTLDs represent only 11% of the market for new domains, they accounted for 37% of reported cybercrime domains between September 2023 and August 2024.
Leveraging 2024 MITRE ATT&CK Results for SME & MSP Cybersecurity Leaders – Attend Free Webinar
The data, sourced from various anti-spam organizations such as the Anti-Phishing Working Group (APWG), suggests that these newer domains are increasingly favored by scammers.
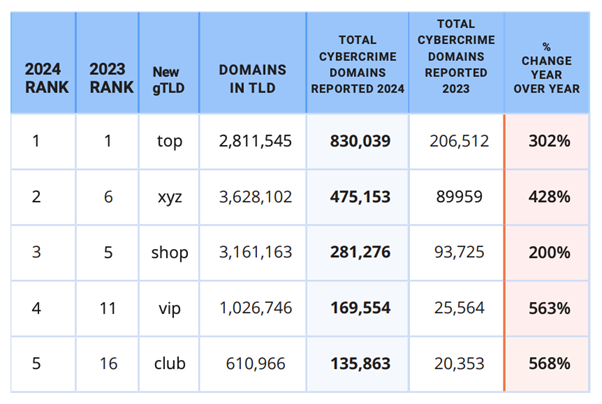
The allure of new gTLDs for criminals lies in their affordability and lack of stringent registration criteria.
Many of these domains are available for less than $2, contrasting sharply with the cheapest .com domains priced at $5.91.
This low cost of entry, combined with minimal oversight, allows phishers to purchase domains in bulk without significant investment.
John Levine, president of the Coalition Against Unsolicited Commercial Email (CAUCE), criticized ICANN’s approach, suggesting that the organization is acting more like a domain speculator trade association than a regulatory body.
He argues that without stricter registration policies, the introduction of new gTLDs will only further fuel cybercriminal activities.
Interisle’s report also noted a shift in phishing targets. Traditionally, large tech companies like Apple, Facebook, and Google were frequently impersonated.
However, the U.S. Postal Service emerged as the most-phished entity in the past year, driven in part by a cybercriminal known as Chenlun, who has developed phishing kits targeting postal services globally.
According to the Krebs On Security report, beyond gTLDs, phishers are increasingly using subdomain providers, such as blogspot.com and weebly.com, to host their attacks.
The report found over 1.18 million instances of phishing using subdomains—an increase of 114%. These platforms present unique challenges for mitigation, as blocking malicious activities at the root level could disrupt legitimate users.
The report concludes with recommendations for subdomain providers to limit mass account creation and enhance monitoring.
As ICANN continues with its plans to introduce new gTLDs, cybersecurity experts urge the implementation of stricter policies to prevent the misuse of these domains by cyber criminals.
Analyse Advanced Malware & Phishing Analysis With ANY.RUN Black Friday Deals : Get up to 3 Free Licenses.



.png
)
