Oracle Corporation has confirmed a data breach involving its older Gen 1 servers, marking its second cybersecurity incident disclosed in recent weeks.
This breach underscores vulnerabilities in legacy systems and raises concerns about the company’s ability to safeguard sensitive client data.
Details of the Breach
According to a Cyber Security News report, the breach was first reported by a threat actor known as “rose87168,” on Breachforums on March 20, 2025.
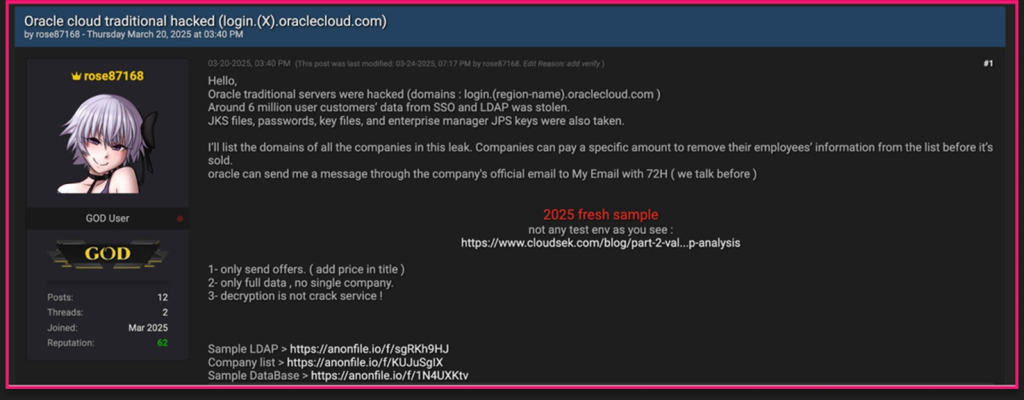
The attacker claimed access to approximately 6 million data records, including usernames, email addresses, hashed passwords, and sensitive authentication credentials such as Single Sign-On (SSO) and Lightweight Directory Access Protocol (LDAP) information.
Additionally, Java Key Store (JKS) files and Enterprise Manager JPS keys were exfiltrated. While no complete Personally Identifiable Information (PII) was exposed, Oracle confirmed that the compromised data is about 16 months old.
The hacker exploited a 2020 Java vulnerability to deploy malware and a web shell targeting Oracle’s Identity Manager (IDM) database.
The attacker reportedly gained access in January 2025 and remained undetected until late February, prompting Oracle to launch an internal investigation.
Oracle’s Response and Client Notifications
Oracle swiftly notified affected clients and reinforced security measures for its Gen 1 servers. The company emphasized that its Gen 2 servers and primary Oracle Cloud infrastructure remain unaffected.
It has reassured stakeholders that the breach was confined to legacy systems and took steps to mitigate the damage.
Despite Oracle’s assurances, cybersecurity firm CybelAngel reported that Oracle privately acknowledged unauthorized access to legacy systems.
The company is urging impacted clients to reset credentials, monitor for suspicious activity, and implement additional security measures to prevent further exploitation.
The attacker, “rose87168,” appears to be relatively new to the cybercrime scene, with their account created in March 2025.
Their primary motive seems to be financial extortion, as they demanded a $20 million ransom from Oracle. However, the hacker also expressed interest in exchanging stolen data for zero-day exploits, suggesting broader ambitions.
To substantiate their claims, “rose87168” released sample databases and LDAP credentials as proof. Security researchers validated portions of this data, confirming the breach’s authenticity.
This incident has drawn additional scrutiny over Oracle’s security measures given its recent history of similar cyberattacks.
Just weeks prior, Oracle disclosed another breach involving its Health division’s legacy Cerner servers, where patient data from U.S. healthcare organizations was compromised.
Although Oracle maintains these incidents are unrelated, the timing of the breaches has raised concerns about the company’s overall cybersecurity posture.
Experts warn that vulnerabilities in legacy systems, like the Gen 1 servers, pose significant risks if left unaddressed.
The incident underscores the challenges large enterprises face in securing outdated infrastructure while migrating to modern platforms.
Oracle’s response highlights the complexities of defending against evolving cyber threats and reinforces the need for comprehensive security measures in the face of increasingly sophisticated attacks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
