A new Mac malware dubbed OSX/Linker leverages the recently disclosed macOS’ Gatekeeper vulnerability to get executed on victim’s machine without user permission or warnings.
The MacOS X GateKeeper zero-day vulnerability was publically disclosed by Filippo Cavallarin on May 24, as the Apple missed its 90 days deadline to fix the vulnerability.
The vulnerability resides in how the Gatekeeper treats the apps that loaded from a network share and the Internet. Gatekeeper, by default, considers the apps loaded from external drives and network shares as safe locations and allows to run without user consent.
“As per-design, Gatekeeper considers both external drives and network shares as safe locations, and it allows any application they contain to run. By combining this design with two legitimate features of MacOS X, it will result in the complete deceivement of the intended behavior,” reads Filippo Cavallarin blog post.
Gatekeeper in apple is a mechanism to check for the presence of code signing certificates status and verifies the developer signature before allowing the application to execute.
OSX/Linker Malware
Intego’s malware research team noted few attempts of OSX/Linker to leverage the Zero-day flaw in macOS Gatekeeper by using a disk image file(.dmg) that used to distribute Mac software.
Anonymous users uploaded the samples to virustotal, Intego spotted four such samples, the first sample uploaded by an anonymous user from Israel, after that within seven minutes other three samples uploaded form United States.
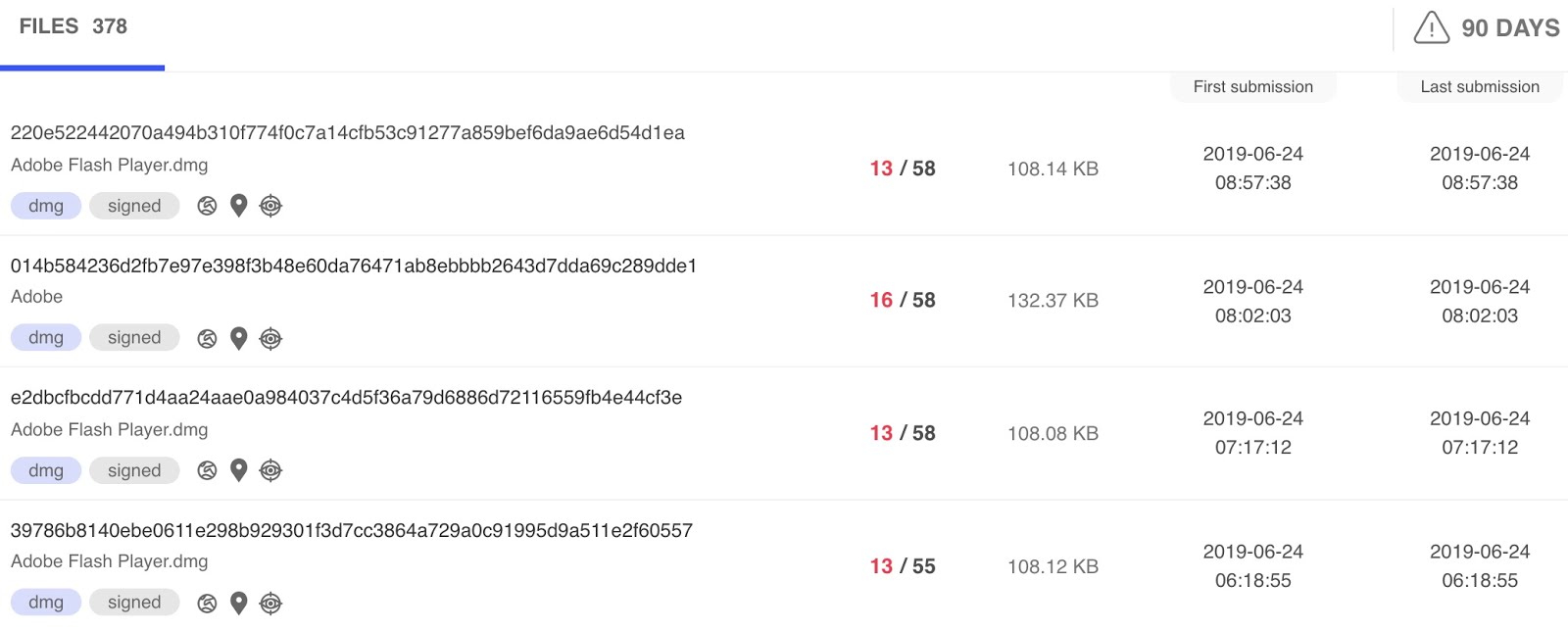
Intego believes all the files uploaded by the same user, possibly he forgot to mask the IP address for at the time of uploading the first sample. The IP referenced by the disk images’ symlinks has been taken down by hosting company or voluntarily.
“It is not clear whether any of these specific disk images were ever part of an in-the-wild malware campaign. It is possible that these disk images, or subsequent disk images, may have been used in small-scale or targeted attacks, but so far this remains unknown.”
As usual, the threat actors behind the campaign disguised the disk images as Adobe Flash Player installers to trick the Mac users.
The developer ID associated with the samples has been reported by Intego to Apple and the Apple to revoke the developer ID associated.
Network administrators are recommended to lock down their network to prevent NFS communications from external IP, and for home users, there is no fix until Apple releases a security update.
IoC
108.168.175.167:111 or 875, or TCP port 2049
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates also you can take the Best Cybersecurity course online to keep yourself updated.
Related Read
Memory Corruption Flaw in macOS Let Hackers run Malicious Code with Root Privileges
macOS Zero-Day Vulnerability Allows Hackers to Bypass Security Protections With Synthetic Clicks



.png
)
