The Open Web Application Security Project (OWASP) has released its updated Smart Contract Top 10 for 2025, providing essential insights for developers and security teams in the rapidly evolving Web3 environment.
This document outlines the most pressing vulnerabilities found in smart contracts, serving as a crucial resource for maintaining security and protecting against exploitation.
OWASP’s new release reflects changes in the landscape of smart contract security, informed by data from multiple authoritative sources, including SolidityScan’s Web3HackHub.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Overview of the OWASP Smart Contract Top 10 (2025)
The OWASP Smart Contract Top 10 (2025) categorizes vulnerabilities into ten key areas that developers must pay close attention to to enhance the security of their smart contracts. The updated list includes:
| Vulnerability Code | Vulnerability Name | Description |
| SC01:2025 | Access Control Vulnerabilities | Flaws that allow unauthorized access or modifications. |
| SC02:2025 | Price Oracle Manipulation | Exploitation of vulnerabilities in external data fetching for contract logic manipulation. |
| SC03:2025 | Logic Errors | Deviations from intended functionality affecting contract performance. |
| SC04:2025 | Lack of Input Validation | Insufficient checks allowing harmful inputs to disrupt contract behavior. |
| SC05:2025 | Reentrancy Attacks | Exploiting functions by re-entering before completion, leading to state changes or fund loss. |
| SC06:2025 | Unchecked External Calls | Failures in verifying the results of external calls can result in unintended consequences. |
| SC07:2025 | Flash Loan Attacks | Manipulations exploiting rapid multiple actions in single transactions to drain liquidity. |
| SC08:2025 | Integer Overflow and Underflow | Arithmetic errors causing serious vulnerabilities due to fixed-size integer limitations. |
| SC09:2025 | Insecure Randomness | Predictable random number generation leading to exploitation in sensitive functionalities. |
| SC10:2025 | Denial of Service (DoS) Attacks | Exploiting vulnerabilities to exhaust resources and render contracts non-functional. |
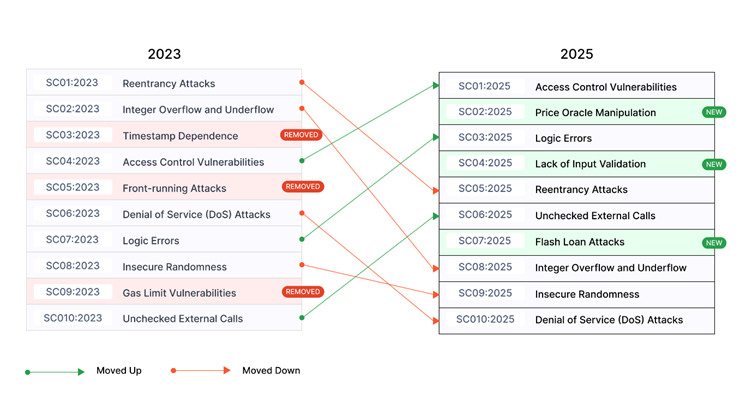
Changes from 2023 to 2025
The OWASP Smart Contract Top 10 has evolved to reflect the latest threats and vulnerabilities observed in the blockchain space.
The 2023 version has seen a reclassification and introduction of vulnerabilities based on recent attack data and trends:
- Reentrancy Attacks have been highlighted due to their prevalence in high-profile breaches.
- Flash Loan Attacks have been recognized as a significant threat in decentralized finance (DeFi) ecosystems.
- Access Control Vulnerabilities remain at the forefront, with notable financial impacts documented in the past year.
In 2024, the financial impact of vulnerabilities in smart contracts was staggering.
According to data from the SolidityScan’s Web3HackHub, the total losses amounted to $1.42 billion across 149 documented incidents. Below is a summary of the most impacted vulnerability categories:
| Vulnerability Type | Total Financial Loss (in USD) | Incident Count |
| Access Control Vulnerabilities | $953.2M | 45 |
| Logic Errors | $63.8M | 20 |
| Reentrancy Attacks | $35.7M | 15 |
| Flash Loan Attacks | $33.8M | 10 |
| Lack of Input Validation | $14.6M | 8 |
| Price Oracle Manipulation | $8.8M | 5 |
| Unchecked External Calls | $550.7K | 6 |
The OWASP Smart Contract Top 10 (2025) serves as a critical resource for developers within the Web3 ecosystem, emphasizing the need for rigorous testing and security measures against common vulnerabilities.
By integrating insights from various sources, including Kacherginsky’s “Top 10 DeFi Attack Vectors – 2024,” OWASP aims to provide a comprehensive framework for understanding and mitigating risks in smart contract development.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
