A new attack method dubbed PDFex that extracts the contents of encrypted PDF files in a plain text. All attacker needs are to have a single block of know plain text or the legitimate user needs to open the encrypted document.
PDF files are encrypted to exchange and store sensitive information without any additional mechanisms. The encryption key here is the PDF password, the recent version of PDF supports for the 256-bit AES encryption algorithm.
PDF encryption is used in several public and private sectors to protect sensitive information, this new attack focuses on vulnerabilities in PDF specification.
Researchers analyzed 27 popular PDF viewers, out of the 23 are vulnerable to direct exfiltration and all of them are vulnerable to CBC gadgets
Novel Attacks on PDF Encryption
Researchers developed two possible attack methods, exploiting the security limitations with PDF encryption based on active-attacker scenarios.
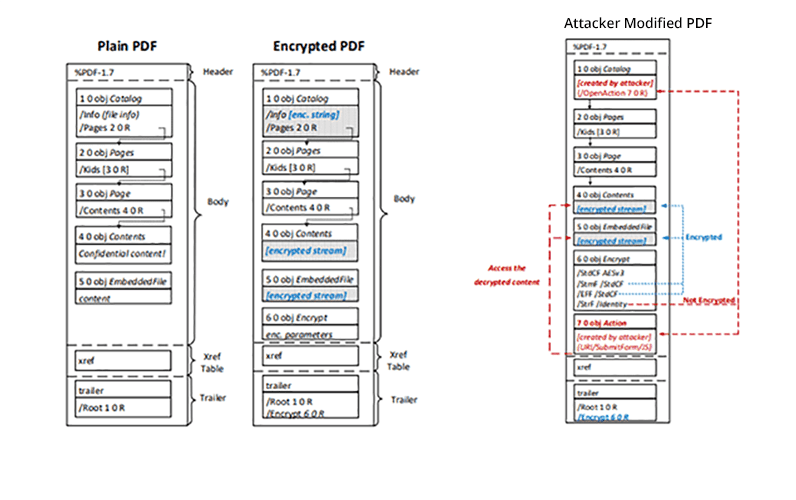
The first method involves abusing PDF feature, the attacker should gain access to the encrypted PDF. The encrypted PDF file contains both ciphertexts and plaintexts which allows an attacker to launch direct exfiltration attacks once the victim opens the file.
The second method based on Cipher Block Chaining (CBC), PDF encryption uses CBC with no integrity checks, this allows us to create self-exfiltrating ciphertext parts using CBC malleability gadgets and to modify the existing plain text or to create a new one.
PDFex Attacker Scenarios
It is assumed that attackers already having access to the PDF document, but they don’t know the password or the decryption keys.
What attacker can do is by modifying the encrypted files by changing the document structure or adding new unencrypted objects and they send the modified files to the victim. Researchers classified attack into two scenarios.

without user interaction – In this case, all attacker need is to just open the modified PDF file and displays the PDF document.
with user interaction – In this attack scenario the victim needs to interact with the PDF document (just a mouse click).
The attack is successful if they extract complete data as plain text from encrypted PDF or parts of the data from the encrypted PDF file.
To note that the PDFex attack won’t allow the attacker to remove or to know the password, instead it allows attackers to read the data from the encrypted file.
Data Exfiltration
This section describes how the data is exfiltrated with Direct Exfiltration and CBC Gadgets method.
Direct Exfiltration (Attack A)
With is attack type, attacker abuses the flexibility in PDF encryption that allows ciphertext and plaintext elements. An attacker can modify the PDF structure to add unencrypted elements that are controlled by the attacker.

This action can be in three possible ways
- Submit a form
- Invoke a URL
- Execute JavaScript
This document later sends by attackers to the victim and the data leak HTTP request leaks the full data in plaintext automatically to the attacker’s server once the victim opens the file.
CBC Gadgets (Attack B)
“PDF encryption generally defines no authenticated encryption, attackers may use CBC gadgets to exfiltrate plaintext. The basic idea is to modify the plaintext data directly within an encrypted object”, reads the paper.

Two launches the attack, the attacker needs to satisfy two preconditions.
Know Plain Text: To manipulate the encrypted the attacker should know parts of the plaintext is necessary.
Exfiltration channel: The attacker should have an exfiltration channel.
PDF Versions Affected
It is important to note that for both attacks, the attacker gets full control of the appearance of the displayed document.

According to researchers, 21 out of 22 desktop PDF viewer applications and 5 out of 7 online PDF validation services are vulnerable against at least one of our attacks.
“We reported our attacks to the affected vendors and have proposed appropriate mitigations. However, to sustainably eliminate the root cause of the vulnerabilities, changes in the PDF standard are required,” the paper reads.
The vulnerabilities can be tracked as CVE-2018-16042, CVE-2018-18688 and CVE-2018-18689 .
Full technical details on PDFex found on the research paper and also researchers published a dedicated website with more details.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates



.png
)
