The Predator Files project, coordinated by the European Investigative Collaborations (EIC), has highlighted the extensive use of Predator spyware by customers of Intellexa surveillance solutions.
The intrusion set, known as Lycantrox, was exposed by Sekoia.io in collaboration with Amnesty International, CitizenLab, and MediaPart.
The exposure led to the shutdown of the spyware’s infrastructure, which was used against civil society, journalists, politicians, and academics.
However, despite the initial disruption, Sekoia.io discovered new infrastructure indicating that Predator spyware is still actively used.
You can analyze a malware file, network, module, and registry activity with the ANY.RUN malware sandbox and the Threat Intelligence Lookup that will let you interact with the OS directly from the browser.
Evolving Tactics for Stealth Operations
The new infrastructure revealed a shift towards more generic malicious domains, suggesting that government services using Intellexa’s solutions adapt their operations for greater plausible deniability.
Angola’s Concealed Continuation
Previously identified domains linked to Angola suggested government use of Predator.
The latest findings show Portuguese-speaking malicious domains not directly tied to Angola, hinting at continued use with improved operational security.
Madagascar’s Subtle Shift
Madagascar, which had acknowledged the use of Predator, now shows fewer noticeable malicious domains.
A domain resembling the French newspaper Le Monde was linked to Madagascar with medium confidence.
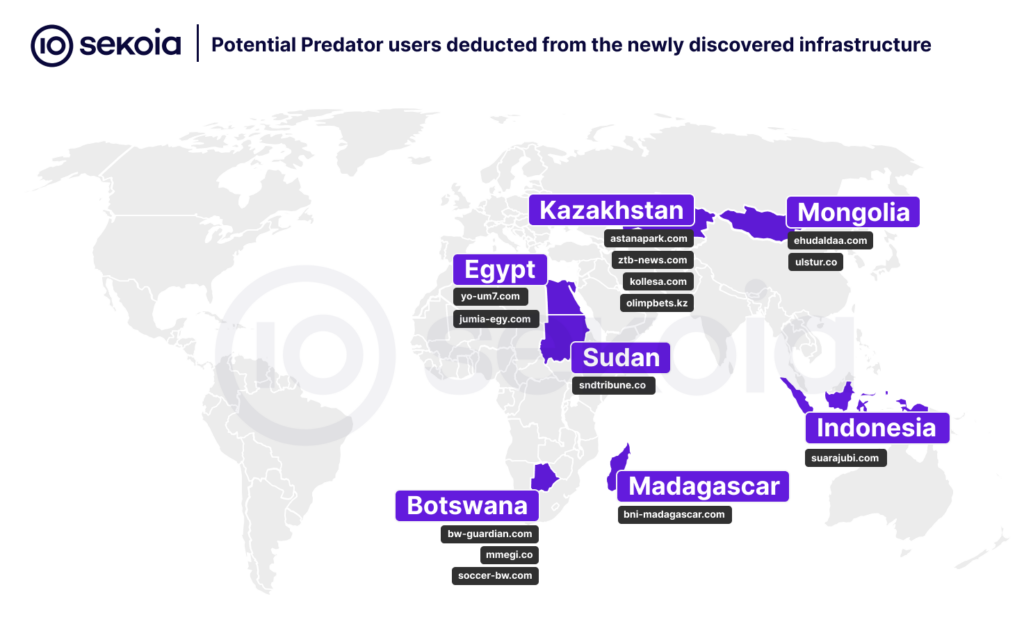
Indonesia and Kazakhstan: Business as Usual
Indonesia’s new domains confirm ongoing political surveillance, while Kazakhstan continues its use of Predator without significant operational changes.
Egypt’s Unchanged Stance
Egypt-related domains continue to mimic various sectors, with no notable change in operational security.
Sekoia.io has identified domains related to Botswana, Mongolia, and Sudan, expanding the list of potential Predator users.
Ongoing Vigilance and Collaboration
Sekoia TDR analysts remain committed to monitoring cyber mercenary groups and supporting initiatives like the Pall Mall Process to combat the irresponsible use of commercial cyber intrusion capabilities.
In conclusion, despite setbacks, the Predator spyware ecosystem remains a persistent threat.
The efforts of Sekoia.io and its partners underscore the importance of continued vigilance and international cooperation to address the challenges posed by commercial surveillance technologies.
You can block malware, including Trojans, ransomware, spyware, rootkits, worms, and zero-day exploits, with Perimeter81 malware protection. All are incredibly harmful, can wreak havoc, and damage your network.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.



.png
)
