A vulnerability in Qualcomm’s Secure Execution Environment(QSEE) implementation of the Trusted Execution Environment(TEE) used in a number of devices especially in Android devices lets attackers to steal sensitive data from the isolated secure area of the processor.
Qualcomm implementation used in number of devices such as Pixel, LG, Xiaomi, Sony, HTC, OnePlus, Samsung.
The trusted apps running in TEE is an isolated environment and the security extension backed by an ARM processor is an integral part of every modern mobile device.
What TEE Implementation Consists
The TEE implementation consists of the following trusted operating system, drivers, Normal and Secure world’s libs, trusted apps and other components.
It is the main core area of the processor which guarantees that code and data executed within TEE are protected. Security research in these areas are difficult as it has proprietary code
A vulnerability in TEE may leads to leakage of protected data, device rooting, bootloader unlocking, execution of undetectable APT, and more.
Checkpoint researchers conducted fuzzing-based research in TEE implementations, the fuzzing test is the method to find implementation bugs by providing invalid or random data through automated methods.
“Researchers noted that all data related to a trustlet is concentrated in one place. It is its data segment region.”
Trusted Apps loaded in Normal World
After four months of research, they found a hole to execute the trusted app in the Normal world by detecting the detect the start addresses of the trustlet’s code and data segments in the Secure world and dump them.
The following problems arise when loading the command handler function that calls for cmnlib and syscall during the execution.
- Detect base addresses of a trustlet and cmnlib in the Secure world.
- Dump data segments of a trustlet and cmnlib.
- Execute a trustlet’s syscall in the Normal world.
“All of these problems can be resolved if we can patch a chosen trustlet before loading it into the Secure world. In this case, we can extend its command handler function for one more supported command ID.”
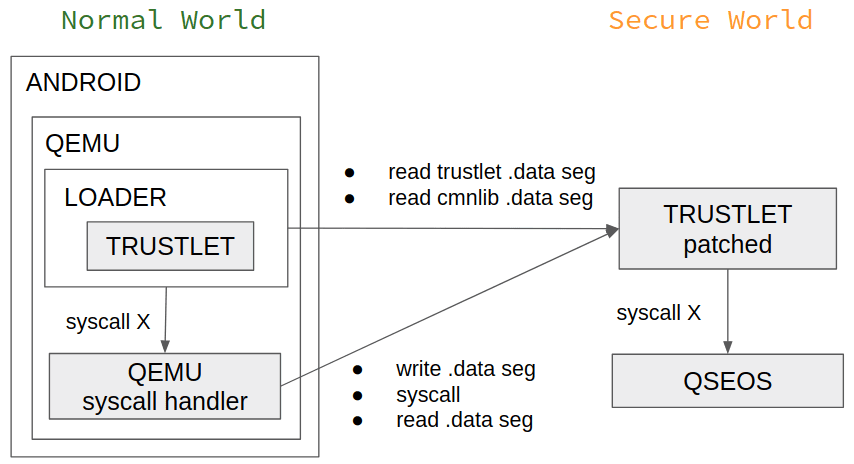
This provides an ability to request the base address and data segment memory block of the trustlet from the Normal world.
Trusted app in the Secure World
The primary target of the attack is the trustlet verification algorithm. “We want to “nop” the QSEOS code responsible for calculating the hash block’s signature or for comparing the actual hashes of the segments with the verified ones.”
The next step is loading the trusted app in the Secure world without breaking the chain of trust.
In the process, they used two exploits CVE-2015-6639 and CVE-2016-2431 that give them “a possible way to patch the QSEOS data segment on a Nexus 6 device with an Android of up to MOB30D build.”
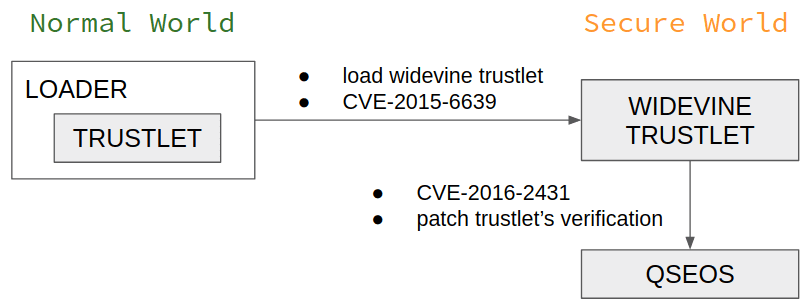
By executing the command researchers gained the ability ” to replace a trustlet’s hash block after verification but before using it to validate the segments.”
The research said that the trustlet will successfully pass the verification. An interesting fact is that we can load trustlets from another device as well.”
According to researchers, vulnerability lets an attacker run the trusted app in the normal world, patched trusted app in the secure world, breaking Qualcomm’s Trust chain and more.
The vulnerability affects several Android and IoT devices, Checkpoint reported the vulnerability to Qualcomm in June and it has been patched.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates.
Also Read
QualPwn – Vulnerabilities in Qualcomm chips Allows Attackers to Compromise Android Devices Remotely



.png
)
