Cybersecurity researchers at Bitdefender have uncovered a significant evolution in the tactics of the RedCurl threat group, marking their first foray into ransomware deployment.
This new strain, dubbed QWCrypt, specifically targets Hyper-V servers, showcasing a sophisticated and highly targeted approach to cyberattacks.
Novel Ransomware Strain Emerges
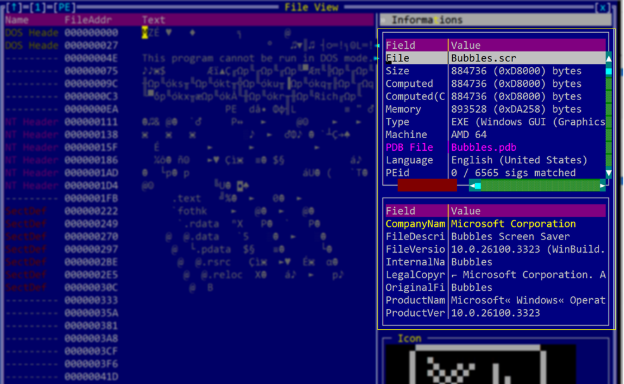
The QWCrypt ransomware, previously undocumented, represents a departure from RedCurl’s historical focus on corporate espionage and data exfiltration.
This UPX-packed Go executable employs a unique strategy, encrypting virtual machines hosted on hypervisors while deliberately excluding specific VMs that act as network gateways.
The ransomware’s configuration includes a hardcoded personal ID, likely corresponding to a unique RSA key pair, with the public key embedded within the malware.
According to the Report, this setup implies that the attackers maintain a matching private key for decryption purposes.
Sophisticated Deployment and Evasion Techniques
RedCurl’s attack vector remains consistent with their previous campaigns, utilizing social engineering and spear-phishing emails containing IMG files disguised as CV documents.
The group leverages DLL sideloading vulnerabilities in legitimate Adobe executables to initiate the infection chain.

The ransomware deployment process involves a series of batch scripts tailored to the victim’s environment.
These scripts disable Windows Defender and other security solutions, demonstrating the attackers’ deep understanding of the target infrastructure.
The malware also employs Living Off The Land (LOTL) techniques, abusing legitimate system tools like pcalua.exe and rundll32.exe to evade detection.
This shift in RedCurl’s tactics raises critical questions about their motivations and operational objectives.
The highly targeted nature of the ransomware attack, focusing exclusively on Hyper-V servers while maintaining network gateway functionality, suggests a deliberate effort to confine the attack’s impact to IT departments.
Bitdefender recommends implementing a multilayered security approach, including network segmentation and enhanced endpoint protection.
Organizations should prioritize detection and response capabilities, focusing on behavioral analysis and anomaly detection to identify suspicious activities.
Additionally, implementing strict application control and hardening scripting environments can help mitigate Living-off-the-Land attacks.
As the threat landscape continues to evolve, this new ransomware strain serves as a stark reminder of the need for constant vigilance and adaptive cybersecurity strategies in the face of increasingly sophisticated threat actors.
Are you from SOC/DFIR Teams? – Analyse Malware, Phishing Incidents & get live Access with ANY.RUN -> Start Now for Free.
.webp?w=696&resize=696,0&ssl=1)


.png
)
