The cyber threat landscape has witnessed remarkable adaptation from the notorious hacker collective known as Scattered Spider.
Active since at least 2022, this group has been consistently refining its strategies for system compromise, data exfiltration, and identity theft.
Silent Push analysts have tracked the evolution of Scattered Spider’s tactics, techniques, and procedures (TTPs) through early 2025, uncovering significant shifts in the group’s infrastructure and deployment strategies.
In early 2025, Scattered Spider unveiled an updated version of the notorious Remote Access Trojan (RAT) known as Spectre RAT.
This malware allows for stealthy, persistent access to compromised systems, enabling threat actors to carry out data exfiltration and execute commands remotely.
A notable change was the incorporation of dynamic DNS/rented subdomains in their phishing kits, which further complicates efforts by security teams to track and shut down their operations.
Innovative Phishing and Infrastructure
Scattered Spider’s phishing campaigns have become increasingly nuanced.
The group’s domain name strategies now often emulate legitimate organizations or include specific keywords to appear more credible.
The latest phishing kit, entitled Phishing Kit #5, observed in 2025, was hosted on Cloudflare and featured a reimagined deployment process that relies less on fully registered, centralized domains and more on publicly rentable subdomains.

In recent campaigns, Scattered Spider has shown a preference for registrars like NiceNIC and hosting services like Njalla, Virtuo, and Cloudflare.
These providers offer features that facilitate anonymity and dynamic updates, aligning with the group’s need for agility in their attack infrastructure.
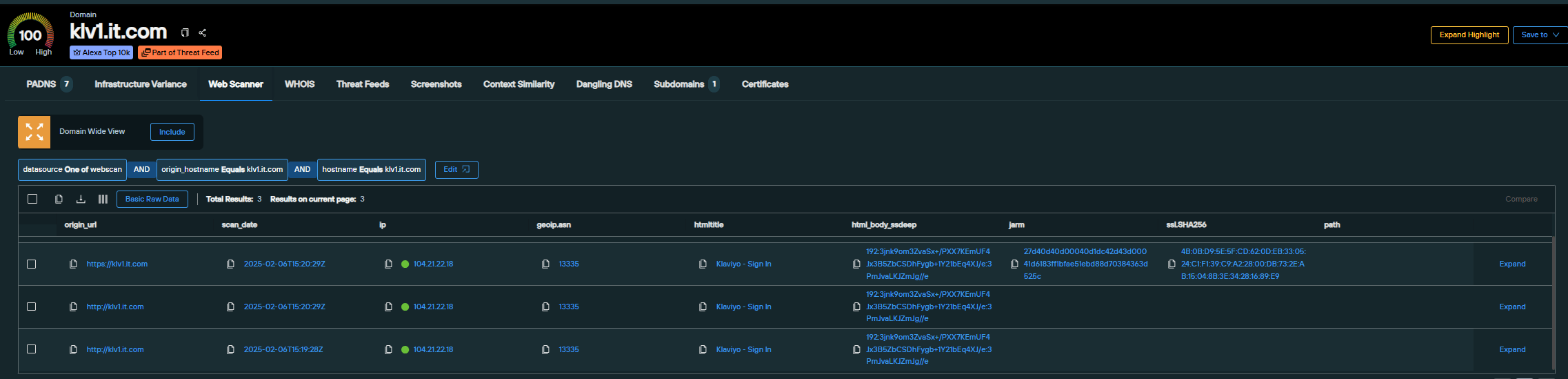
An example includes the targeted domain klv1.it[.]com, which impersonated a “Custom Link Shortener” used by Klaviyo, one of their previous targets.
Targeting and Reach
Scattered Spider’s selection of targets remains broad, with a particular focus on financial services, retail, telecommunications, and cloud storage platforms.
High-profile breaches attributed to Scattered Spider include attacks on Twilio in 2022, MGM Resorts in 2023, and most recently, Pure Storage in 2025.
Their approach involves careful research of potential targets, often impersonating brands that align with the victim’s sector or software vendors they use.
Law enforcement efforts in 2024 led to the arrests of at least seven Scattered Spider members, including an alleged leader.

Subsequent charges by U.S. prosecutors in November 2024 temporarily slowed operations.
However, 2025 has seen the group adapt its tactics and infrastructure, indicating they are far from eradicated.
Silent Push recommends vigilant monitoring of Scattered Spider-associated domains, suggesting organizations implement blocking measures for connections to subdomains from services that allow public registration.
This step is essential to minimize potential risks and limit the group’s attack vectors.
The ongoing threats posed by Scattered Spider have economic and geopolitical implications.
The group’s ability to steal login credentials, MFA tokens, and sensitive data can lead to substantial financial losses for the affected organizations, and potentially compromise critical infrastructure.
Their continued activity, regardless of legal actions, underscores the enduring challenge presented by advanced persistent threats (APTs) in today’s digital landscape.
Silent Push has developed tools and resources to aid organizations in defending against these evolving threats.
The company’s Indicators of Future AttackTM (IOFATM) Feeds provide insights into Scattered Spider’s infrastructure, while a Bulk Data Feed tracks dynamic DNS providers and publicly rentable subdomains, helping organizations proactively mitigate risks.
As Scattered Spider evolves, cybersecurity professionals must remain agile and proactive in their defense strategies.
Silent Push continues to offer advanced threat intelligence through webinars, reports, and data feeds, empowering defenders to stay ahead in the cat-and-mouse game against these sophisticated adversaries.
As the cyber threat landscape evolves with Scattered Spider’s sophistication, keeping up with their changing tactics is paramount.
Silent Push remains at the forefront, equipping organizations with the necessary tools and knowledge to counter these persistent threats.
The comprehensive analysis of Scattered Spider’s tactics and the recommendations provided by Silent Push not only shed light on the intricacies of this threat actor but also offer actionable insights to secure systems against such targeted cyber-attacks.
The evolving nature of this threat requires continuous monitoring, proactive defense strategies, and a collaborative effort between Silent Push, cybersecurity professionals, and the broader community to stay ahead in this rapidly changing cybersecurity landscape.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
