A critical vulnerability has been discovered in AMI’s MegaRAC software, which is used in Baseboard Management Controllers (BMCs) across various server hardware.
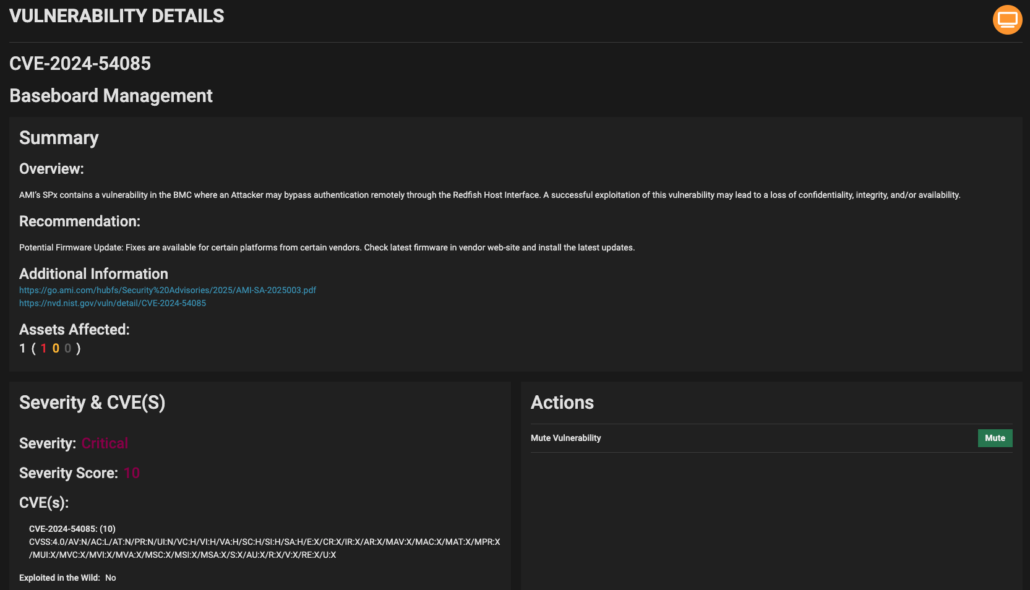
This vulnerability, identified as CVE-2024-54085, allows attackers to bypass authentication remotely, posing a significant risk to cloud infrastructure and data centers worldwide.
The issue is a continuation of previous vulnerabilities disclosed by Eclypsium, highlighting the ongoing challenges in securing BMCs, which are crucial for remote server management.
Background
The vulnerability exploits a weakness in the Redfish interface of MegaRAC, allowing unauthorized access to BMCs.
This can lead to severe consequences, including remote control of compromised servers, deployment of malware or ransomware, firmware tampering, and even physical damage to server components.
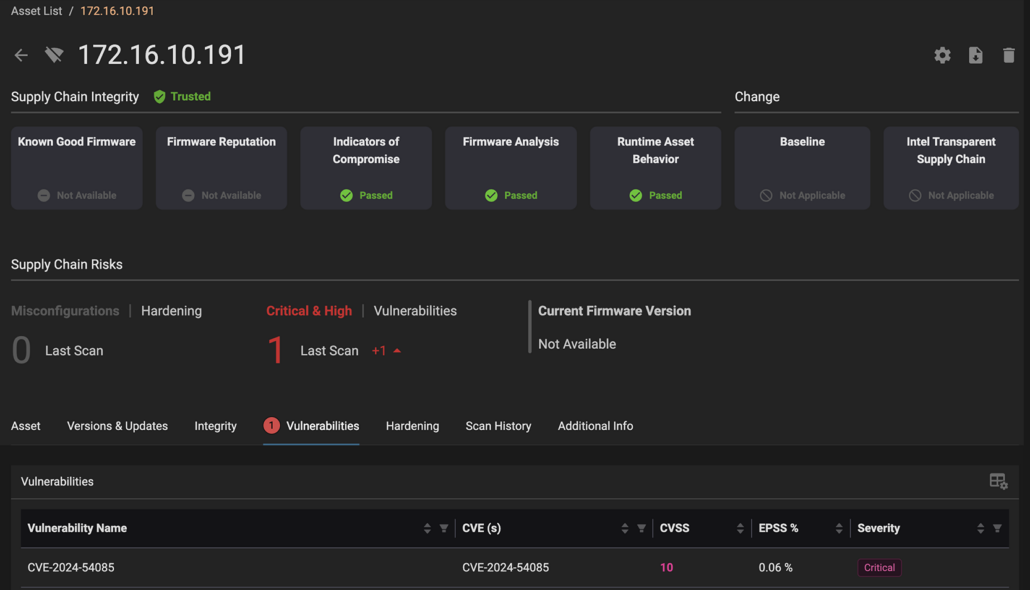
The vulnerability affects several devices, including the HPE Cray XD670 and Asus RS720A-E11-RS24U, with potentially more devices impacted due to the widespread use of AMI’s BMC software across multiple manufacturers.
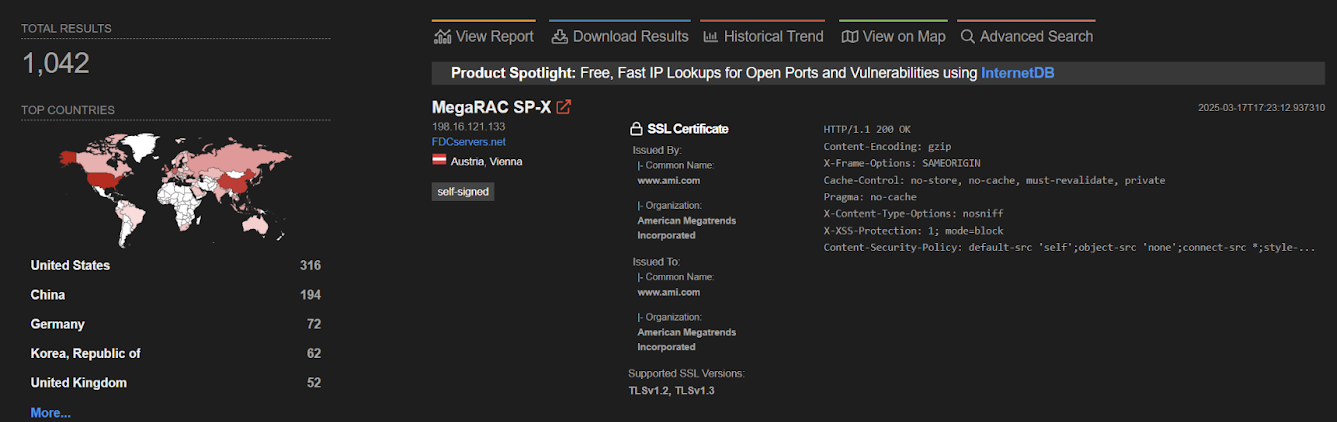
A search using Shodan revealed approximately 1,000 exposed instances, indicating a substantial risk if these systems are not patched promptly.
Impact
The exploitation mechanism involves crafting specific HTTP headers to bypass authentication checks.
By manipulating the “X-Server-Addr” header, attackers can trick the system into accepting unauthorized access.
This vulnerability is particularly concerning because it can be exploited without any user interaction, and the CVSS scores reflect its high severity, with a score of 10.0 for systems exposed to the internet.
AMI has released patches for the vulnerability, but applying these fixes requires device downtime, making remediation a complex process.
Organizations are advised to ensure that all remote management interfaces are not exposed externally and to restrict internal access to authorized personnel.
Regular software and firmware updates are crucial, along with monitoring server firmware for signs of compromise.
Additionally, new equipment should be thoroughly checked for outdated firmware and potential supply chain risks.
Eclypsium’s research emphasizes the importance of robust security measures for BMCs, given their critical role in data center operations.
As no known exploits are currently observed in the wild, organizations have a window to secure their systems before potential attacks occur.
However, the ease of creating exploits once the vulnerability is understood underscores the urgency of implementing patches and security best practices.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.



.png
)
