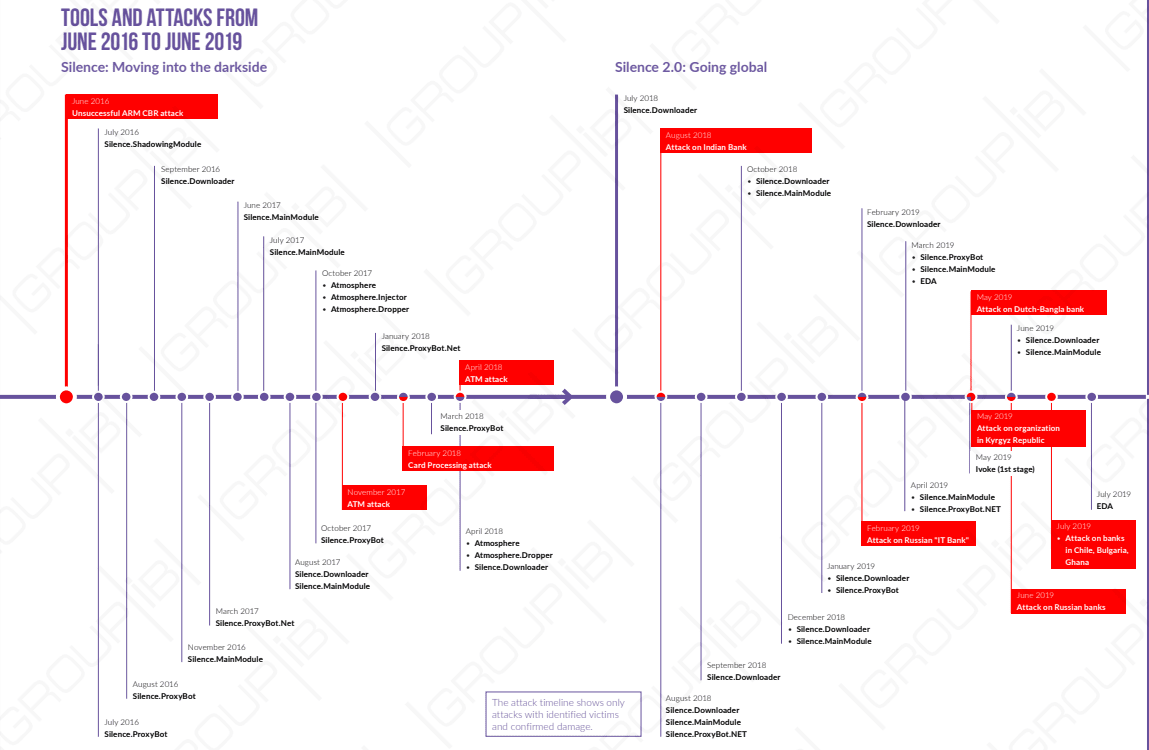
The silence hacker group is one of the most active threat actors group that targets financial sectors. The group initially attacks banks in Russia and now the group expanded its geography.
According to the report shared by Group-IB with GBHackers on Security, the hacker group has infected more than 30 countries across America, Europe, Africa, and Asia.
The group also made a number of changes to their toolset to stay undetected by security tools and they have also made changes to their encryption alphabets, string encryption, and commands for the bot and the main module.
It was believed that the group has stolen more than 4.2 million US dollars between June 2016 to June 2019. the group actively targets financial sectors.
Silence Group Campaigns
Silence group also uses phishing as an attack vector, the email sent by the silence group includes a picture or a link without a malicious payload and the email has been sent to over 85,000 users.
Starting from October 2018, the group started sending reconnaissance emails to get an updated list of the active email address and to obtain cybersecurity tools used in the companies.
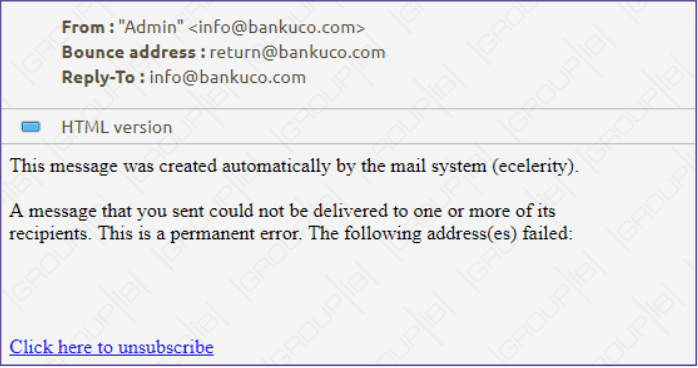
Silence has conducted at least three campaigns using recon emails, the campaigns were no longer focused just on Russia and former Soviet countries, but spread across Asia and Europe. The Hacker group has sent more than 170,000 recon emails.

Tools and Tactics
The group uses almost the same tactics, they still use Microsoft Office documents with macros or exploits, CHM files, and.LNK shortcuts as malicious attachments.
“Threat actors have completely rewritten TrueBot loader, the first-stage module, on which the success of the group’s entire attack depends. The hackers also started using Invoke, a fileless loader, and EDA agent, both written in PowerShell.”
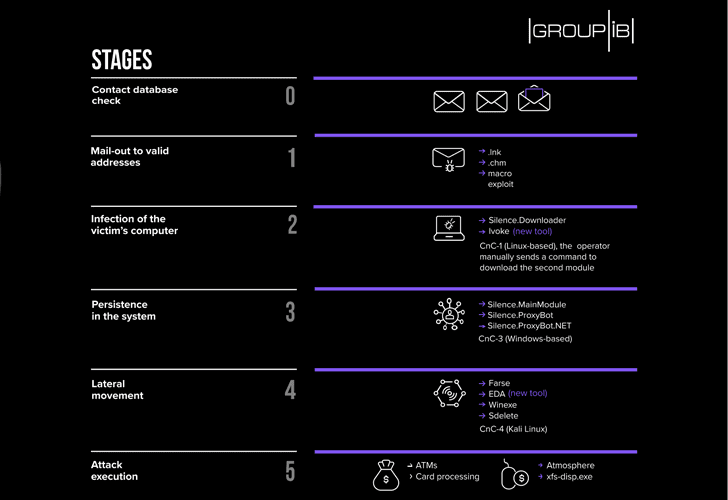
The attack success depends on the initial infection, the primary loader is Silence.Downloader (aka TrueBot), Group-IB also observed the threat actors fileless PowerShell loader called Ivoke.
Silence.Main is the primary payload that contains a full set of C&C commands that required to control the compromised computer and to download additional modules.
With the recent attacks, Silence group downloads a PowerShell agent based on the opensource projects Empire and dnscat2, along with that the group also downloads other proxy services to hide the C&C communication.
The final stage of the attack is to gain control over ATMs, the group uses Atmosphere Trojan which was designed by them or another program called xfs-disp.exe to dispense cash from ATMs.
Group-IB analysis revealed that FlawedAmmyy.Downloader and Silence.Downloader is developed by the same person and the developer is a Russian speaker and works actively on underground platforms. Researchers also believed the developer linked to attacks by TA505.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity updates.



.png
)
