In an age where digital footprints can be traced with just a few clicks, surveillance technology has become a double-edged sword. While it can enhance security and improve services, it also poses significant privacy concerns.
One of the most formidable players in this realm is Russia, whose surveillance technologies are expanding their reach across borders, tracking individuals, and curtailing freedoms in several nations worldwide.
The Backbone of Russian Surveillance: SORM
At the heart of Russia’s surveillance capabilities is the System for Operative Investigative Activities (SORM), which underpins the nation’s electronic monitoring apparatus.
Established in the 1990s, SORM mandates telecommunications providers to install monitoring equipment that allows Russian authorities direct access to all telecommunications traffic without the knowledge of the service providers.
The SORM system has evolved through three iterations—SORM-1, SORM-2, and SORM-3—each expanding the scope of surveillance, including real-time monitoring of internet activity, social media, and even geolocation tracking.
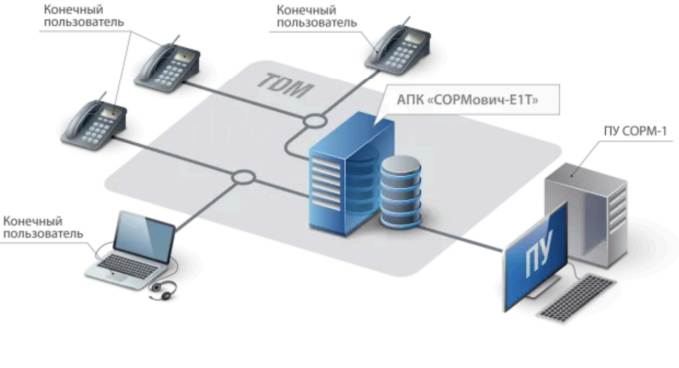
The implications of this system are profound. SORM not only facilitates the interception of vast amounts of personal data but does so with minimal oversight, raising significant concerns over abuse of power.
This apparatus has become a model for authoritarian regimes, providing a legal framework for widespread digital surveillance.
Global Spread of Surveillance Technology
Recent reports from Recorded Future indicate that Russian surveillance technologies have proliferated beyond its borders, particularly in Central Asia and Latin America.
Countries such as Belarus, Kazakhstan, Kyrgyzstan, Cuba, and Nicaragua have adopted SORM-based systems, significantly enhancing their capacity for state surveillance.
These nations have histories of using surveillance systems to suppress dissent and monitor political opposition, prompting concerns over human rights abuses.
Russian companies like Citadel, Norsi-Trans, and Protei have actively marketed their SORM solutions to these countries, participating in regional trade expos and offering customized services designed to meet local regulatory requirements.
Insight from the Insikt Group highlights that the exportation of SORM technology is often facilitated by intermediaries linked to Russian intelligence, increasing the risks associated with data privacy on a global scale.

Surveillance in Action: Case Studies
Belarus
Belarus stands as a stark example of how Russian surveillance technologies can be used to consolidate power. Following the installation of SORM-compliant hardware in 2010, the Belarusian government has engaged in extensive monitoring of both citizens and foreign nationals.
Reports suggest that there is no legal requirement for authorities to obtain judicial approval before intercepting communications, significantly increasing the likelihood of abuse against political dissidents and activists.
Kazakhstan
Kazakhstan has similarly embraced the SORM framework, with regulations implemented by the National Security Committee allowing for real-time network access to monitor communications.
Reports of unauthorized surveillance are not uncommon, leading to a chilling effect on free speech. Before its withdrawal from the country, Swedish telecommunications company Tele2 cited concerns over the opacity of SORM usage in its operations.
Cuba and Nicaragua
In Cuba, the government has implemented laws requiring telecommunications providers to store user data and allow direct access by state security. The influence of Russian technologies is evident in the government’s capacity to monitor communications.
Nicaragua, too, has legal structures that facilitate government surveillance, often without the checks and balances that a democratic society might demand.
The Risk of Russian Access to Global Data
One of the most alarming aspects of SORM technology deployment abroad is the potential for Russian intelligence to access vast stores of intercepted data.
The interconnected nature of global telecommunications means that systems equipped with Russian SORM components may inadvertently grant the Kremlin access to sensitive information.
Concerns have been raised about the dual-use nature of these technologies, which can serve both legitimate security purposes and state-sponsored espionage.
For individuals and corporations operating in regions with SORM technology, mitigating privacy risks is crucial.
Experts recommend using encrypted communication methods, such as secure messaging apps and virtual private networks (VPNs), to safeguard sensitive information.
Conducting thorough assessments of the surveillance landscape in host countries can also help organizations navigate the complexities and risks associated with foreign operations.
The Russian model of SORM serves as a troubling template for other regimes, indicating a trend toward increased state control over personal data.
With governments seeking to expand their security apparatuses, the global community must remain vigilant in advocating for privacy rights and the responsible use of technology.
The rise of Russian surveillance systems like SORM exemplifies a significant and growing threat to privacy worldwide.
Addressing these challenges requires a coordinated effort to uphold the principles of transparency, accountability, and respect for human rights in the face of an evolving digital landscape.
ANY.RUN Threat Intelligence Lookup - Extract Millions of IOC's for Interactive Malware Analysis: Try for Free



.png
)
