Simjacker vulnerability disclosed last month, being exploited by attackers for more than two years. The vulnerability is based on SIM card technology.
The vulnerability relies on the S@T Browser technology, which has no authentication enabled by default, it let attackers execute any command on SIM card without user consent.
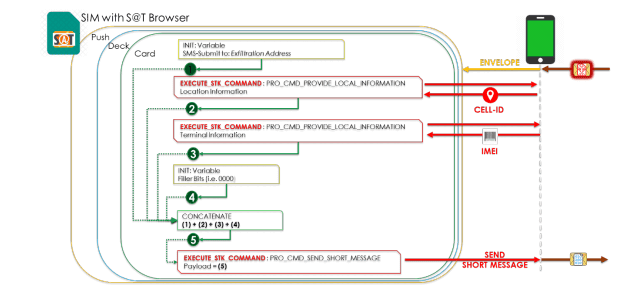
All the attacker require is to send a message which includes spyware-like code to the targeted mobile phone, the message instructs the SIM cards to send to another message with details such as location/terminal information, without any user interaction.
For a successful attack, the following conditions to be satisfied
- Successful SMS Delivery
- SIM should use S@T Browser technology
The vulnerability was disclosed by Adaptive Mobile Security, according to the new report published by the company, 61 Mobile Operators in the 29 countries use S@T Browser technology. 861 Million active SIM cards use this technology.
Attack Volume
Researchers observed over 25k Simjacker messages are attempted to send for more than 1500 Unique Identifiers. Most of the targeted users are from Mexico and few users from Colombia and Peru.
In a given single day 69% of users are targeted and few users are targeted every single day. The primary objective of the attack is to get the geo-location and IMEI of the device.
Following are the additional commands executed
- Display Text (Test Messages),
- Launch Browser (Test websites),
- Set Up Call (test recipient number) and
- Send USSD (test PIN change)
“Researchers observed that over 860 Simjacker Attack sub-variants in the actual SMS Packet and they are sent in 1000 different types of encoding combinations, the actual Simjacker Attack packet itself was done to also potentially avoid defenses, or potentially to tailor the attack per specific Sim card type.”
Countries Affected
At least 29 countries still S@T Browser with the no-security level set. According to an analysis report, 61 Mobile Operators using this technology, around 90% of the SIM card issued by the operators use this technology.

- Asia: Saudi Arabia, Iraq, Palestine and Lebanon.
- Africa: Nigeria, Ghana, Benin, Ivory Coast, and Cameroon.
- North America: Mexico, Guatemala, Honduras, Costa Rica, Nicaragua, Belize, El Salvador, Dominican Republic, and Panama.
- Europe: Italy, Bulgaria, and Cyprus.
- South America: Peru, Colombia, Brazil, Ecuador, Chile, Argentina, Uruguay, and Paraguay.
Countries /operators are using the technology which we did not observe directly. This is because our search was based on a side effect of looking for attacks on users, not looking for ordinary activity, researchers said.
Researchers believe operators in other countries may also use this technology, but as we did not directly observe S@T Browser messaging at a no security Level.
The attack can be used in any of the following scenarios
- Fraud Applications
- Advanced Location Tracking
- Assistance in Malware Deployment
- Denial of Service
- Information Retrieval
- Misinformation
Similar to the Simjacker attack, another vulnerability was observed at the end of September dubbed WIBattack which impacts millions of od subscribers around the globe.

Adaptive security researchers also looked at WIB application, when used with no security level is used in far fewer countries: 7 and operators:8. These countries are spread over Eastern Europe, Central America, Asia, and West Africa.
You can follow us on Linkedin, Twitter, Facebook for daily Cybersecurity and hacking news updates



.png
)
