A critical zero-day vulnerability in Sitecore’s enterprise content management system (CMS) has been uncovered, enabling unauthenticated attackers to execute arbitrary code on affected servers.
Designated CVE-2025-27218, this pre-authentication remote code execution (RCE) flaw resides in Sitecore versions up to 10.4 and stems from unsafe deserialization practices involving the .NET BinaryFormatter class.
The vulnerability exposes organizations using the platform to full server compromise, data theft, and lateral movement within networks.
Technical Analysis of the Deserialization Vulnerability
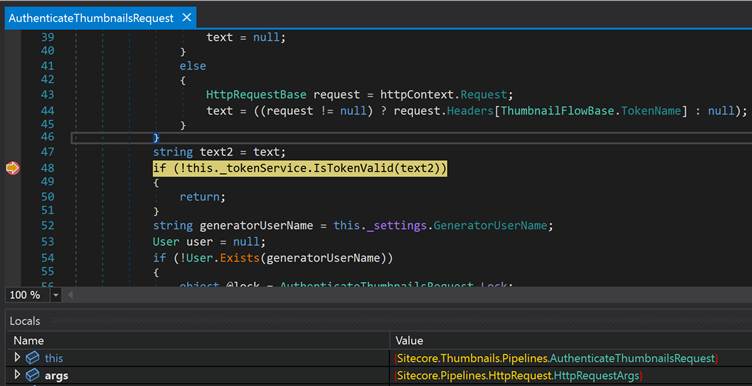
The vulnerability originates in Sitecore’s MachineKeyTokenService.IsTokenValid method, which processes user-supplied tokens through the Convert.Base64ToObject wrapper.
This custom function deserializes Base64-encoded data using BinaryFormatter—a known risky component due to its ability to instantiate arbitrary .NET objects during deserialization.
Crucially, the decryption step via MachineKey.Unprotect occurs after deserialization, bypassing any cryptographic validation of the payload’s integrity before processing.
public bool IsTokenValid(string token) {
try {
byte[] protectedData = Convert.Base64ToObject(token) as byte[];
byte[] array = MachineKey.Unprotect(protectedData);
// Validation occurs after deserialization
Guid guid = new Guid(array);
return guid == _token;
} catch { return false; }
}
Attackers can exploit this by crafting malicious serialized payloads using tools like ysoserial.net, embedding commands that execute with WindowsIdentity privileges.
The payload is delivered through the ThumbnailsAccessToken HTTP header, which the AuthenticateThumbnailsRequest processor passes directly to the vulnerable method.
Exploitation Methodology and Impact
Successful exploitation requires no authentication and leaves minimal forensic traces beyond error logs.
As per a report by Searchlight Cyber, Researchers demonstrated the flaw by injecting a payload that writes a file to the web root:
ysoserial.exe -f BinaryFormatter -g WindowsIdentity -c "whoami > \inetpub\wwwroot\...\x.txt"This grants attackers the same privileges as the Sitecore application pool identity, typically high-permission service accounts with access to databases, file systems, and network resources.
Enterprise environments using Sitecore for customer portals, e-commerce platforms, or internal systems face severe operational and reputational risks.
Mitigation and Patch Deployment
Sitecore has released security updates addressing CVE-2025-27218 in version 10.4.1. Organizations should:
- Immediately apply patches from Sitecore’s advisory portal
- Remove or disable the AuthenticateThumbnailsRequest HTTP processor if immediate patching isn’t feasible
- Audit logs for unexpected ThumbnailsAccessToken header values or 500 errors from /thumbnails endpoints
Security teams should implement runtime protection mechanisms like WAF rules blocking requests containing TypeConfuseDelegate or WindowsIdentity in Base64-encoded headers.
CVE-2025-27218 represents a critical threat to Sitecore deployments worldwide, with exploit development likely already underway.
While patches are available, the window for remediation is closing rapidly. Organizations must prioritize inventorying affected systems, applying updates, and monitoring for anomalous authentication patterns.
This incident reinforces the necessity of continuous attack surface management and proactive security testing for enterprise CMS platforms.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free



.png
)
