In a recent investigation into Amazon Web Services (AWS) security breaches, Mandiant uncovered a troubling scenario: client-specific secrets were leaked from Atlassian’s code repository tool, Bitbucket, and exploited by threat actors to gain unauthorized access to AWS accounts.
This revelation highlights the potential vulnerabilities in Bitbucket’s Secured Variables.
These variables can be leaked in CI/CD pipelines, exposing organizations to significant security risks.
ANYRUN malware sandbox’s 8th Birthday Special Offer: Grab 6 Months of Free Service
Bitbucket and CI/CD Secrets
Bitbucket, an Atlassian code hosting platform, includes a built-in continuous integration and delivery/deployment (CI/CD) service known as Bitbucket Pipelines.
This service is commonly used to deploy and maintain AWS resources.
According to Google Cloud Blog, Bitbucket’s administrative function, “Secured Variables,” allows administrators to store CI/CD secrets, such as AWS keys, directly in Bitbucket for easy reference by code libraries.
CI/CD secrets are crucial for authentication and authorization within CI/CD pipelines, providing the credentials for pipelines to interact with platforms like AWS.
These secrets are precious to attackers as they offer direct access to an environment.
Balancing the confidentiality of these secrets with ease of use for developers is a constant challenge in securing CI/CD pipelines.
Exporting Secrets from Bitbucket
CI/CD pipelines, like household plumbing, are complex orchestrations of events designed to accomplish specific tasks.
While they offer developers numerous possibilities for automating work, they can also be a source of anxiety for security professionals.
A single line of code with a hardcoded secret or a developer accidentally storing secrets locally can lead to significant security breaches.
Although Bitbucket’s secured variables are convenient for storing secrets locally, they have a concerning characteristic—they can be exposed in plain text through artifact objects.
If a Bitbucket variable, secured or not, is copied to an artifact object using the artifacts: command, the result is a .txt file with the variable’s value displayed in plain text.
Reproducing the Secret Leak
To recreate the secret leak in a Bitbucket environment, follow these steps:
- Establish Secured Variables in Bitbucket: Set secured variables at the repository or workspace level.

- Update the bitbucket-pipelines.yml File: Execute the printenv command to copy all environment variables to a .txt file called environment_variables.txt. This file is then passed to a Bitbucket artifact object for use in future pipeline stages.
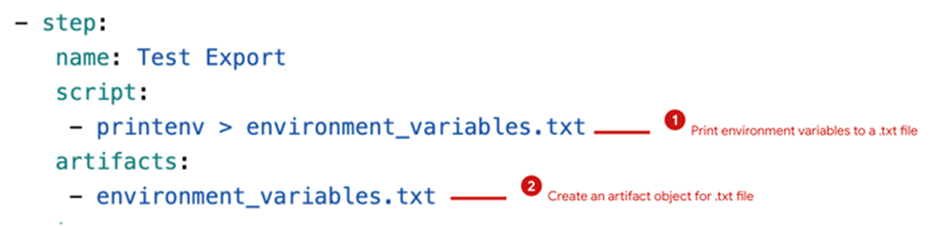
- Navigate to the Pipeline Execution History and Download the Artifact: Access the pipeline execution history and download the artifact.

- Open the Artifact and Search for Secured Variables: After exporting the .txt file, secrets can be read in plain text among all the variables in the Bitbucket environment.
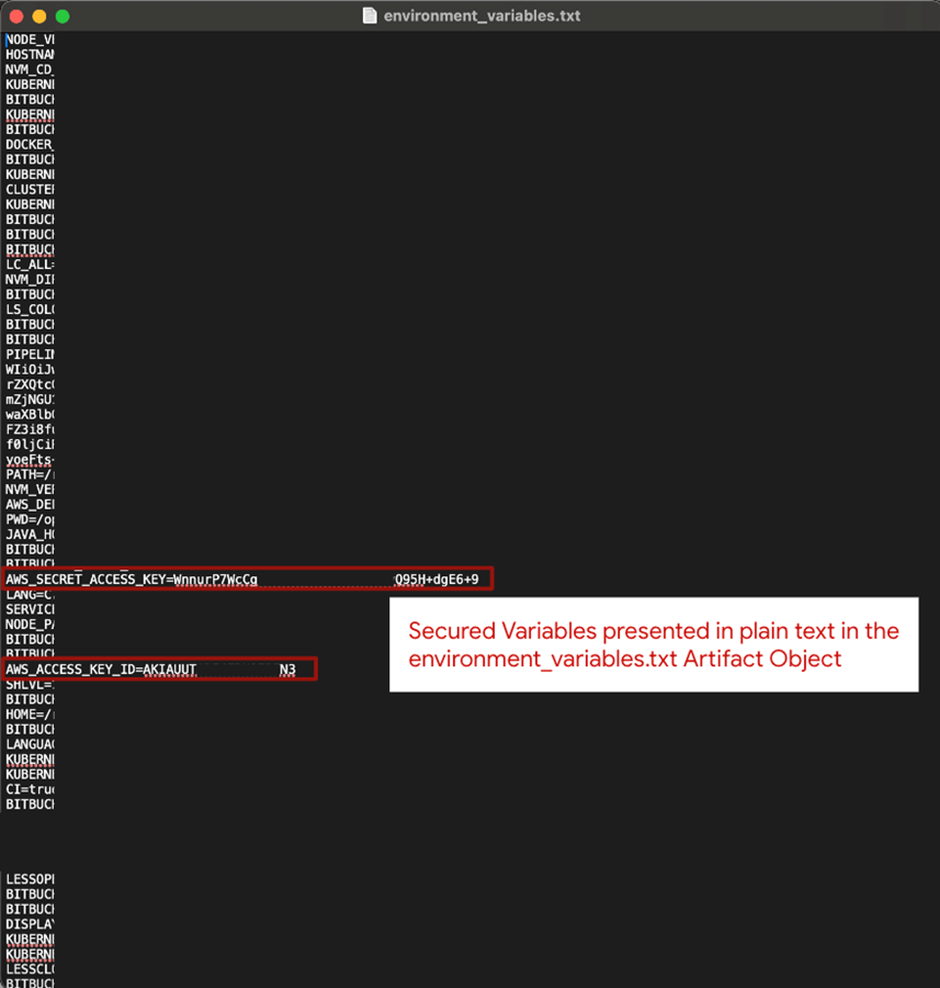
Once secrets are printed to the environment_variables.txt file, they can flow out of Bitbucket through the pipeline and become exposed.
This exposure can result from development mistakes, malicious intent, or accidental disclosure, leading to misuse by threat actors.
To protect your secrets when using Bitbucket Pipelines:
- Store secrets in a dedicated secrets manager and reference those variables in your Bitbucket repository code.
- Closely review Bitbucket artifact objects to ensure they do not expose secrets as plain text files.
- Deploy code scanning throughout the pipeline lifecycle to catch secrets stored in code before deployment to production.
This case study is not an indictment against Bitbucket but a reminder of how seemingly innocuous actions can lead to serious security issues.
A single keystroke, line of code, or misconfiguration can cause a slow, untraceable leak of secrets through your pipeline, exposing them to the world.
Organizations must remain vigilant and implement robust security measures to safeguard their CI/CD environments.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
.webp?w=696&resize=696,0&ssl=1)


.png
)
