The rapid evolution of Phishing-as-a-Service (PhaaS) platforms is reshaping the threat landscape, enabling attackers to launch increasingly sophisticated phishing campaigns.
One such advanced PhaaS platform, Tycoon, has seen widespread use since its emergence in August 2023.
In November 2024, it debuted its latest iteration, Tycoon 2FA, which bypasses multifactor authentication (2FA) using Microsoft 365 session cookies.
30% of credential attacks in 2024 leveraged PhaaS platforms like Tycoon, a figure projected to rise to 50% by 2025.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Advanced Evasion Tactics in the Latest Tycoon 2FA
The new Tycoon 2FA campaigns exhibit a significant shift in tactics.
Attackers now exploit compromised but legitimate email accounts to send phishing emails, which leads unsuspecting users to fake Microsoft login pages designed to steal credentials.
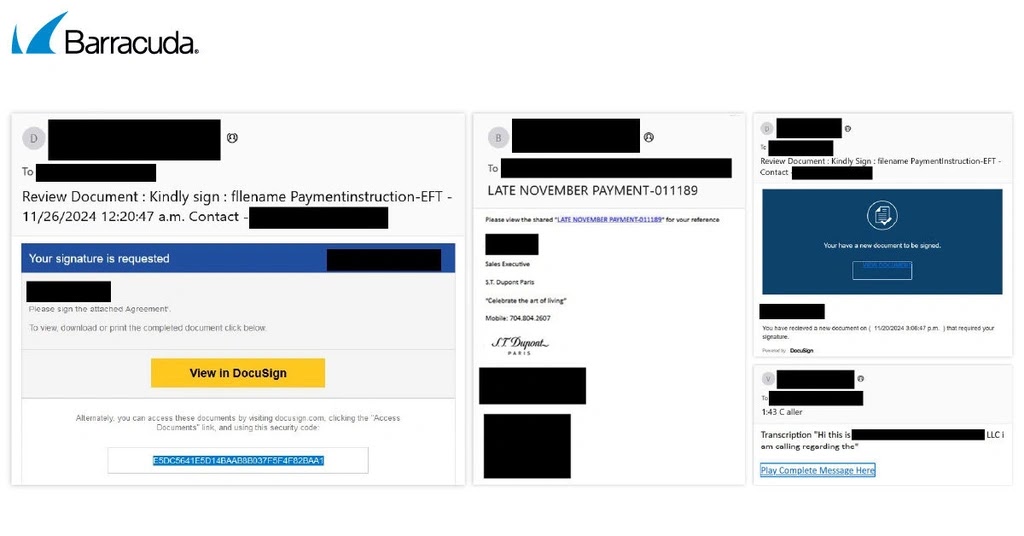
This tactic significantly improves evasion, as emails from verified accounts are less likely to trigger suspicion or be flagged by automated systems.
Major updates to Tycoon 2FA’s phishing pages include changes to the source code that hinder traditional web page analysis.
Unlike earlier versions that called external JavaScript resources and stylesheets, the latest version employs embedded, obstructive scripts to complicate manual inspection.
Additionally, Tycoon 2FA incorporates mechanisms to detect and block automated security scripts and tools, such as the popular Burp Suite.
If such tools are identified, the platform redirects users to a blank page, effectively preventing further analysis.
Another advanced feature in Tycoon 2FA is its ability to monitor keyboard inputs for common shortcuts used by security professionals to inspect web pages.
Key combinations like “Ctrl+Shift+I” or F12 are blocked, rendering developer tools inaccessible.
According to Barracuda threat analysts, in some variants, shortcuts are replaced with their ASCII decimal values for enhanced obfuscation.
If developer tools are detected, the software delays page loading, and if the delay exceeds predefined thresholds, the page redirects to a legitimate site, such as OneDrive, further obfuscating malicious intent.
Disruption Techniques and Obfuscation Strategies
Tycoon 2FA’s latest version disables key web functionalities, such as the right-click context menu, to prevent users from inspecting or saving page elements.
It also employs code obfuscation, making the underlying phishing scripts more difficult to interpret.
Additionally, the platform blocks users from copying meaningful text by overwriting clipboard contents with pre-specified strings, hindering offline analysis and data extraction.
These measures demonstrate the proactive lengths phishing kit developers go to to derail security investigations.
As PhaaS platforms like Tycoon become more sophisticated, they expand the capabilities of even less-skilled attackers, making phishing a more pervasive and complex threat.
The ability of Tycoon 2FA to bypass 2FA protections and implement advanced detection evasion techniques underscores the need for robust security measures across organizations.
Barracuda and other cybersecurity firms continue to monitor and analyze these platforms to uncover their evolving tactics and develop countermeasures that can mitigate their impact.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar



.png
)
