A critical security vulnerability, CVE-2025-31125, has been identified in the Vite development server.
Due to improper path verification during URL request processing, attackers can bypass path restrictions and gain unauthorized access to arbitrary files on affected servers.
This flaw is particularly concerning as it can be exploited by unauthenticated attackers, leaving sensitive data at risk.
The vulnerability impacts users who expose their Vite development server to the network (e.g., by enabling –host or modifying server.host).
Publicly available proof-of-concept (PoC) exploits for CVE-2025-31125 have heightened the urgency for immediate mitigation.
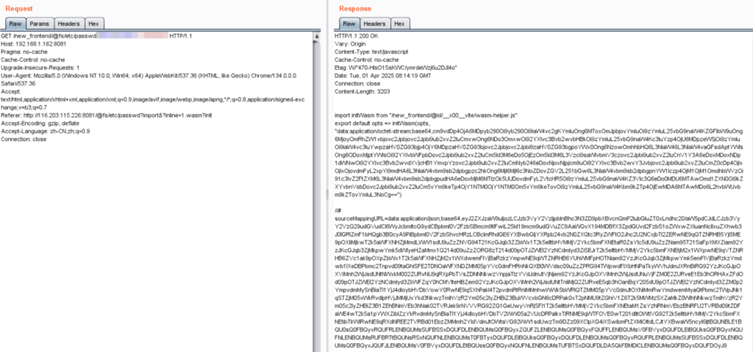
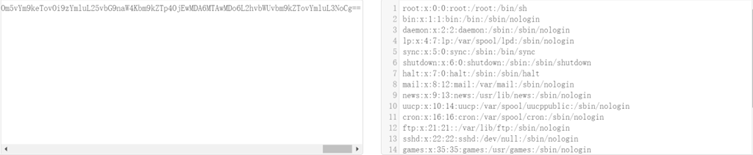
NSFOCUS CERT has verified and reproduced the vulnerability and is urging users to take quick action to secure their systems.
CVE-2025-31125: Affected Products
The following table outlines which Vite versions are vulnerable and the unaffected (patched) versions available:
| Affected Versions | Unaffected Versions (Patched) |
| 6.2.0 ≤ Vite ≤ 6.2.3 | Vite ≥ 6.2.4 |
| 6.1.0 ≤ Vite ≤ 6.1.2 | 6.1.3 ≤ Vite < 6.2.0 |
| 6.0.0 ≤ Vite ≤ 6.0.12 | 6.0.13 ≤ Vite < 6.1.0 |
| 5.0.0 ≤ Vite ≤ 5.4.15 | 5.4.16 ≤ Vite < 6.0.0 |
| Vite ≤ 4.5.10 | 4.5.11 ≤ Vite < 5.0.0 |
Detection Methods
Manual Detection
To determine if your system is affected, use the following commands:
- Check the global installation with npm:
npm list --global vite - Verify the version directly using the vite -v command in the terminal.
Automated Detection
For enterprise users, NSFOCUS offers tools to detect this vulnerability:
- EZ Automated Penetration Testing Tool:
- Detects Vite fingerprints and CVE-2025-31125 vulnerability risks.
- Example command:
./ez webscan –pocs vite -u https://192.168.1.41:443/ - Download here.
- Remote Security Assessment System (RSAS): Scans for CVE-2025-31125. Ensure updated plug-in packages.
Mitigation
The Vite team has released patched versions. Affected users are strongly advised to update to one of the unaffected versions listed above.
If upgrading immediately is not feasible, limit access to the Vite development server by implementing network restrictions while maintaining core functionality.
Organizations using NSFOCUS External Attack Surface Management Service (EASM) can assess Internet-facing assets and mitigate risks. Additionally, NSFOCUS’s CTEM solution supports active identification of vulnerable Vite development servers.
Security teams must act quickly to address CVE-2025-31125, as public PoCs and the nature of the exploit increase the chances of real-world attacks.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!



.png
)
