A cybersecurity researcher has demonstrated a method to bypass BitLocker encryption on Windows 11 (version 24H2) by extracting full volume encryption keys (FVEK) from memory.
Using a custom-built tool named Memory-Dump-UEFI, the researcher was able to retrieve sensitive cryptographic keys to decrypt a BitLocker-protected partition.
BitLocker, Microsoft’s full-disk encryption system, is designed to protect data by encrypting the entire volume of a device.
It is especially crucial for safeguarding sensitive information in enterprise environments. However, its security relies heavily on preventing unauthorized access to the encryption keys.
The method used in the demonstration exploits a common weakness: the residual data stored in RAM.
When a device is abruptly restarted, its RAM contents may remain intact for a short period. By leveraging this time window, an attacker can extract sensitive data stored in memory, including encryption keys.
The demonstration highlights several advanced methods to mitigate memory degradation, including techniques like physically cooling RAM modules or maintaining power to prevent data decay.
Bypassing BitLocker: Demonstration of the Attack
The researcher carefully outlined the steps to bypass BitLocker encryption. Here’s the summarized process:
- Preparing a Bootable USB Tool
A USB storage device larger than the system’s RAM was prepared using a script provided by the research tool. - Restarting the Target System
By shorting the reset pins on the motherboard, the researcher forced an abrupt restart of the system while preserving power to the RAM. This ensured minimal data degradation. - Dumping Memory Data
The system was booted using the USB device, launching the Memory-Dump-UEFI tool. This program dumped the contents of the RAM into files for further analysis. - Analyzing Memory Dumps
Using tools such as concatDumps and xxd, the researcher analyzed the memory dumps. Key cryptographic data, including FVEK, was located by identifying specific memory pool tags such as dFVE (allocated by dumpfve.sys).
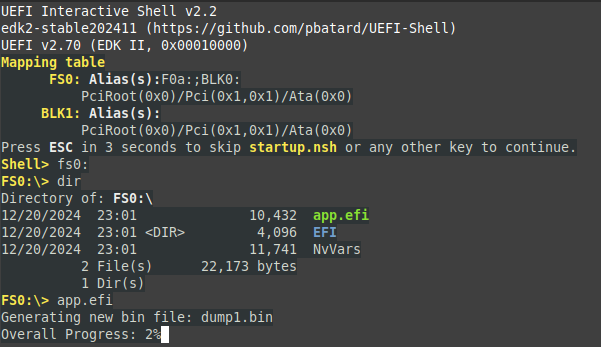
The FVEK keys were traced to specific memory pools, with one consistent recovery location marked by the dFVE pool tag.
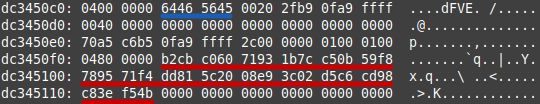
The keys were extracted in hexadecimal format and prepped for decryption by appending metadata about the encryption algorithm, such as XTS-AES-128. Using tools like Dislocker, the researcher successfully unlocked the encrypted volume.
According to the NoInitRD, this research underscores a critical vulnerability in systems where attackers can gain physical access.
While Microsoft has incorporated measures to overwrite sensitive data, some keys persist in memory and can be extracted under the right circumstances.
- Enable Device Lockdown: Ensure devices are secured in tamper-proof environments to prevent unauthorized physical access.
- Configure BitLocker with TPM: A Trusted Platform Module (TPM) adds a layer of hardware-based security, reducing the risk of key theft.
- Rapid Shutdown Protocols: Emphasize complete power-off mechanisms to clear RAM.
- Educate Users: Organizations should train employees on best security practices, especially regarding physical device security.
This revelation serves as a reminder that even sophisticated encryption systems like BitLocker can be vulnerable under specific attack conditions. Microsoft is expected to investigate these findings and improve BitLocker’s resilience.
Investigate Real-World Malicious Links, Malware & Phishing Attacks With ANY.RUN – Try for Free



.png
)
