Cybersecurity experts have uncovered a sophisticated phishing campaign targeting Microsoft advertising accounts.
The attack, orchestrated through malicious Google Ads, aims to steal login credentials of users accessing Microsoft’s advertising platform.
This incident highlights the growing risk of malvertising, where cybercriminals exploit legitimate ad networks to deceive users.
How the Attack Works
The phishing campaign leverages sponsored Google search results for terms like “Microsoft Ads” and “Bing Ads.”

While Microsoft does purchase ad space on Google to attract advertisers, threat actors have inserted fake sponsored links mimicking legitimate Microsoft domains.
These malicious ads bypassed Google’s security protocols, directing unsuspecting users to fraudulent login pages.
Upon clicking the malicious ad, users are redirected through a complex network of cloaking techniques.
The attackers differentiate genuine users from bots or web crawlers, directing suspicious traffic to harmless “white pages.”
Real users, however, are funneled through a Cloudflare verification checkpoint, which uses legitimate infrastructure to validate their authenticity.
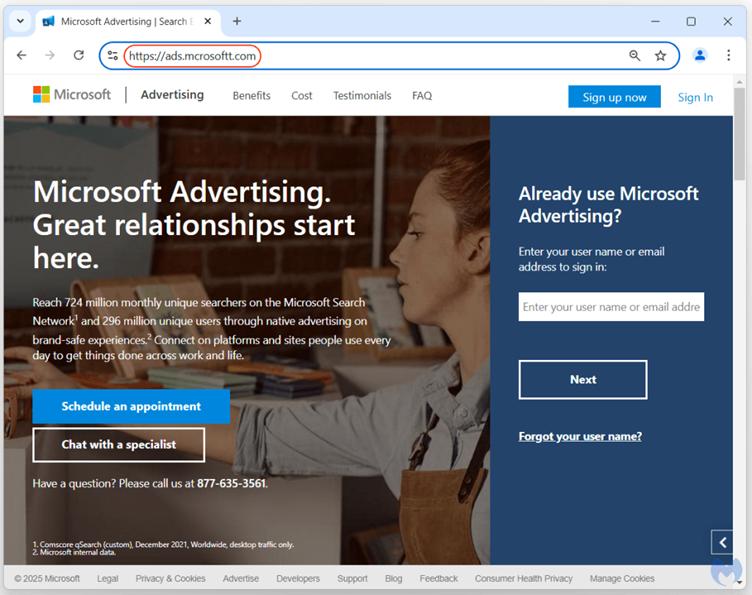
Once verified, users face phishing pages designed to replicate Microsoft’s advertising login portals. These pages prompt users to reset passwords, inadvertently handing over sensitive information to the attackers.
Some phishing kits used in this campaign even attempt to bypass two-factor authentication (2FA), a troubling insight into the evolving sophistication of phishing tactics.
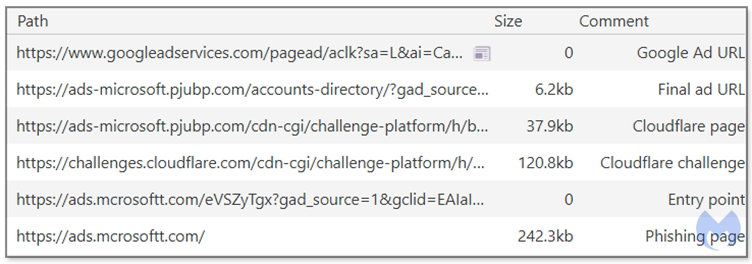
The Scope of the Attack
Evidence suggests this campaign may have been active for years, with links to domains hosted in Brazil and other regions.
According to the Malwarebytes report, Cybersecurity researchers identified a broad infrastructure supporting the phishing operation, pointing to a large-scale attack targeting advertisers on Microsoft and possibly other platforms like Google and Facebook.
The attackers used URLs mimicking Microsoft’s domains, with slight misspellings or substitutions, such as “ads.microsoftt[.]com” or “ads-mlcrosoft[.]com.”
The scale and persistence of the campaign indicate that significant resources have been invested, and the attack might only reveal the “tip of the iceberg.”
The attack comes as Microsoft’s advertising business, including Bing, experiences increasing competition from Google.
In 2023, Microsoft generated $12.2 billion from search and news advertising, a fraction of Google’s market dominance.
With malicious actors infiltrating a space already marked by rivalry, both companies face scrutiny over their security measures to protect advertisers. The incident underscores vulnerabilities in online advertising systems.
Google and Microsoft have been informed of the breaches, but the campaign raises concerns about the robustness of ad network security protocols and the risks they pose to users who trust these platforms.
Here are some key steps advertisers and users can take to stay safe:
- Verify URLs: Always double-check the website address for slight misspellings or inconsistencies before entering credentials.
- Be Cautious with 2FA Requests: While 2FA is essential, users must scrutinize all access requests to ensure they’re legitimate.
- Monitor Accounts Regularly: Watch for unauthorized activity or unexpected changes in account settings.
- Report Suspicious Ads: If encountering fraudulent ads, report them to the platform to help protect others.
This attack underscores the critical need for vigilance in digital advertising. As cybercriminals develop increasingly sophisticated tactics, businesses and users alike must adopt robust security practices.
While companies like Google and Microsoft work to enhance their defenses, staying educated and cautious remains one of the best lines of defense against such threats.
Are you from SOC/DFIR Teams? – Analyse Malware Files & Links with ANY.RUN Sandox -> Start Now for Free.



.png
)
