A new variant of the WhiteSnake Stealer, a formidable malware that has been updated to be more elusive and efficient in its malicious endeavors.
One of the key features of the updated WhiteSnake Stealer is its use of mutexes (mutual exclusions).
Mutexes are a common programming practice to prevent the same program from being launched multiple times, which can lead to system instability or make the malware more detectable.
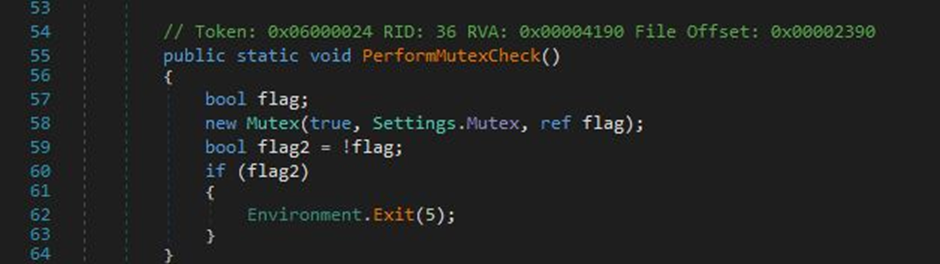
Upon execution, the stealer checks for a specific mutex value predefined in its configuration file.
If this mutex is already present on the system, indicating that an instance of the stealer is running, the newly executed stealer will terminate itself.
This ensures that only one instance of the malware operates at a time, reducing the risk of detection and system resource exhaustion.
Anti-VM Detection to Evade Analysis
Another layer of stealth is the AntiVM feature.
Free Webinar : Mitigating Vulnerability & 0-day Threats
Alert Fatigue that helps no one as security teams need to triage 100s of vulnerabilities.:
- The problem of vulnerability fatigue today
- Difference between CVSS-specific vulnerability vs risk-based vulnerability
- Evaluating vulnerabilities based on the business impact/risk
- Automation to reduce alert fatigue and enhance security posture significantly
AcuRisQ, that helps you to quantify risk accurately:
Security researchers often use virtual machines (VMs) to analyze malware behavior in a controlled environment.
To combat this, WhiteSnake Stealer can be configured to detect the presence of VMs and terminate itself if one is found.
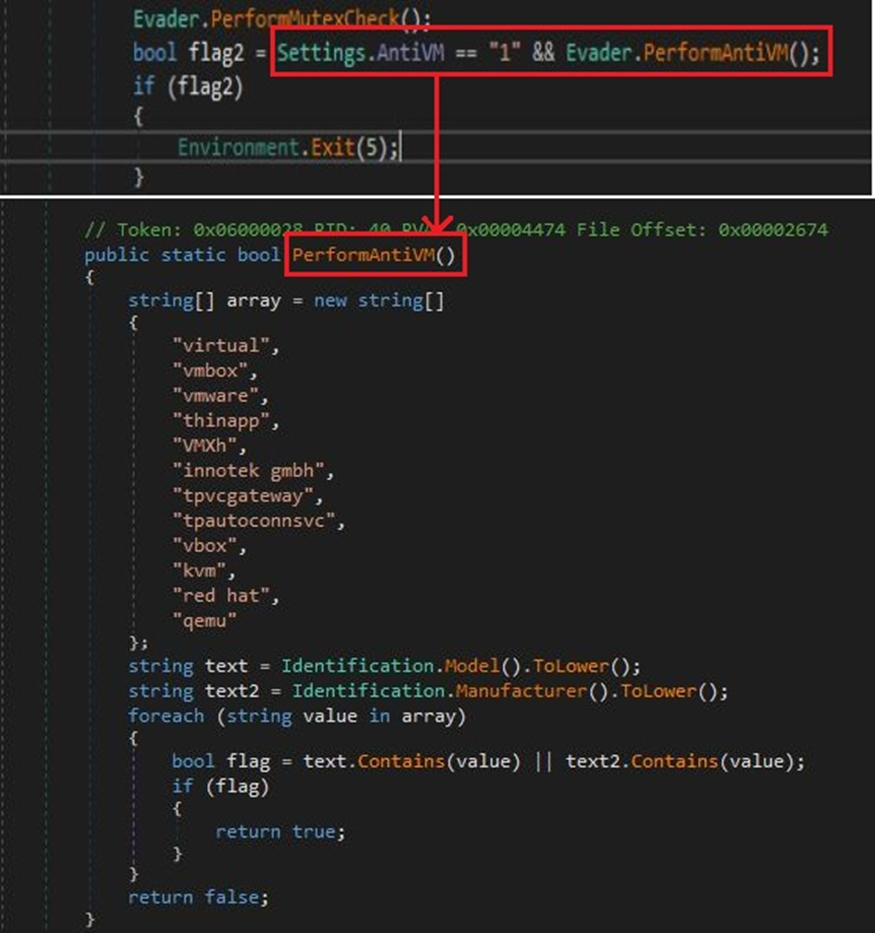
The stealer uses a WMI query to retrieve the computer system’s “Model” and “Manufacturer” properties.
It then searches for strings that are typically associated with virtual environments, such as “VMware,” “virtual,” and “qemu.”
If any of these strings are detected, the stealer will exit, thwarting any attempt to analyze or reverse-engineer its code.
According to the latest findings by SonicWall Capture Labs’ threat research team, WhiteSnake Stealer malware has emerged, showcasing less obfuscation and increased danger.
Advanced-Data Exfiltration Capabilities
Following the Anti-VM check, the malware proceeds to its primary function: data theft.
The Create() function is called, leading to the ProcessCommands() function, designed to siphon sensitive data from various sources.
The WhiteSnake Stealer targets a wide range of web browsers, including mainstream options like Google Chrome, Mozilla Firefox, and Microsoft Edge, as well as less common ones like Vivaldi and CocCoc Browser.
It extracts cookies, autofill information, login credentials, browsing history, and more.
In addition to web browser data, the stealer is programmed to target cryptocurrency wallets to capture the lucrative financial information associated with these assets.
The table below shows the targeted cryptocurrency wallets and browser extensions.
Cryptocurrency Wallets
| Cryptocurrency Wallet Name | Targeted Directory |
| Ledger | %AppData%\ledger live |
| Atomic | %AppData%\atomic\Local Storage\leveldb |
| Wasabi | %AppData%\WalletWasabi\Client\Wallets |
| Binance | %AppData%\Binance |
| Guarda | %AppData%\Guarda\Local Storage\leveldb |
| Coinomi | %LocalAppData%\Coinomi\Coinomi\wallets |
| Bitcoin | %AppData%\Bitcoin\wallets |
| Electrum | %AppData%\Electrum\wallets |
| Electrum-LTC | %AppData%\Electrum-LTC\wallets |
| Zcash | %AppData%\Zcash |
| Exodus | %AppData%\Exodus |
| JaxxLiberty | %AppData%\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb |
| JaxxClassic | %AppData%\Jaxx\Local Storage\leveldb |
| Monero | %UserProfile%\Documents\Monero\wallets |
Targeted Cryptocurrency Wallets
Beyond its sophisticated evasion techniques, WhiteSnake Stealer boasts a range of functionalities designed to harvest sensitive data from infected systems.
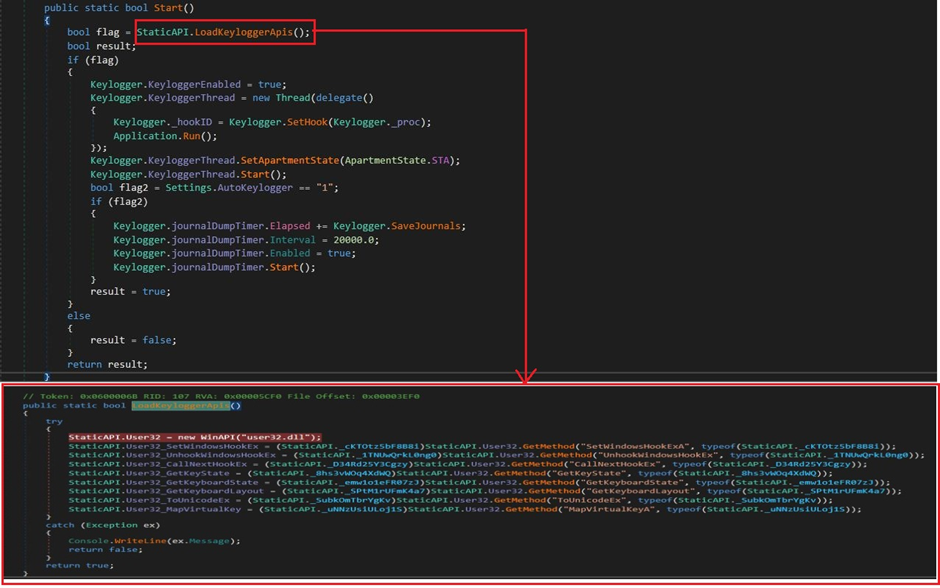
While keylogging is disabled by default, attackers can activate this feature remotely and capture every keystroke of the victim.
Moreover, the malware can hijack the victim’s microphone and webcam, turning personal devices into surveillance tools.
The new variant of WhiteSnake Stealer demonstrates the continuous innovation by cybercriminals to bypass security measures and remain undetected.
Implementing mutexes and anti-VM techniques, along with its comprehensive data theft capabilities, make it a significant threat to users and organizations.
As the cyber threat landscape evolves, it is crucial for cybersecurity professionals and end-users to stay informed about the latest malware trends and to implement robust security measures to protect sensitive information.
Stay updated on Cybersecurity news, Whitepapers, and Infographics. Follow us on LinkedIn & Twitter.
.webp?w=696&resize=696,0&ssl=1)


.png
)
