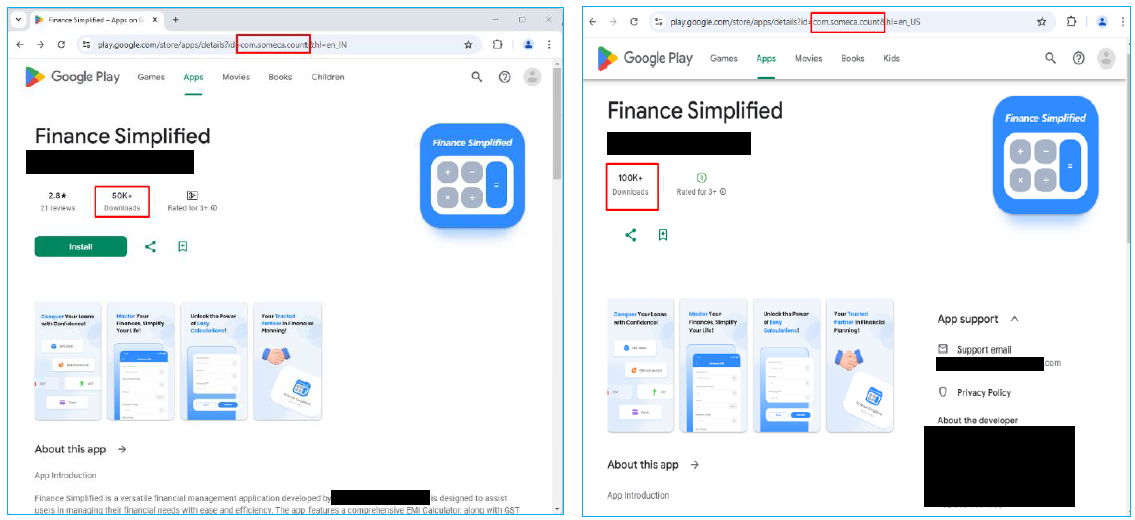
A malicious Android application, Finance Simplified (package: com.someca.count), has been identified on the Google Play Store, targeting Indian users under the guise of a financial management tool.
The app, which claims to offer an EMI calculator, is instead a sophisticated malware platform facilitating predatory lending, data theft, and extortion.
Rapid Spread and Exploitative Practices
The app has seen a sharp rise in downloads, surging from 50,000 to 100,000 installations in just one week.
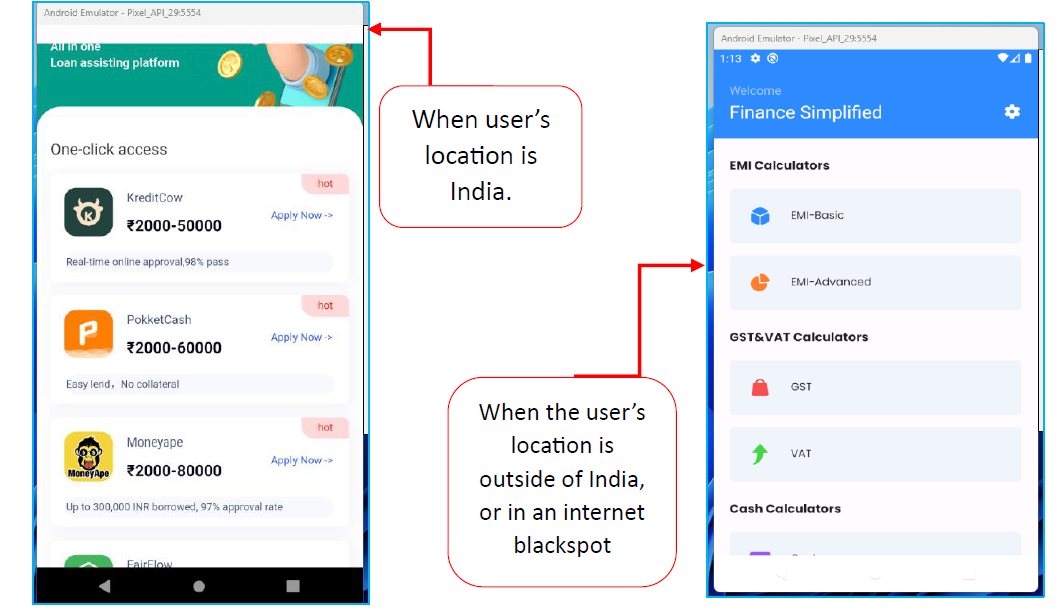
Once installed, it leverages location-based targeting to display unauthorized loan applications through WebView.
These apps redirect users to external websites that bypass Google Play’s security mechanisms by hosting APK files on external servers.
Victims are coerced into exploitative loan agreements and subjected to harassment through blackmail tactics, including the creation of deepfake images using their personal photos.
Technical Mechanisms and Data Breaches
The app requests excessive permissions, including access to location data, contacts, call logs, SMS messages, clipboard content, and external storage.
It silently collects sensitive information such as passwords, credit card details, and private messages.
This data is transmitted to a command-and-control (C2) server hosted on Amazon EC2 infrastructure.
The admin panel of this server supports both English and Chinese languages, suggesting potential involvement of Chinese-speaking attackers.
Key features of the app’s malicious activities include:
- Dynamic WebView Manipulation: Injecting JavaScript code to display fake loan applications tailored to the user’s location.
- Persistent Data Harvesting: Capturing clipboard entries, tracking call logs, extracting contact details (including emails and phone numbers), and monitoring SMS communications.
- Blackmail Tactics: Editing user photos into fake nude images for extortion purposes.
Cyfirma investigation revealed that Finance Simplified is part of a larger network of fraudulent apps such as KreditApple, MoneyAPE, StashFur, and PokketMe.
These apps share similar interfaces and privacy policies while claiming registration with Indian financial regulators, a claim proven false by their removal from the Play Store for fraudulent activities.
These apps utilize misleading tactics like dynamic privacy policies hosted on external URLs that can be altered post-installation without user knowledge.
This enables attackers to inject harmful updates or redirect users to phishing sites.
The emergence of apps like Finance Simplified underscores the growing sophistication of cybercriminals exploiting mobile platforms.
Users are advised to scrutinize app permissions carefully and avoid downloading applications from unverified sources even from official platforms like Google Play Store.
Organizations should implement robust endpoint security measures and collaborate with app marketplaces to identify and remove malicious apps promptly.
This case serves as a stark reminder of the critical need for heightened cybersecurity awareness in combating financial cybercrime in India and beyond.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here



.png
)
